Follina Windows Zero-Day Vulnerability Identified
Contents
What Happened?
The nao_sec team posted this on their Twitter account link on May 27, 2022, like a zero-day vulnerability because then there was no patch to address this.
Interesting maldoc was submitted from Belarus. It uses Word's external link to load the HTML and then uses the "ms-msdt" scheme to execute PowerShell code.https://t.co/hTdAfHOUx3 pic.twitter.com/rVSb02ZTwt
— nao_sec (@nao_sec) May 27, 2022
For those who don’t know, nao_sec is a cybersecurity research team that has been active since 2017 in finding various vulnerabilities that you can find on their official website.
Stay Up-To-Date On The Latest Attacks
Be the first to know when our experts release new insights on the top attacks.
You're on the list! Just one more step...
Check your email to confirm your subscription.
What Is MSDT?
Microsoft Support Diagnostic Tool (MSDT) is a service in Windows 11/10/8.1/7 and Windows Server, even the latest: Windows Server 2022.
The tool enables the Microsoft support representatives to analyze diagnostic data and find a resolution for the problems experienced by users.
To make it clearer to you which tool it is, it would be best to say that it is a troubleshooting window that almost never solved the user’s problem.
This software component is included on startup by default on the mentioned versions of Microsoft Windows and can be found in
“C:\Windows\System32″ under the name msdt.exe”.
The Exploitation of MSDT Vulnerability
As mentioned above, exploitation is done with the help of a malicious Word document example exploit_name.doc and enabled vulnerable Microsoft Support Diagnostic tool installed on a Windows machine.
This vulnerability has gone viral on the Internet and there are a lot of explanations for this vulnerability, let’s try to simplify for the part of the audience that is not technologically savvy.
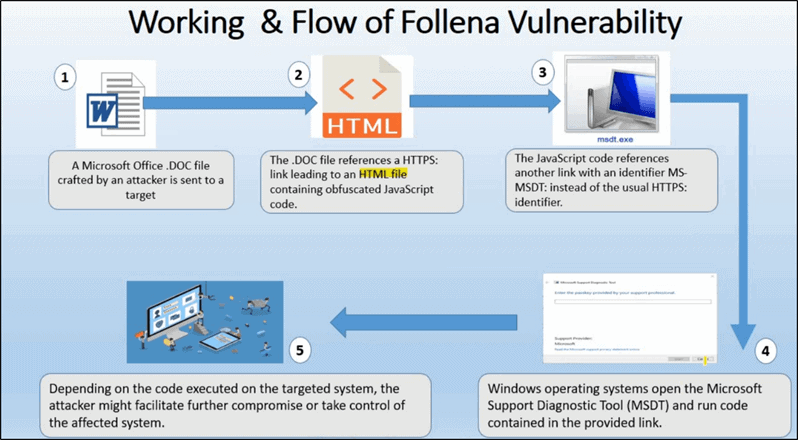
- The attacker creates a malicious Word document file that contains the malicious code.
- After the file is created manually or downloaded from the Internet and GitHub, the attacker delivers the file by e-mail with the help of social engineering or physically in another way (USB).
- When the victim receives, downloads, and opens the malicious file, an MSDT service opens that spins as if looking for a solution.
- At that point, the machine is already infected and the attacker has full access to the victim’s machine.
From here, the attacker can now work on further exploiting the machine in the background, installing persistence as a backdoor to maintain access, and working on escalating privileges from user to administrator.
The complete procedure in the more professional edition can be seen in the picture below, as well as in the references, links with a more detailed description, and where the exploit can be found.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

How To Protect Against Follina RCE Exploit
On Tuesday, June 14, 2022, Microsoft issued Windows updates to address this vulnerability. Microsoft recommends installing the updates as soon as possible.
In particular, to prevent exploitation of this vulnerability, you can disable support for the MSDT URL protocol by taking these steps:
- Run Command Prompt as Administrator.
To back up the registry key, execute the command “reg export HKEY_CLASSES_ROOT\ms-msdt filename.” - Execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”.
- -Check your antivirus program or Windows defender on the machine to see if it is up and running.
This first line of protection will stop most of these types of files that have not been modified to bypass antivirus and defenders, of course, if the attacker is not highly skilled.
If you are in a company environment, it is recommended that endpoint protection is present, which will also be upgraded and noticed based on the behavior of this type of file.
Article by
Share This Article
Our Editorial Process
Our content goes through a rigorous approval process which is reviewed by cybersecurity experts – ensuring the quality and accuracy of information published.
Categories
The Breach Report
Our team of security researchers analyze recent cyber attacks, explain the impact, and provide actionable steps to keep you ahead of the trends.