Cyber attacks are becoming ever more pervasive in our daily lives. As a result, businesses must shift their mindset to monitoring these threats in real-time.
That’s where a Security Operations Center (SOC) comes into play.
Free IT Security Policies
Get a step ahead of your goals with our comprehensive templates.

In this article, I’ll share my 10+ years of professional experience leading a SOC team. First, I’ll discuss what a SOC is and the 3 main benefits of a modern-day SOC.
Then, I’ll dive into how a SOC works and the different types of SOC models. Finally, I’ll share the top best practices for running a successful SOC.
By the end, you’ll have all of the information you need to know on how SOCs help to prevent cyber attacks.
What Is A Security Operations Center?
There are two main definitions of a Security Operations Center (SOC).
The traditional definition of a SOC is a facility, place, or department that houses all of, or the primary core of, your business’s security operations.
What we mean by security operations is the continuous monitoring of a network, detection management, and incident response.
A modern SOC is a little different. Most of them you’ll still find in a facility or a building, but it doesn’t have to be quite that strict of a definition.
For instance, there are now virtual SOCs, such as a SOC as a service. I’ve found that you can run a SOC without a traditional on-site facility. This is true whether it’s an internal SOC or a Managed SOC.
This is because the core of a SOC is the team of security professionals whose sole aligned purpose is to meet a corporate or business security goal to manage, detect, and respond to cyber security risks.
24/7 SOCs today are more accessible than they were in the past, partly due to the meteoric rise of cloud services. Another reason has been the constant drive to push security down to smaller business models.
One thing that does not change, no matter the SOC architecture, is the primary purpose:
To be the neuro center of the organization’s security.
What Are The Types Of SOC Models?
The different types of SOC models include:
- Internal SOC
- Managed SOC (SOC as a Service)
- Co-Managed SOC
- Global SOC
Internal SOC
An internal SOC is a department of cyber security experts within an organization who fill many different roles of a SOC.
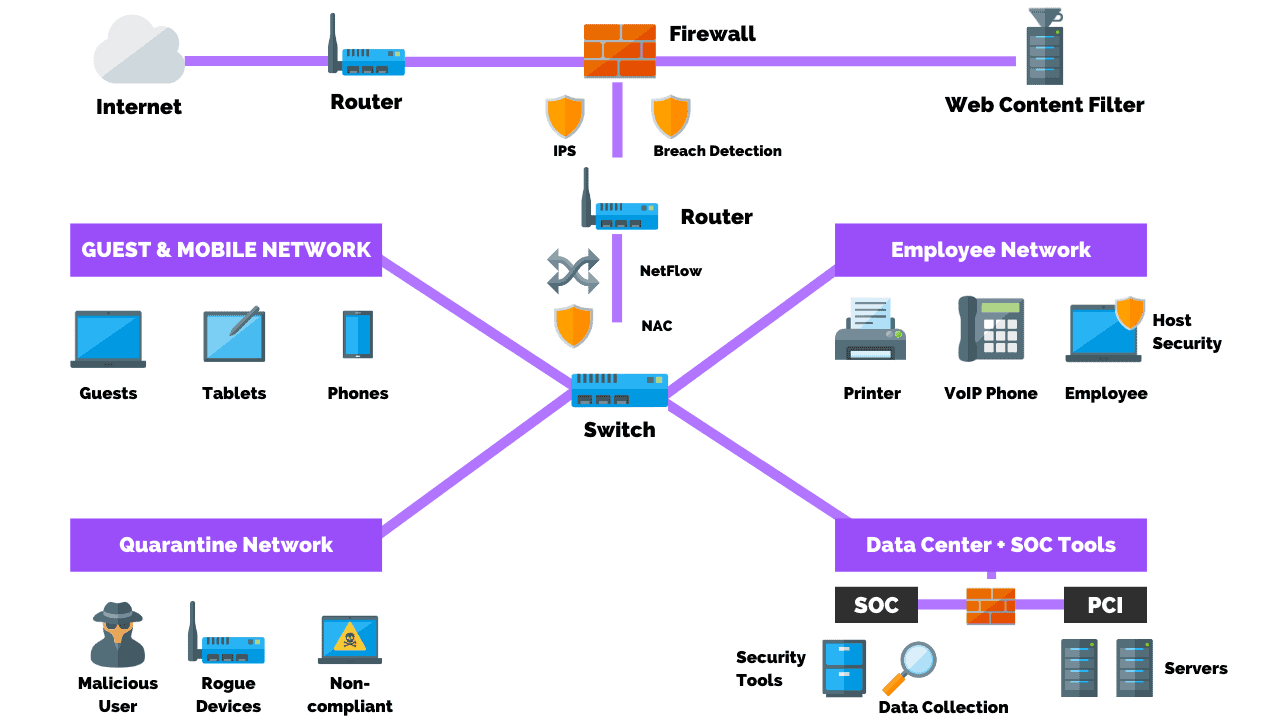
Generally, they’re going to be managing the corporate network and any internet presence they may have. They may or may not also be working on the development and product-type networks that reach out elsewhere.
