Kaseya VSA Ransomware Attack Explained
Contents
Kaseya suffered one of the largest ransomware attacks in history impacting up to 1500 companies along with a staggering ransom note of $70 million.
We’ll cover the ransomware terms, the method and indicator of compromises of the attack, and how Kaseya is responding.
Stay Up-To-Date On The Latest Attacks
Be the first to know when our experts release new insights on the top attacks.
You're on the list! Just one more step...
Check your email to confirm your subscription.
What Is Kaseya And Why Do Businesses Use It?
Kaseya VSA is a remote monitoring and management (RMM) platform. It’s used by MSPs managed services providers (MSPs), which perform IT functions such as email, phone systems, firewalls, switches, and other networking equipment.
The RMM agent is installed on endpoints on client workstations and servers. The purpose, like most software, is to streamline IT operations for MSPs by centralizing all of the management and monitoring of those platforms.
This includes everything from asset tracking, software monitoring, and warranties on a particular PC.
Who Was Impacted By The Kasyea Attack?
The Kaseya ransomware attack has impacted over 50 MSPs and between 800 and 1500 companies. For context, this represents a total of 37,000 of Kaseya’s clients or 0.001% of their total customer base.
An MSP has a number of companies that they service and if one MSP is breached it’s a downstream effect impacting all of their clients.
Kaseya has pushed the narrative that it is only a small percentage of their client base has been impacted, which is true.
However, even though it’s a small percentage there is potential for this attack to widen.
We’ve learned throughout these breach reports that it can take several weeks to months for the full implications of an attack to surface. 50 impacted MSPs could turn into hundreds.
Those 1500 companies impacted could turn into 3000.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

Who Is Responsible For The Kaseya Attack?
REvil, a ransomware-as-a-Service (RaaS) gang, also known as Sodinokibi, is behind the Kasyea ransomware attack.
They’re a full-fledged black hat red team operator. RaaS gangs sell their expertise to anybody who wants to ransom an organization for any purpose. This is typically driven by financial motivation.
REvil is known to conduct its own campaigns in addition to selling ransomware services. In total, this gang is responsible for more than 300 ransomware campaigns per month.
According to KPN, who tracks REvil’s activities, the gang has been increasing the number of their operations.
What Types Of Organizations Does REvil Target?
REvil has targeted major corporations such as JBS Meats, Quanta, and HX5.
However, those aren’t their only targets. REvil has also gone after childcare centers, dentists’ offices, beauticians.
Their goal is to target industries that are not known for robust security practices, while also looking for opportunities to spread to anyone who’s relying upon their IT infrastructure.
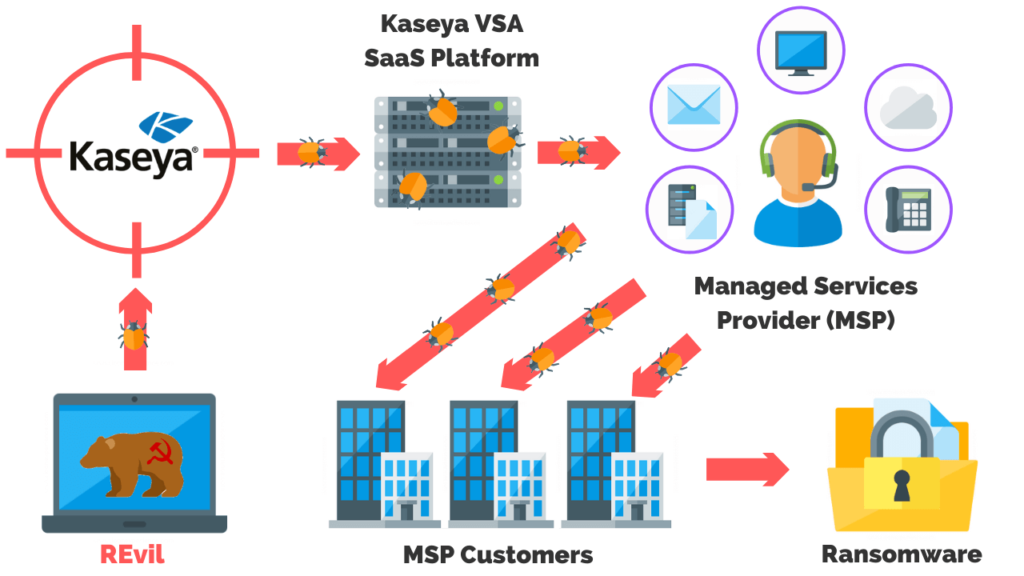
How Did The Kaseya Ransomware Attack Happen?
