Previous
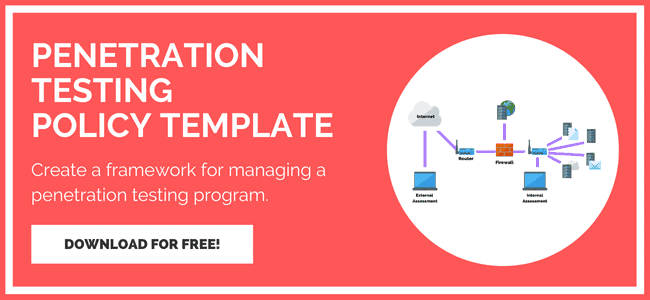
How To Create & Implement A Penetration Testing Policy
Assess and validate your security with PurpleSec’s penetration testing services.
Author: Jason Firch / Last Updated: 11/21/22
Reviewed By: Michael Swanagan, CISSP, CISA & Seth Kimmel, OSCP
View Our: Editorial Process
Table Of Contents
You can successfully implement a penetration testing policy by categorizing all systems and data, assigning roles and responsibilities, using relative risk scoring, defining communication channels, and regularly updating your policy as needed.
What You’ll Learn
- What a penetration testing policy is and why you need one.
- What you should include in a pen testing policy and how to write one.
- A sample penetration testing policy template you can use for your organization today.
- How PurpleSec drastically reduces cyber risk.
Penetration testing proactively tests an organization’s IT security resilience by simulating attacker behavior using known tactics, techniques, and procedures (TTP).
By simulating real-world cyber attacks, penetration testing provides a higher degree of security assurance than only relying on an automated scanning product to find exploitable vulnerabilities.
This article will provide an overview of why an organization may want – or even be required – to conduct regular penetration testing and also describe how to support penetration testing activities with formal policies.
Penetration testing policies help increase the effectiveness of a penetration testing program by supporting penetration testing best practices and ensuring that roles and responsibilities are clearly defined.
What Is A Penetration Testing Policy?
A penetration testing policy is a set of formalized guidelines, requirements, and standard operating procedures that serve to define the overall goals, expectations, limits, and methods that an organization uses to govern penetration testing activities.
A penetration testing policy primarily outlines which types of penetration testing should take place and who is responsible for different aspects of an organization’s penetration testing program.
The policy should also clearly outline how communication should be handled between all stakeholders including managers, service providers, departments, and IT security teams.
A penetration testing policy helps ensure that pen testing program activities happen in a reliable manner and reports can effectively facilitate the remediation of any security gaps discovered.
In situations where penetration testing is conducted to satisfy regulations or meet industry standards, a penetration testing policy helps ensure compliance.
Why Do You Need A Policy For Penetration Testing?
Cyber-attacks have been increasing in frequency and severity.
Cyber security statistics show a sharp increase in the frequency and cost of cyber attacks over recent years and this trend is expected to increase.
Ransomware attacks – the apex cyber threat – cost an average of $283,000 worth of downtime per incident in 2020, while attackers’ demands increased 82% year over year reaching an average of $570,000 USD in 2021.
Although fundamental vulnerability management activities such as scanning a network for misconfiguration and known vulnerabilities provide some degree of risk mitigation for an organization, pen testing activities can achieve an even higher degree of IT security risk assurance.
Without a formalized and systematic approach to advanced risk mitigation activities – including pen testing – it is impossible to ensure that risk mitigation has been conducted reliably.
Formal pen testing policies standardize processes by providing clear operating procedures that increase the effectiveness, efficiency, and reliability of the results that pen testing activities return.
Penetration testing policies clearly outline types of testing, schedules, scopes, and limitations of testing activities so that testers work in an organized and predictable way to achieve the intended goals.
Pen testing policies also delegate roles and responsibilities and define clear communication channels to ensure that testing results are properly disclosed in a timely manner and any security gaps are remediated.
This structured and reliable approach to pen testing operations results in a quantifiable reduction in cyber risk by testing an IT environment’s resilience against known real-world cyber attack strategies.
What Should A Penetration Testing Policy Include?
Penetration testing has different use cases depending on what type of IT environment an organization is seeking to secure.
Each organization can scope pen testing activities to include only a small subset of critical departments, assets, applications, or network segments.
Fundamentally a penetration testing policy should include a risk assessment of all assets, systems, and data, a schedule of pen testing activities, and detailed instructions about which types of testing should be done.
Because the goal of a penetration test is to simulate real-world cyber attacks, in most cases, a third-party service provider will perform tests.
An organization’s pen testing policy should explicitly name those partner service providers and include input from service providers.
In this way, a pen testing policy can act as a service level agreement (SLA) to govern an organization’s expectations from service providers.
At a minimum, a penetration testing policy should include:
- A description of the most fundamental goals of the penetration testing program.
- A description of any legal or formal compliance requirements.
- Designation of critical roles and responsibilities for all pen testing activities.
- Communication and reporting channels that govern the penetration testing program.
- A description of the types of penetration testing that will be conducted.
- The general scopes and limitations that should be applied to all pen testing program activities.
How To Write A Penetration Testing Policy
Designing and implementing an effective penetration testing policy requires a process that can be summarized as follows:
- Build a comprehensive asset inventory of your organization’s entire IT environment.
- Develop risk management goals by categorizing all systems and data according to operational criticality, potential damages due to a cyber-breach, and applicable laws and regulations.
- Assign roles and responsibilities for internal staff and third-party service providers will provide penetration testing or related services.
- Use relative risk scores to determine which types of penetration testing activities, scopes, and limitations are appropriate to mitigate risk in line with risk management goals.
- Determine the most appropriate communication channels for documenting, monitoring, and reporting the results of penetration testing activities.
- Maintain, monitor, and update the penetration testing policy as needed.
The process should include consulting with trusted industry standards that define IT security best practices with respect to the data sensitivity, operational criticality, and the underlying infrastructure that the data resides on.
It’s important to note that penetration testing activities are continuously monitored to ensure that procedures are being properly followed.
Also, if changes are made to business operations or infrastructure, the penetration testing policy should be reevaluated and updated as required.
Wrapping Up
The cost of even a single data breach can be high and has been increasing exponentially in recent years.
Many organizations are actively seeking to extend their cybersecurity operations to include pen testing activities – authorized simulated cyber attacks on their own infrastructure.
By simulating real-world attacks using known attack TTP organization’s can achieve a higher degree of assurance that an IT environment is resilient.
A formally documented pen testing policy clearly outlines the goals, activities, schedules, requirements, roles and responsibilities, scopes, and limitations; allowing the organization to extract greater value from its pen testing operations.
Organizations don’t need to start from scratch either. Pentesting policy templates already exist that can jump-start efforts to create a policy and make the transition smoother.

Jason Firch
Jason is a proven marketing leader, veteran IT operations manager, and cyber security enthusiast with 10 years of experience. He is the co-founder and CEO/CMO of PurpleSec.
Recent Articles
- Why Automation Is The Future Of Penetration Testing
- Continuous Penetration Testing: How To Lower Costs & Improve Security
- What Is Cloud Penetration Testing? (& When Do You Need It?)
- How To Create & Implement A Penetration Testing Policy
- White Box Penetration Testing: When Do You Need One?
- View All Resources
Categories
Policy Templates
Most Popular