Their job is to be the nerve center for security within the company. They are the managers of all the tools and agents that are deployed across the fleet.
They’re making sure they have visibility as systems get installed that come online, they can see them, scan them, inventory them, provide incident response on them, and run the tools for security on them as they require.
Creating that visibility, responding to those incidents, blocking things as need be, making sure that the IPS is updated, that they’re working, making sure that all the systems in the corporate network are updated and they have a lot of tools that give them these abilities.
For example, with SCCM you can manage many Windows systems. Corporate malware systems will have a host or server-based system so you can have one central security server and all the agents are deployed out across the fleet.
Read More: How To Prevent Ransomware Attacks: An Expert Guide
They can call back to this main server and that’s how you can manage everything.
So when I say it’s a nerve center, it really does kind of function like a brain.
The ultimate goal is to protect the crown jewels from unauthorized users.
For example, a crown jewel for a company may be its intellectual property. If it’s a factory that IP could be the production lines. If it’s an architecture shop, it’s their blueprints.
Those are the things that they’re really trying to primarily protect. And the way that you protect that is by securing everything else around them, which is the encompassing corporate network.
Managed SOC (SOC As A Service)
If you don’t want to build an internal SOC, because either you don’t have the budget, you don’t know how, or you’re a smaller business and it doesn’t make sense to invest in full-time employees and toolsets then you may look into a managed SOC or SOC as a service model.
A managed SOC functions the exact same way as an internal SOC. The main difference is that a managed SOC is usually larger because this is a company that’s selling this as a service.
So it can have more Capacity than a corporate SOC depending on how it’s built.
The other side is it’s less expensive. You don’t have to invest all that time into hiring and retaining talent as well as the cost of purchasing tools
Now, a difference comes into how that SOC gets its information and how it’s able to do the things that it can do within your network.
The typical model is to use appliances or agents similar to those used when building software or virtual machines, or a physical like rack appliance,
And this is all calling back to some kind of main SOC that this company runs and their employees have access to your information through these, these agents, through these appliances.
They’re actually the ones who are going to be maintaining the signatures, protecting the systems from things to the IPS systems, doing breach investigation reports, responding to incidents, and it works like any other “as a service” business model.
You can call if it’s an emergency, cause you’re under attack. There’s a button you can press to get through to somebody right away 24/7.
I can tell you from managing it from the inside, that it is like a beehive. It is just constant activity. Not always at the same spot. It kind of rolls around and there’ll be points in the day where half of the building feels like it’s dead because nothing’s really going on here.
But then over there, there’s some other kind of fire, but it just ebbs and flows just like the internet does. You’re kind of tuned into it. It’s really neat to be on that side of it to be ingesting it.
Co-Managed SOC
A co-managed SOC, while not common, can be found in some enterprises that maybe want to offload a certain aspect of the job to a managed SOC.