REvil attacked Kaseya’s VSA SaaS platform using zero-day exploits to gain access and distribute malicious software to their customers and their systems.
From there, the ransomware gang began using weaknesses on those systems to encrypt everything.
The Kaseya VSA agent (C:\PROGRAM FILES (X86)\KASEYA\<ID>\AGENTMON.EXE) is deployed to Kaseya’s customers (MSPs) and then deployed to the MSP customer’s systems.
This agent is responsible for pulling from Kaseya servers, which are hosted in the cloud.
Since the malware is already wrapped in the platform, it’s been signed by Kaseya’s platform. As a result, the malware is getting past everything on these client’s systems. To casual observers, it looks like legitimate Kaseya traffic when it’s actually installers for malware.
What Does It Mean To Sign The Malware?
Signing the malware is an evasion technique used by threat actors to get around security controls.
For example, drivers from Microsoft are digitally signed and are assumed to be a trusted software.
You may have seen alerts in the past on your computer saying they’re not from a trusted publisher when you go to install the software. In this case, it’s the user’s responsibility to confirm the software is legitimate.
Endpoint protection response, and other security monitoring tools, also look for a signed publisher executable. If the tool believes the software to be legitimate, or it has been configured by a security analyst to allow the activity, then it will allow the software to execute and install.
What Are The Indicators Of Compromise?
- 35.226.94[.]113
- 161.35.239[.]148
- 162.253.124[.]162
| Filename | MD5 Hash | Function |
|---|---|---|
| cert.exe | Legitimate File with random string appended | Legit certutil.exe Utility |
| agent.crt | 939aae3cc456de8964cb182c75a5f8cc | Encoded malicious content |
| agent.exe | 561cffbaba71a6e8cc1cdceda990ead4 | Decoded contents of agent.crt |
| mpsvc.dll | a47cf00aedf769d60d58bfe00c0b5421 | Ransomware Payload |
- POST /dl.asp curl/7.69.1
- GET /done.asp curl/7.69.1
- POST /cgi-bin/KUpload.dll curl/7.69.1
- GET /done.asp curl/7.69.1
- POST /cgi-bin/KUpload.dll curl/7.69.1
- POST /userFilterTableRpt.asp curl/7.69.1
Kaseya Vs Solarwinds Attack: What's The Difference?
Similar to Kaseya, SolarWinds was a supply chain attack. The main difference is that SolarWinds builds security products and delivers them directly to their customers. In the case of SolarWinds, the attack was on the security product’s code itself.
Nobelium, the threat actor group behind the attack, modified SolarWind’s product with malicious code.
With Kaseya, REvil moved further left in the DevOps chain or further up in the logistical chain attacking Kaseya themselves. When Kaseya’s MSP customers were compromised so were the customers of those MSPs.
Unlike the SolarWinds attack, the Kaseya attack comes from two layers of trust as well in terms of the end client.
In addition, REvil didn’t compromise Kaseya’s code and the company themselves were careful to point out that their code was not compromised.
It was Kasyea’s platform that delivered their agents and their code that was compromised and used to deliver the ransomware.
What Are The Ransomware Payment Terms?
Each customer is being asked to pay a ransom of between $50,000 and $5 million. However, there is also a $70 million master key available as a bundled deal paid in Bitcoin.
REvil’s ransom note:
Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities – nobody will not cooperate with us. Its not in our interests. If you will not cooperate with our service –for us, its does not matter. But you will lose your time and data, cause just we have the private key. In practice – time is much more valuable than money.
Is This The Biggest Ransomware Attack In History?
Three factors are used to define the criteria of the “biggest” ransomware attack including:
- Ransom demand
- Number of systems impacted
- Total damage caused
While the WannaCry is the largest ransomware attack by the number of systems infected, 230,000 computers over 150 countries, the total ransom was only $130,000.
Some security experts estimate the total impact of the WannaCry attack is between $100s of millions to $4 billion.
However, Kaseya is the biggest ransomware attack by ransom demand at $70 million as of July 23, 2021.
Should Companies Pay The Ransom?
No, do not pay the ransom. Here are a few reasons why.
First, the United States government has equated ransomware attacks to terrorism activities. While companies who pay the ransom may not be legally liable now, it is possible that the government will enact new legislation to deter this behavior.
Second, paying the ransom does not guarantee that threat actors will unlock all of your systems or that you’ll reclaim all of your data. In addition, paying the ransom paints you as a future target as threat actors know you are willing and able to pay.
Third, paying the ransom helps to fund these activities. Threat actors use these funds to reinvest into their infrastructure, obtain zero-day exploits, and hire top-tier threat researchers.
