Nimbuspwn Vulnerability Discovered By Microsoft
Contents
What Happened?
In April 2022, Microsoft 365 Defender Research team discovered a vulnerability named Nimbuspwn, where an attacker can gain escalation of privilege from local users with low capabilities to root access on multiple Linux desktop environments.
Stay Up-To-Date On The Latest Attacks
Be the first to know when our experts release new insights on the top attacks.
You're on the list! Just one more step...
Check your email to confirm your subscription.
What Is Nimbuspwn?
The “Nimbuspwn” vulnerability is recorded as CVE-2022-29799 (Directory Traversal) and CVE-2022-29800 (TOCTOU race conditions).
When these two vulnerabilities are linked together, they give the attacker root privileges and from there he can deploy other payloads, compromising Linux systems via arbitrary root code execution and potentially exposing compromised Linux environments to more advanced threats, including ransomware attacks to achieve greater impact on vulnerable devices.
Who Is Impacted By The Nimbuspwn Vulnerability?
According to research by the Microsoft Team, the vulnerability was found in networkd-dispatcher versions v2.0-2 and v2.1-2. For those who don’t know, this service is responsible for systemd-networkd connection status changes.
It is similar to NetworkManager-dispatcher, but is much more limited in the types of events it supports due to the limited nature of systemd-networkd.
Reference: Detailed explanation for networkd-dispatcher.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

How Do I Tell If I Am Vulnerable To Nimbuspwn?
With these simple commands, we can check on our Linux distribution whether this service exists and whether it is enabled, as well as which version it is.
Command: $ sudo apt list networkd-dispatcher
This command is enough to see the version information.
Command: $ sudo apt show networkd-dispatcher
This command will give your comprehensive information about the package.
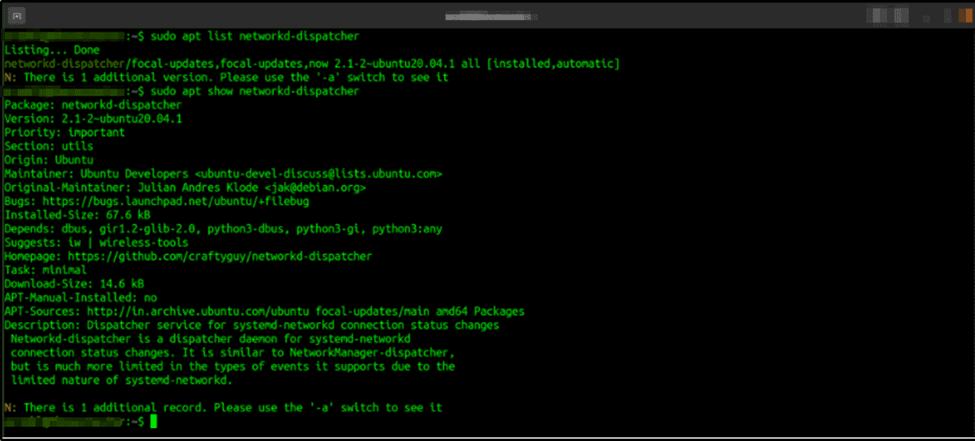
In this image, we can see an example of a vulnerable server as it’s running v.2.1-2.
How To Remediate The Nimbuspwn Vulnerability
In case you have enabled service networkd-dispatcher with a vulnerable version on your Linux Distribution, we can recommend a few steps to fix this flaw:
There are a few commands that we can use to update our system repositories:
Command: $ sudo apt update && sudo apt upgrade –y
You need to upgrade your service if it is installed and enabled:
Command: $ sudo apt upgrade networkd-dispatcher
You can always remove this service if there is no fixed version:
Command: $ sudo remove networkd-dispatcher | sudo purge networkd-dispatcher
Additional Resources
Wrapping Up
Microsoft also recommends implementing a “proactive vulnerability management approach” that identifies and mitigates previously unknown vulnerabilities.
It is also recommended to install endpoint security solutions capable of detecting the directory traversal vulnerability required to complete the Nimbuspwn attack chain.
Article by
Share This Article
Our Editorial Process
Our content goes through a rigorous approval process which is reviewed by cybersecurity experts – ensuring the quality and accuracy of information published.
Categories
The Breach Report
Our team of security researchers analyze recent cyber attacks, explain the impact, and provide actionable steps to keep you ahead of the trends.