A company may want to keep all its data on-site, but they don’t want to write up all the reports and keep up to date on firewall signatures.
In this case, they may offload that task and others to a managed SOC provider. For example, the SOC provider can deploy an agent for devices connected to the network.
The internal team will work on all the data mining in Splunk Elastic Search, or whatever tool that they’re using.
Anything that deals with their attack surface will be offloaded to this SOC as a service.
Global SOC
A global SOC is a series of SOCs around the globe that are treated as individual facilities as nodes of a single major SOC. Global SOCs are typically used by the military or governments.
The advantage of a global SOC is that rather than have data streams and information come into one or two locations geographically, you can have your security expert sitting on top of the traffic, wherever it is in the world, manage it in near real time.
What Are The Benefits Of A SOC?
Having a SOC, a mature and properly configured SOC, keeps you agile in the security sense. This ensures you remain if not ahead of the game, then at least in the game of security.
Nothing is 100% effective, but a SOC allows you to respond quickly to get ahead of APTs and other threats to your business.
There are three main benefits of a SOC including:
- Centralizing the display of assets
- Collaborating across departments and functions
- Maximizing awareness to minimize costs
Centralizing Assets
A SOC helps centralize the management of your security and security assets in one place so that it’s not spread out across the whole organization.
Larger organizations typically have an internally managed SOC to:
- Perform incident response
- Monitor the fleet
- Be the main point of contact for audits
- Conduct vulnerability scans
- Conduct penetration tests
- Provide other security functions
Collaboration Across Departments
Collaboration across departments ensures that everyone is secure. You need someone to be the coach to bring everyone together to prevent siloed departments – especially in large organizations.
It’s also the job of a SOC to keep metrics of the security landscape within the organization and report that to the CIO.
This information is then brought forward to the C-Suite as a security breach has many monetary implications.
You can quantify risk in dollars because let’s say with a ransomware attack, we know generally how much that could cost an organization.
Any good company knows the worth of its intellectual property. So if that were to be attacked, you can put a dollar amount to that kind of a breach.
Maximizing Awareness
SOCs are also responsible for reporting pertinent information to key stakeholders and decision-makers to maximize awareness, thereby helping businesses to keep costs down.
Even though many will argue that the IT department is going to cost you money.
It’s true. There is an investment in that, but the reality is it’s always cheaper to run an IT department than it is to pay to access your encrypted assets.
When Do You Need A SOC?
If you do a lot of business and you have a large web presence, and if most of your shop, for example, is online, then it would be a good idea to have access to most of, if not all of, what a SOC can provide.
Of course, this is just the simple answer. The real answer, like many things in cyber security, is that it depends because implementing a SOC has to be worth it.
You have to have a web presence and have a lot of your business risk out there on the internet, or at least in the information systems that you have within your company.
You don’t necessarily have to always be on the internet, but when you have a large attack surface, you need a SOC to be able to react to it.
However, implementing a SOC is not really something you should do as a reaction. If you’re saying, “hey, we should get a SOC,” after you’ve been breached, then obviously it’s too late.
And that’s where the managed services come in for small to medium-sized businesses.
SOC For Small & Medium Companies
More and more every day, everyone needs the functions that a SOC can provide. And I say it that way because you may not necessarily get it from a SOC.
You can still get this through other means, but it typically requires a lot of your own management. This is where a SOC as a service comes in, especially with the medium and small business models.
It’s cheaper to pay using a monthly subscription model than it is to hire a whole department of employees, as well as purchase all the toolsets required.
Whereas that’s really been taken care of by a third party in these managed SOC and managed security service providers.
SOC For Enterprises
Enterprise organizations with thousands of employees and a national or global presence typically don’t subscribe to a third-party SOC.
This is because the overhead of the deployment needed to cover that organization is going to be so expensive and so cumbersome that it actually ends up being easier to build a SOC internally.
Enterprise businesses can benefit from a managed SOC, but it can be difficult to find a provider with the resources to satisfy security requirements in a way that works best for your enterprise.
