Previous
Cisco Suffers Cyber Attack By UNC2447, Lapsus$, & Yanluowang
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Dušan Trojanović / Last Updated: 8/24/2022
Reviewed By: Dalibor Gašić, & Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
Summary Of The Attack
- Cisco confirmed that the UNC2447 cybercrime gang, Lapsus$ threat actor group, and Yanluowang ransomware operators breached its corporate network in late May and that the actor tried to extort them under the threat of leaking stolen files online.
- During the investigation, it was determined that a Cisco employee’s credentials were compromised after an attacker gained control of a personal Google account where credentials saved in the victim’s browser were being synchronized.
- The attacker conducted a series of sophisticated voice phishing attacks under the guise of various trusted organizations attempting to convince the victim to accept multi-factor authentication (MFA) push notifications initiated by the attacker. The attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user.
- After obtaining initial access, the threat actor conducted a variety of activities to maintain access, minimize forensic artifacts, and increase their level of access to systems within the environment.
What Happened?
Cisco has confirmed that Yanluowang ransomware operators, UNC2447 and Lapsus$ groups have breached their local network on the May 24, 2022, described their actions and it has resulted that human is still supposed to be the security weakest link.
After further breach impact analysis on Cisco business, there was no impact on any Cisco services, sensitive customer or employee data, Cisco intellectual property, or supply chain operations.
What Is The Impact?
Ransomware operators Yanluowang claimed that they manage to steal a total of 2.75 GB including 3100 files that were published on the Dark web on the 10th of August.
Cisco shared technical details with the public and they claimed that they took additional measures to get their network and systems safe from potential similar attacks in the future.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
How Did This Attack Happen?
According to Talos analysts, the attackers started by gaining control of a Cisco employee’s personal Google account.
Cisco compromise started when one of their employees had enabled password syncing and had stored its Cisco corporate credentials in the Google Chrome web browser, allowing credentials to synchronize to the Google account.
After obtaining the user’s credentials attacker attempted to bypass MFA (Multi-Factor Authentication) with multiple bypass techniques, and with two of them, vishing (Voice phishing) and MFA fatigue attackers managed to gain access and enroll multiple new devices to authenticate to Cisco VPN service.
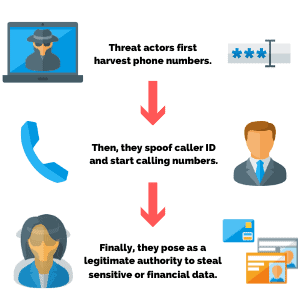
Vishing is a common social engineering technique where attackers try to trick employees into disclosing sensitive information over the phone.
MFA fatigue is an attack where criminals target a user’s MFA application for account access by sending multiple push requests to the target device until user accidentally or on purpose allow one of the repeated push notifications they are receiving.
After attackers successfully authenticated to Cisco VPN service, they had escalated from regular user privilege to administrative privileges, which allowed them to log in to multiple systems inside Cisco’s corporate network.
For remote accessing systems attackers have used tools similar to LogMeIn and TeamViewer.
Once attackers gain access to a system, they began to enumerate the local environment. They do this by using built-in Windows utilities to enumerate the targeted system, user, and group membership configuration.
This results in obtaining details about the operating user’s account context.
Offensive Security Tools Used
In order to accomplish privilege escalation, they have used offensive security post-exploitation tools such:
They then added their backdoor accounts as well as persistence mechanisms.
Maintaining Access
Attackers gained access to credential databases, registry information, and memory that contained credentials and deleted accounts they created.
Next, they cleared system logs to cover their tracks, as well performing a variety of activities for:
- Maintaining systems access
- Minimizing forensic artifacts
- Increasing access level to systems within the local environment
Attackers managed to drop multiple payloads onto systems.
One of them was a simple backdoor payload that takes commands from a command and control (C2) server and executes them on the end system via an active terminal session.
How To Mitigate These Types Of Attacks
Attackers were not successful at deploying ransomware, but there were able to deploy backdoor payload communicating with C2 server.
Cisco added two new ClamAV detections for the backdoor and a Windows exploit used for privilege escalation Win.Exploit.Kolobko-9950675-0 and Win.Backdoor.Kolobko-9950676-0, which were created to help other organizations to detect similar attacks.
The best way to mitigate this type of attack is to:
- Implement strong device verification for MFA solution by enforcing stricter device controls to manage enrollments and access from unmanaged or unknown devices.
- Check endpoint security posture before allowing VPN connections from remote endpoints.
- Implement network segmentation to improve network performance and security.
- Implement a SIEM solution to have greater visibility and real-time analysis of security alerts that happens inside the network.
Related Articles:

Dušan Trojanović
Dušan is a Senior Security Engineer actively working as a penetration tester in DevSecOps projects. He is also an avid security researcher bringing forward analysis on the latest attacks and techniques.
Recent Attacks
- Top 10 Cyber Attacks In 2022
- Top 10 Vulnerabilities In 2022
- Rackspace Ransomware Attack
- Dropbox Suffers Data Breach
- Iranian APT Uses Log4j
- Google SEO Poisoning Campaign
- Killnet DDoS Target Airports
- Advocate Aurora Health Data Leak
- Microsoft 2.4 TB Data Leak
- Optus Exposes 2.1M Customers
- $570M Binance Coin Hack
- TikTok Denies Cyber Attack
- NATO Data Leak
- Uber’s Systems Compromised
- Cisco Cyber Attack
- Samsung Exposes PII
Popular Articles
Ransomware Attacks
Preventing Attacks





 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO