Ping attacks are a form of DDoS attack that attempts to flood a system with requests in an attempt to disable it.
You can prevent ping attacks by configuring your firewall, adding filters to your router, looking at spoofed packets, monitoring traffic patterns, and scanning your network.
Learn More: How To Prevent Cyber Attacks
Free IT Security Policies
Get a step ahead of your goals with our comprehensive templates.

What Are ICMP Flood Attacks?
A ping attack is an attack designed to overwhelm or flood a targeted device with ICMP (Internet Control Message Protocol) pings.
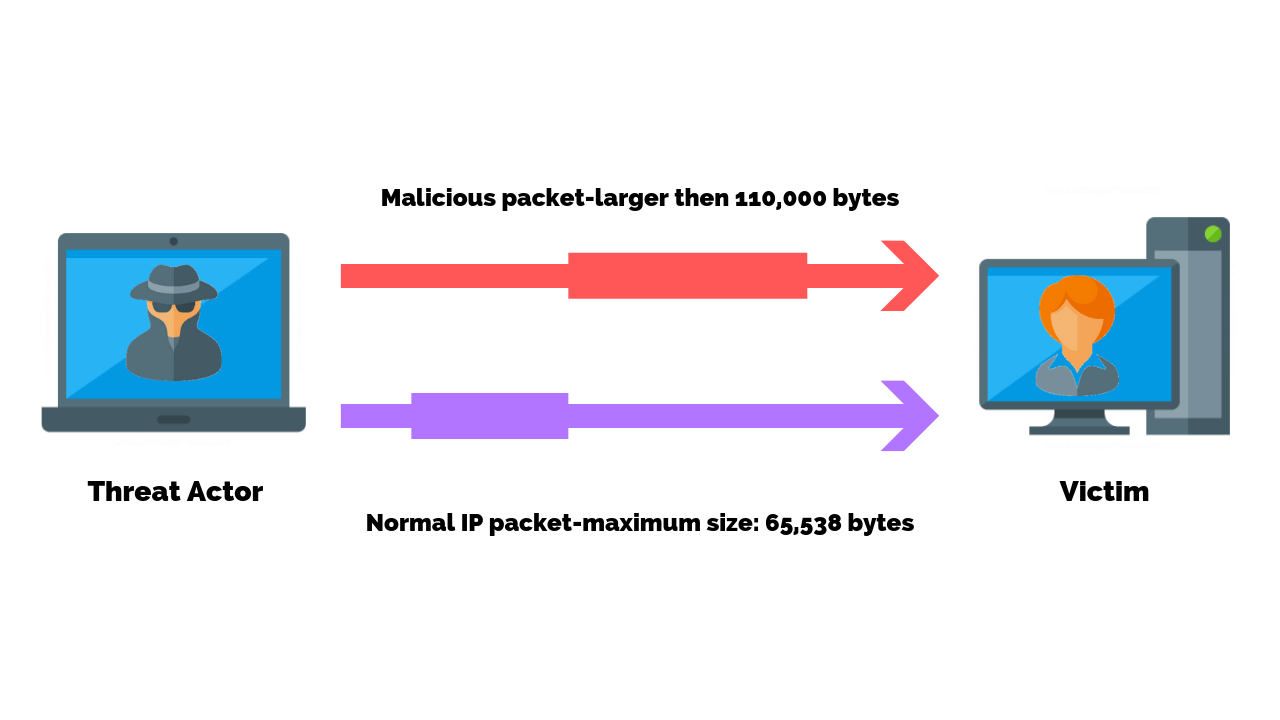
In normal situations, a ping is used to check connectivity between a source and a destination devices by way of ICMP echo-requests and echo-reply messages.
A Ping Attack on the other hand purposely floods the target device with requests packets.
The destination device is forced to respond with an equal number of reply packets and eventually cannot keep up with the volume of requests. This causes the target to become inaccessible to normal traffic and unresponsive to normal ping requests.
Example Of A ICMP Flood Attack
Heartbleed is perhaps one of the most widely known buffer overflow vulnerabilities. It surfaced as a critical flaw in the widely used OpenSSL software, which many internet servers relied upon for implementing TLS (Transport Layer Security).
Countless servers operated by prominent companies (including Yahoo) were affected. The vulnerability allowed attackers to read sensitive information from the server’s memory, potentially compromising user data.
How Can You ICMP Flood Attacks?
Firewall Configuration
Configure firewall rules to specifically deny ICMP echo requests (pings) from reaching your network’s internal devices. This action effectively hides the presence of your network devices from external scanners and attackers.
Access your firewall’s settings and create a rule that blocks ICMP ping requests. This rule can be applied globally or selectively, based on the source IP addresses deemed untrustworthy.
Router Filters
Implement filters on your router that are designed to scrutinize incoming data packets. These filters should be configured to reject packets that are malformed or originate from known malicious sources.
Use the router’s ACL (Access Control Lists) or similar feature to set up criteria that inspect packet integrity and source. Define actions for the router to take when encountering packets that do not meet these criteria, such as dropping the packet.
Egress Filtering For Spoofed Packets
Egress filtering is essential for identifying and stopping packets that appear to be coming from inside your network but are originating from external attackers (IP spoofing).
Configure your network devices to validate the source IP of outgoing packets, ensuring they belong to your internal IP range. This practice prevents attackers from using your network to launch attacks, making it harder for them to conceal their location.
Network Monitoring Software
Deploy network monitoring solutions that can analyze traffic patterns in real time. Such software helps in detecting anomalies that deviate from normal traffic behavior, which could indicate a Ping Attack or other
Choose network monitoring tools that offer detailed traffic analysis, real-time alerts, and the ability to set baselines for normal traffic patterns. Configure alerts for unusual traffic spikes or patterns indicative of a potential attack.
Regular Scanning For Open Ports
Regularly scanning your network for open ports that deviate from your established baseline helps in identifying potential vulnerabilities that attackers could exploit.
Use port scanning tools to conduct scheduled scans of your network. Compare the scan results against your known network baseline to identify unexpected open ports. Once identified, assess whether these ports need to remain open and apply necessary security measures, such as closing unnecessary ports or applying strict access controls.
Article by