Not to say it can’t be done, but you have to shop around. That’s why it’s a lot easier to build an internal team. While it’s very expensive it does give you a lot more control.
It keeps everything, such as your data, in-house, which a lot of people like because their data isn’t going anywhere else.
How Does A SOC Work?
A SOC works in 5 main ways:
- Get Visibility Of Information Systems
- Define Your Goals
- Monitor & Identify Traffic
- Respond To Cyber Attacks & Threats
- Report Findings To Stakeholders
1. Get Visibility Of Information Systems
Foremost a SOC needs to be able to see what’s going on in the information systems that they intend to protect. That’s really the most important thing. If you can’t see it, you can’t protect it. You can’t react to it.
2. Define Your Goals
Secondly, the most important thing after visibility is defining your goal. I don’t put that first because I really believe visibility is more important.
Even if you don’t have a goal, at least if you can see what’s going on, you’re doing something right.
But the goal is a really important part of creating, designing, or subscribing to, or deciding if you need a SOC. Furthermore, it addresses what the SOC is going to do.
The simple answer is that a SOC will keep you secure, but you need to break it down further.
If you’re running an internal SOC then you need to define its purpose such as:
- Blocking traffic/requests
- Monitoring systems
- Keeping ingress from the internet domain
- Protecting internal corporate systems
A company that serves a SOC as a service, typically for small to medium-sized companies, needs to define:
- Who are we servicing?
- Who are we selling to?
- How big of clients do we want to manage?
These are the kinds of things that you have to figure out in your goal of a SOC.
Overall, steps one and two can switch off. If you’re a managed service you need to know the goal. If you are an internal SOC, you need to take inventory of everything, you have figure it out and then decide what you’re going to do with it.
3. Monitor & Identify Traffic
Next, you need to equip yourself with the tools to do achieve your goals. Basic level one is monitoring and identification.
So for that, you’re going to need some kind of a monitoring system, like an intrusion detection system (IDS).
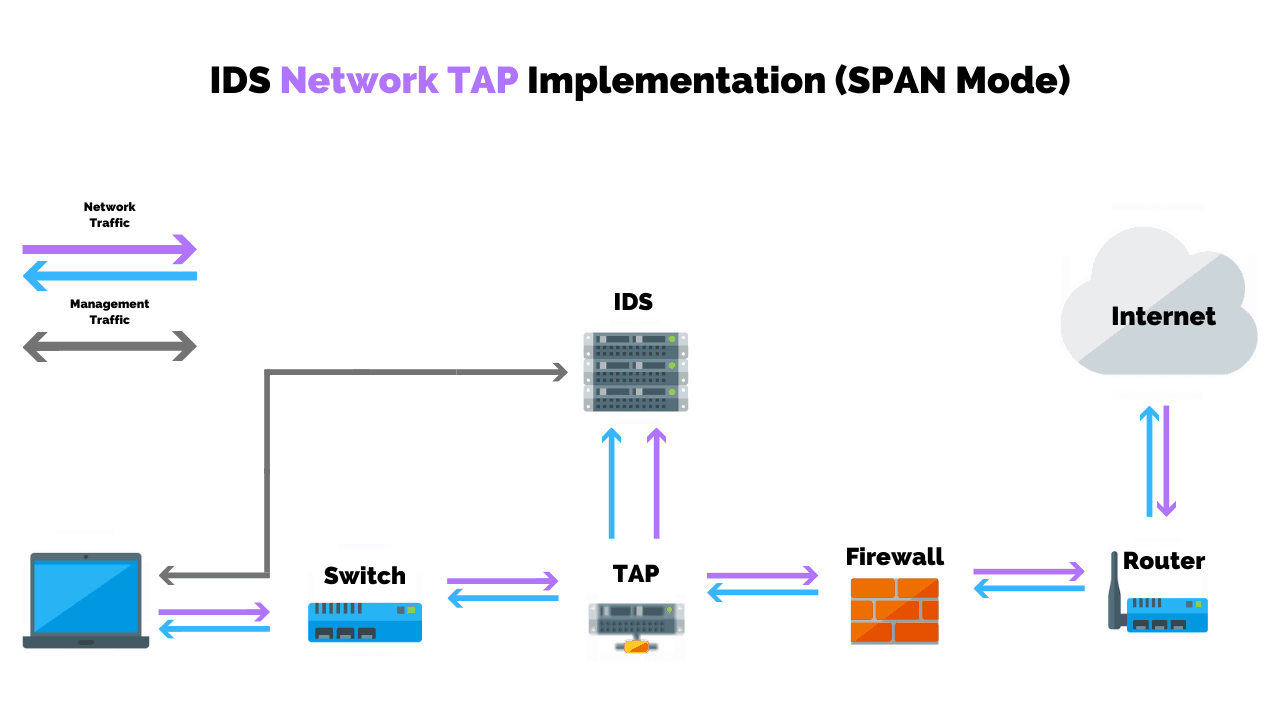
That could be one that sits on the network, looking at the enterprise assets internally. Or, it could be an IDS that is sitting between internet traffic and your web servers to see what’s going on from the internet zone inward.