In most cases, these researchers have no idea what they’re working on or that their work will be used for malicious purposes.
How Has Kaseya Responded?
Kaseya shut down the Virtual System Administrator (VSA) SaaS platform to prevent malware from being delivered to its customers.
Next, they contacted the FBI and the CISA and engaged 3rd party vendors including Huntress and Sophos to help resolve this incident. In addition, the company has taken upon the responsibility of dissemination to all their customers.
The MSPs themselves should also be doing their due diligence of informing their customers of the attack. This should also include active threat hunting for the known indicators of compromise, which has been released by Kaseya.
How Can Companies Prevent Or Mitigate Ransomware Attacks?
Companies can prevent or mitigate ransomware attacks by:
- Implementing user education and training
- Automating backups
- Minimizing attack surfaces
- Creating an incident response plan
- Investing in an EDR tool and MDR
- Purchasing ransomware insurance
- Storing physical and offsite backups
- Implementing zero trust security
Backups are critically important both physical and off-site. Even if your company has cloud backups those can become infected as well. Having a business continuity plan and regularly testing your backups is one way to help mitigate these types of attacks.
Implement Zero-Trust
The best answer for preventing or mitigating a ransomware attack is implementing zero trust security.
While the security controls mentioned above are important, they all cost money, time, and resources. Security analysts are required to research and implement tools, configure them for the environment, and maintain those controls across different vendors.
From this perspective, companies are trying to prevent ransomware attacks by force.
Zero trust is different in that it treats everything as its own perimeter. It says the only thing, I, this piece of software, or this computer, or this user, is allowed to talk to is this user or computer or a piece of software.
In some cases, you change in what way they’re allowed to communicate with each other and what level of access they have when they do that communication.
Zero trust cuts back on the need for many of the tools mentioned above, especially throughout the institution, and helps to minimize the splash damage.
With this ransomware attack, we have a high-trust environment where the clients trust the MSPs, and the MSPs trust Kaseya because they’re all trusted vendors with each other.
Threat actors only need to attack the highest, most trusted vendor to reach companies downstream to be hit by that splash damage.
However, if the environment is zero trust, wherever that vector was that they got into your system and started ransoming it’s a very limited amount of space that they have to move.
What Should Companies Do If They’ve Been Impacted By Ransomware?
There are four steps that every organization should take if they’ve been impacted by ransomware:
- Isolate the impact
- Deploy your team
- Engage your backups
- Contact the FBI and CISA
First, isolate whatever has been impacted, but do not delete it as you will need it for forensic evidence. The purpose of isolation is to pull it off your network in order to stop it from communicating with anything else that’s uninfected.
Second, deploy your team to assess what’s going on whether it’s your managed security provider, a security operations center, or your internal security or IT personnel.
Regardless of the situation do not pay the ransom., as we’ve stated before.
Third, start engaging your backups. You should already have backups at this point and you need to look at replacing the systems that have been infected with new systems so your business operations can be up and running as soon as possible.
Fourth, continue to have your teams work on those isolated systems to pinpoint the cause of the attack.
Finally, contact the FBI immediately and inform the Cyber Information Security Agency (CISA). These agencies have the resources and manpower to help deal with ransomware attacks.
What Is The Current Status Of This Attack?
Update: As of 7/22/2021 Kaseya has obtained the master decryption key to unlock customer files.
Kaseya turned off delivery of the ransom and called the FBI. Kaseya’s CEO, Fred Voccola, is not commenting on if the ransom has been paid or how the decryption key was obtained.
In a quote, he states:
Will not comment on negotiating with terrorists.
Allegedly, REvil’s website has been shut down on their domain as of last week.
President Biden’s administration also told Putin that Russia must crackdown on cyber crime in that region.
What Does The Future Of Ransomware Attacks Look Like?
The Kaseya attack is a good indicator of the trend of threat actors attempting to gain higher trust. Supply chain attacks, not just from ransomware gangs, but from any supply chain attacks are the name of the game right now. The is because it maximizes the influence on systems that it impacts.
In 2021 REvil has already surpassed the money they’ve made in the first half of 2021 than they did the entire year prior. If you’re a business, that is an amazing story.
Simply put, supply chain attacks will continue to grow and ransomware will be the primary method used for threat actors to generate revenue.
Article by
Share This Article
Our Editorial Process
Our content goes through a rigorous approval process which is reviewed by cybersecurity experts – ensuring the quality and accuracy of information published.
Categories
The Breach Report
Our team of security researchers analyze recent cyber attacks, explain the impact, and provide actionable steps to keep you ahead of the trends.