SYN floods are a form of DDoS attack that attempts to flood a system with requests to consume resources and ultimately disable it.
You can prevent SYN flood attacks by:
- Installing an IPS.
- Configuring your firewall.
- Installing up-to-date networking equipment.
- Installing commercial monitoring tools.
Learn More: How To Prevent Cyber Attacks
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is A SYN Flood Attack?
For every client and server connection using the TCP protocol, a required three-way handshake is established, which is a set of messages exchanged between the client and server.
The handshake process is listed below:
- The three-way handshake is initiated when the client system sends a SYN message to the server.
- The server then receives the message and responds with a SYN-ACK message back to the client.
- Finally, the client confirms the connection with a final ACK message.
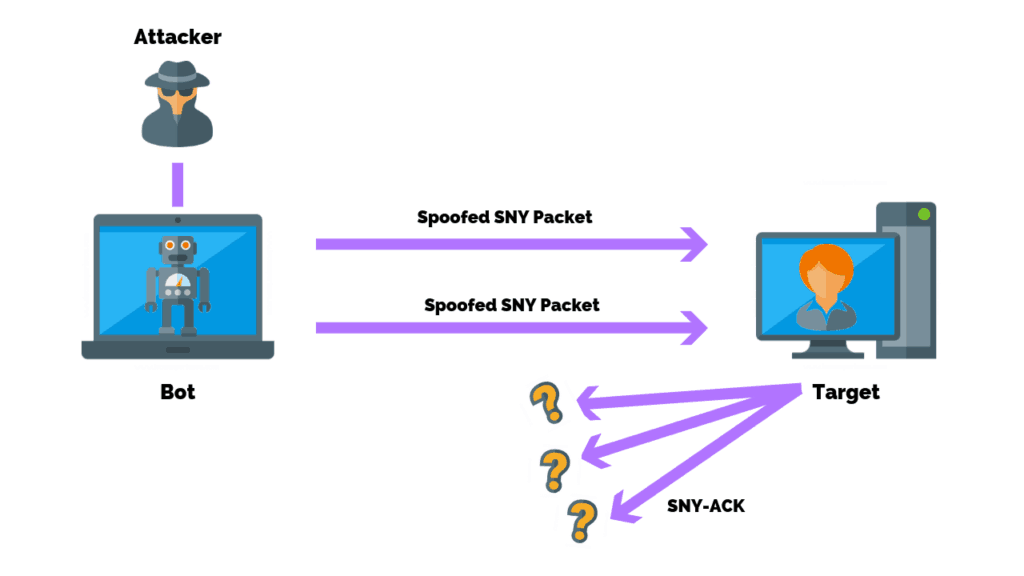
A SYN flood manipulates the handshake which allows the attacker to rapidly initiate a connection to a server without finalizing the connection.
The server has to spend resources waiting for half-opened connections, which can consume enough resources to make the system unresponsive to legitimate traffic.
Example Of A SYN Flood Attack
The Mirai Botnet, which used SYN Flood, among other ‘flooding’ techniques, to compromise over 600,000 Internet of Things (IoT) devices.
It launched one of the most damaging DDoS attacks in history against high-profile targets, including KrebsOnSecurity, a well-known internet security blog, Lonestar cell – a popular telecom operator in Liberia, and Dyn – a broadly used DNS provider.
How To Prevent A SYN Flood Attack
- Installing an Intrusion Prevention System (IPS): An IPS can detect anomalous traffic patterns and block malicious packets1. It’s your first line of defense against SYN Flood attacks. For example, if the IPS detects a sudden surge in SYN requests from a single IP address, it could indicate a SYN Flood attack and the IPS could block further requests from that IP address.
- Configuring the Onsite Firewall for SYN Attack Thresholds and SYN Flood Protection: Firewalls can be configured to limit incoming traffic and block connections from suspicious or known malicious IP addresses. They can also be set to reduce the timeout for half-open connections, which can help mitigate the impact of SYN Flood attacks.
- Installing Up-to-Date Networking Equipment with Rate-Limiting Capabilities: Modern networking equipment often comes with built-in rate-limiting capabilities. This can help prevent SYN Flood attacks by limiting the number of SYN requests that a server will accept from a single IP address within a certain time frame.
- Installing Commercial Tools for Network Visibility: Commercial monitoring tools can provide visibility across the entire network, allowing you to analyze traffic from different parts of the network. This can help you identify patterns that may indicate a SYN Flood attack, such as a sudden increase in SYN requests.
Article by