This gives you visibility, but you also need somewhere to see that information, sort through that information, and understand that information.
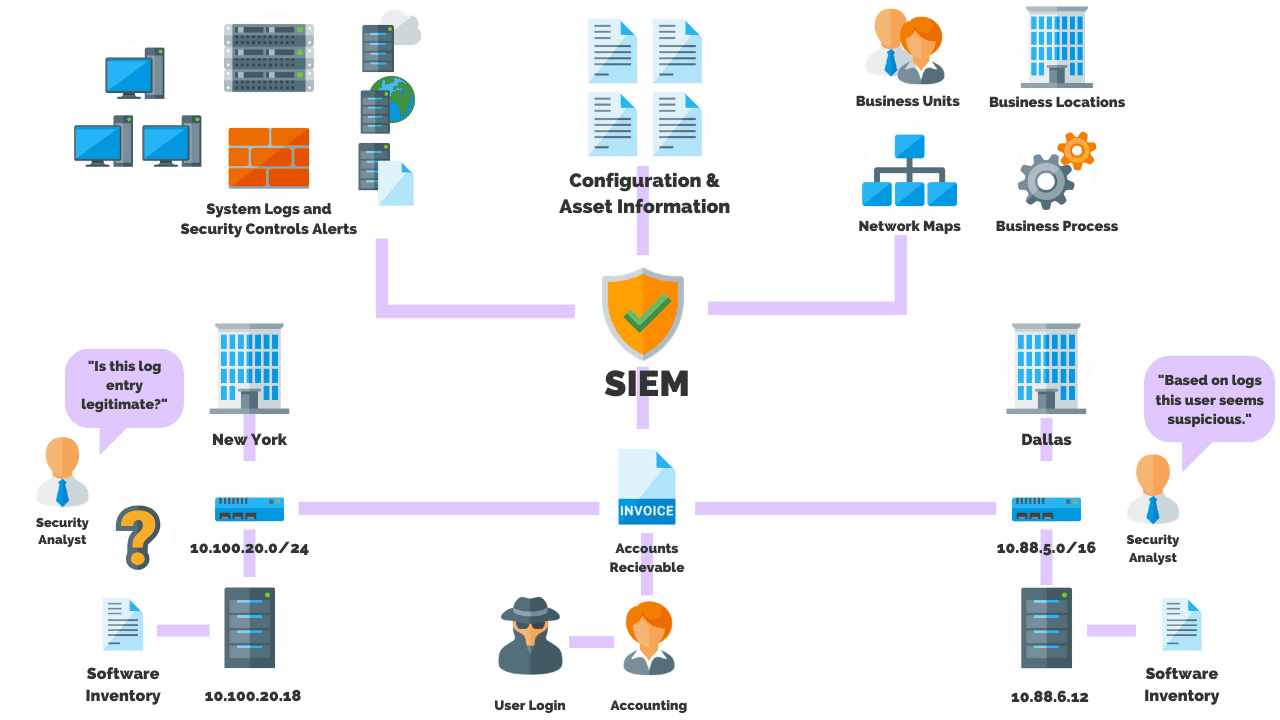
That’s where a SIEM solution, or security information and event management solution comes into play. Splunk and Elastic Search are good examples of this technology.
