Uber’s Internal Systems Compromised By An 18 Year Old
Contents
Summary Of The Attack
- On September 15th, Uber’s internal systems were compromised.
- The attacker managed to hack the company’s HackerOne account, gained access to a Slack account and obtained full admin on their AWS Web Services and GCP accounts.
- The entry attack targeted Uber’s employees utilizing a social engineering campaign.
- Uber is still investigating the incident and some of their internal systems were temporarily disabled due to the hack.
Stay Up-To-Date On The Latest Attacks
Be the first to know when our experts release new insights on the top attacks.
You're on the list! Just one more step...
Check your email to confirm your subscription.
What Happened?
On September 15th, an 18 year old managed to hack Uber. The hacker reportedly gained control over the company’s internal systems leveraging social engineering techniques that led to compromising an employee’s Slack account.
We are currently responding to a cybersecurity incident. We are in touch with law enforcement and will post additional updates here as they become available.
— Uber Comms (@Uber_Comms) September 16, 2022
From there on the hacker accessed their internal databases, and obtained control of the company’s Amazon Web Services and Google Cloud accounts.
How The Attack Happened
Allegedly the attack was carried out by the hacker performing what it seems to be a classic social engineering play.
The hacker sent a text message to an Uber employee that seemed like it was coming from the Uber’s IT department, the employee thought it was a legitimate message coming from their department and they shared their password.
Once the password was shared the hacker was in.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Was The Impact?
On September 16th, Uber decided to give a statement on Twitter, claiming that they are responding to a cybersecurity incident without giving out too many details.
However, data coming in from different sources indicates that the hacker got access to Uber’s HackerOne account and most likely all their reports.
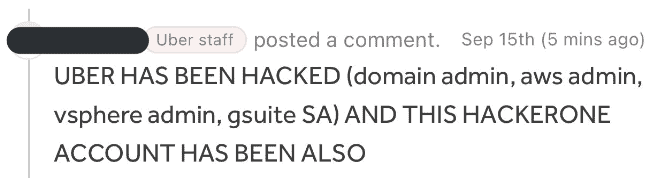
Apart from that, Sam Curry, a Bug Bounty Hunter, also shared on Twitter that the hacker claimed they’ve got full administrative rights on AWS and Google Cloud Platform.
Someone hacked an Uber employees HackerOne account and is commenting on all of the tickets. They likely have access to all of the Uber HackerOne reports. pic.twitter.com/00j8V3kcoE
— Sam Curry (@samwcyo) September 16, 2022
He also posted that an Uber employee shared that at Uber they got an urgent email stating that all employees should stop using Slack, which is the platform on which the hacker, after gaining access, posted a message from the compromised user’s account saying “I announce I am a hacker and Uber has suffered a data breach.”
From the employee statements, the message initially was not taken seriously by the rest of the employees, until the IT team asked the employees to stop using Slack.
Because of the breach, some of Uber’s internal systems, including Slack, were temporarily disabled.
The Aftermath
Uber still hasn’t disclosed the scope of the breach and how exactly they are dealing with it.
However, it does seem like the hackers were motivated by the hack by the low pay that Uber drivers receive as was seen in one of the messages that were posted on Slack, as reported by the New York Times.
They haven’t asked for a ransom and it does look like they have done this to affect Uber’s reputation.
Concealing A Data Breach
This is not the first time Uber had to deal with a cybersecurity data breach.
In 2016, 57 million driver accounts were breached and confidential information was stolen.
A deeper investigation was conducted into the current and now former and accused CISO Joseph Sullivan.
This month, Mr. Sullivan was found guilty of obstructing justice and actively concealing a felony for concealing the breach from the Federal Trade Commission, which was investigating Uber’s privacy protections at the time.
He faces up to five years in prison for obstruction and up to three years for the latter charge.
Based on our sources and information available online, Sullivan was made aware of a data breach that had occurred at Uber which happened on November 3, 2016.
A hacker had gained access to the personal information of 57 million Uber users, including their names, email addresses and phone numbers.
Rather than reporting the breach to the authorities, Mr. Sullivan hid it.
He then paid the hacker $100,000 to destroy the evidence and keep quiet about what had happened.
Article by
Share This Article
Our Editorial Process
Our content goes through a rigorous approval process which is reviewed by cybersecurity experts – ensuring the quality and accuracy of information published.
Categories
The Breach Report
Our team of security researchers analyze recent cyber attacks, explain the impact, and provide actionable steps to keep you ahead of the trends.