2.4 TB Data Leak Caused By Microsoft’s Misconfiguration
Contents
Summary Of The Attack
- On September 24, 2022 SOCRadar detected a misconfigured public bucket where Microsoft stored 2.4 TB of data.
- Impacted were 65,000 entities from 111 countries.
- The exposed data is dated from 2017 to August 2022.
- Microsoft stated that SOCRadar exaggerated the scope of the data leaked.
Stay Up-To-Date On The Latest Attacks
Be the first to know when our experts release new insights on the top attacks.
You're on the list! Just one more step...
Check your email to confirm your subscription.
What Happened?
Misconfiguration of an endpoint caused a leakage of 2.4 TB of data of Microsoft’s customers.
The issue stemmed from a misconfigured Azure Blob Storage and was spotted on September 24, 2022, by the security company SOC Radar.
What Is The Impact?
According to the SOCRadar statement, the data leaked was stored on a misconfigured Azure Blob Storage and the impact spanned 65,000 entities from 111 countries.
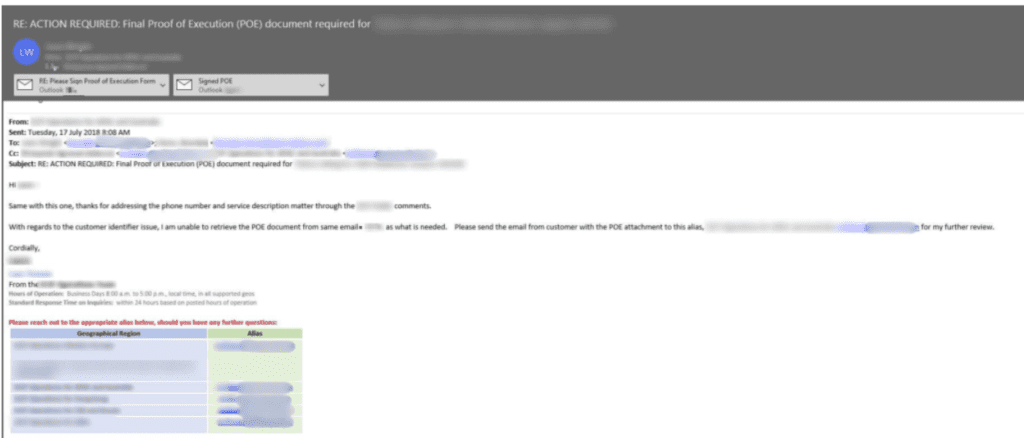
Customer data was the entity that suffered in this Microsoft data leak, which included:
- Names
- Email addresses
- Email content
- Company name
- Phone numbers
- Proof of concept documents
- Sales data
In addition, attached files relating to business between a customer and Microsoft or an authorized Microsoft partner were also exposed.
Per their statement, the exposed data is dated from 2017 to August 2022.
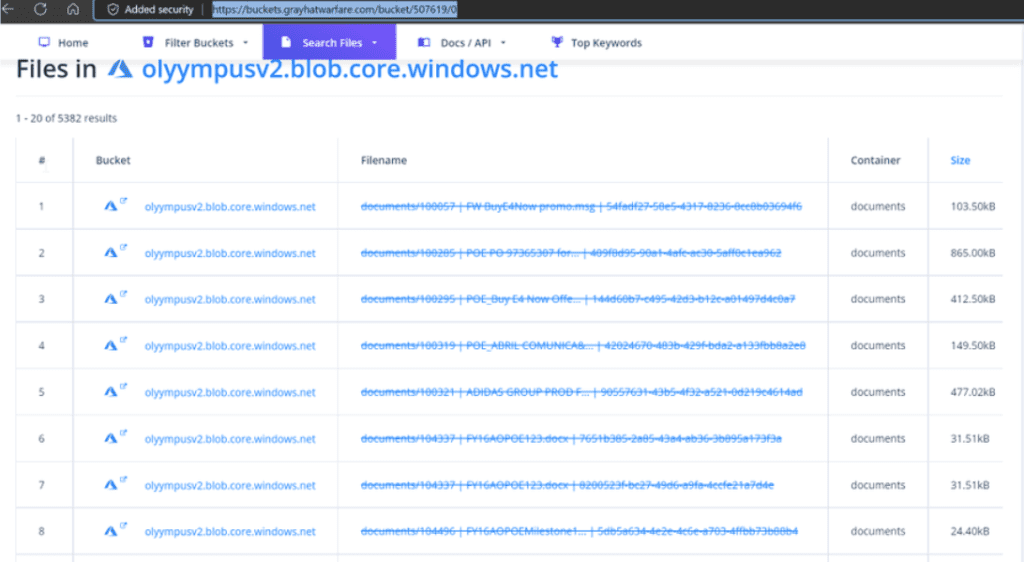
Researchers stated that the bucket was publicly indexed for months and it actively appeared in search engines.
The researchers named the leak “BlueBleed” referring to the exposed sensitive data from six misconfigured buckets.
SOCRadar even set up a website called BlueBleed where users can check if their data has been exposed.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is BlueBleed?
From the official SOCRadar website it is clearly stated that the term “BlueBleed” was created by Can Yoleri, who is a Threat and Vulnerability Researcher at SOCRadar.
The term refers to the sensitive information leaked by six misconfigured buckets collectively.
In their blog post, it is clearly elaborated how they discovered BlueBleed Part I as it is referred to.
The issue they stated was clearly a misconfigured public bucket where they stored 2.4 TB of data inside one single bucket.
By their estimation, it can be considered maybe one of the most significant B2B leaks, considering the scope of it.
How Can The Information Be Used?
Third parties or threat actors that might have had access to the bucket can use this information in different ways.
The first and most obvious one is scraping the email addresses for targeting the companies affected by the breach utilizing social engineering techniques, however blackmailing and selling the information on the dark web or Telegram channels are also viable options.
Besides that, SOC Radar also stated that the information exposed included information about network configuration and infrastructure posture of potential customers.
This opens another vector of attack, where researchers or threat actors might start looking for vulnerabilities in those systems and network configurations based on the information from the exposed data.
Microsoft’s Response
Microsoft in their statement elaborated that they do appreciate that SOCRadar informed them about the issue, however, following SOCRadar’s blog post Microsoft stated that the security company has greatly exaggerated the scope.
Based on Microsoft Security Response Center’s in-depth analysis and investigation they were able to conclude that a lot of the data that was exposed was duplicate information with multiple references to the same projects, email addresses and users.
They also expressed their disappointment in SOCRadar releasing a search tool where users can check if their data is exposed, since that does not follow best security practices and may even pose an additional security risk.
Actions Taken
In the official statement released to the customers, Microsoft stated that they did notify every impacted customer directly and provided them with instructions on how they can further proceed to handle the incident.
Article by
Share This Article
Our Editorial Process
Our content goes through a rigorous approval process which is reviewed by cybersecurity experts – ensuring the quality and accuracy of information published.
Categories