You can build a number of different types of SIEMs, but they all generally serve the same purpose of ingesting all that information from some kind of log source, like an IDS, and providing that data to analysts and security experts.
From there, security analysts have the ability to run searches, and filter results, in order to look for threats. These are the minimum requirements to run a basic SOC.
Although some professionals may argue that a SOC should really be reacting to threats and not just monitoring them.
However, you can have a monitor-only SOC if that’s all you really think that you need in your business.
4. Respond To Cyber Attacks & Threats
Now in the next step, security analysts need to be able to do something with data collected from the SIEM. It could be as basic as blocking IPs from some bad source.
To do this, you’ll need firewalls and an intrusion prevention system (IPS).
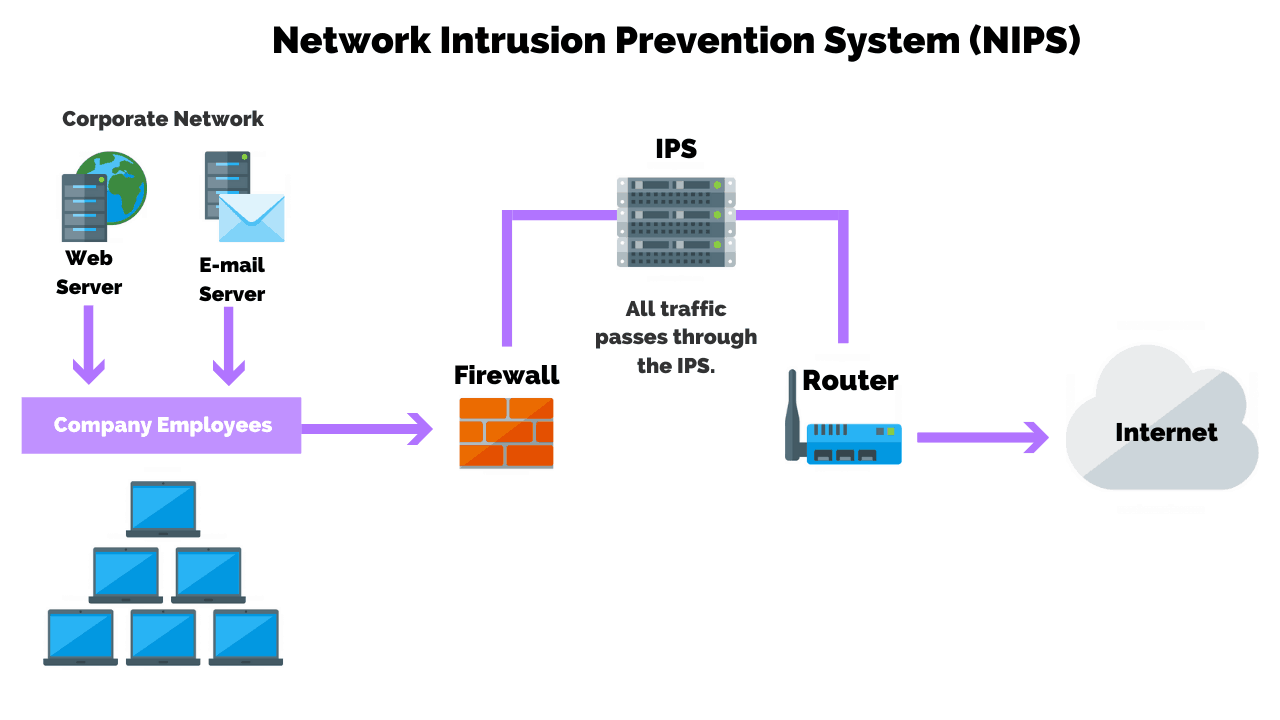
This is where we get into advanced SOCs. Most perimeter tools go way beyond just a firewall in your traditional sense.
If you’re in a cloud service, there are all kinds of application gateways, API connectors, cloud tools, and numerous other ways that traffic can enter your environment.
And there are numerous different ways that you can protect the traffic coming in through there. So if you’re trying to block it, you need to be able to communicate with these tools.
In some way, a lot of SOCs will use a tool that sits in an environment that can speak to all these configurations or build AWS or Azure configurations for themselves to act as a firewall.
This is your first layer of response. Now that’s really basic. And these days SOCs are doing so much more than that because there’s also threat intelligence.
There’s dynamic data science coming in here so that they can continuously update signatures and keep on top of current threats.
And that’s a really important part of what a SOC does and how it works – it’s constantly moving.
5. Report Findings To Stakeholders
Finally, a SOC must report findings to the CISO, CIO, CFO, and/or CEO, so that they are aware of what happens within their business. This is typically delivered in the form of risk reports.
This ensures that decision-makers in the business are:
- Aware of what is happening
- Aware of their current running risk
- Aware of the dollar value of that risk
The purpose of this reporting is to drive the company towards some kind of corporate security goals.
What Are The Best Practices For Running A SOC?
There are 4 main best practices to consider when running a SOC:
- Widening the scope
- Increasing data intake
- Enforcing deeper analysis
- Embracing automation
Widening The Scope
Recall that visibility is the number one priority when it comes to running a SOC number one visibility.
A big part of that is inventory.
If you can’t see it, you can’t protect it. And if you don’t know it’s there you can’t put all your visibility tools on it.
You need to inventory all of your software, all of your IT systems within your enterprise, not just for the SOC, but for the system admins, and for auditing.
This inventory ultimately serves as the scope for the SOC.
The wider the scope, the bigger the shield, the more protection you have.
It’s essential that your SOC cover the entire scope of what you’re trying to protect with your goals in mind.
Increasing Data Intake
Another best practice is optimizing and increasing your data intake. Your SOC needs a good data stream.
However, you have to make sure that the tools and your network can support the data intake.
Network configurations need to happen in order to get information through to the Splunk server. Or, you’re using a managed service you have to consider data that is being sent outside of your environment.
Next, you have to worry about encrypted, secure, external connections to send all of your data, all of your logs outward, usually from that appliance.
Enforcing Deeper Analysis
Don’t just react. Reacting is not even half the game. It’s like an eighth of the game. It’s great if you react, but to really, truly understand what’s going on you need to make sure that your team is analyzing everything.
That’s why we call them analysts. It’s often the case that small problems can be clues to a much larger threat that’s happening, especially when we’re talking about these apt groups.
These groups deploy very subtle techniques and so the analysis is essential to uncovering these threats.
Your SOC needs to make sure that they’re analyzing and understanding your security posture every day.
Embracing Automation
Introduce automation into your SOC. The more tasks you can automate, the more time your people can spend analyzing and using their human brains.
That’s why you have them.
The tools are going to do the job of grabbing all the stuff and blocking the things, but you hire the people for their abilities to identify patterns and create connections in ways that computers can’t.
So automate menial tasks so that your most valuable assets can spend more time using their brains.
Conclusion
Cybersecurity for the modern internet is a lot like the Cold War; both sides are constantly improving and innovating their weapons and defenses to overcome the other.
There is no stopping the constant evolution of the internet or technology itself. Meanwhile, threat actors continue to move with the trends evolving their toolsets and techniques along the way.
For businesses and, more often every day, private citizens, it is important to understand that the tools of cyber security have greatly changed at an accelerated pace over the last few years.
It is no longer sufficient to have client-side antivirus and firewalls to protect your IT.
Instead, modern security and safety mean continuous monitoring, scanning, and testing of your IT infrastructure to meet basic due diligence, and it is becoming ever more important to include response as a security discipline within the organization.