Australian Telecom Optus Exposes
Data Of 2.1 Million Customers
Contents
Summary Of The Attack
- On October 3, 2022, Australian mobile company Optus confirmed that a cyberattack last month had exposed the government identification numbers of 2.1 million of its customers.
- The Disclosure came following the leak of 10,000 Optus customer records, which included user information such as names, birthdates, home, and email addresses, phone numbers, and personal identification numbers.
- The threat actor had first tried to blackmail Optus by demanding a $1 million ransom in exchange for them not disclosing or selling the stolen data.
- The actual data breach appears to have been caused due to improperly configured security protections on an API endpoint, but still, there is no proper understanding in Optus of how the incident occurred.
Stay Up-To-Date On The Latest Attacks
Be the first to know when our experts release new insights on the top attacks.
You're on the list! Just one more step...
Check your email to confirm your subscription.
What Happened?
On October 3, 2022, Australian mobile company Optus confirmed a cyber attack last month had exposed the government identification numbers of 2.1 million of its customers.
What Was The Impact?
The Disclosure came following the leak of 10,000 Optus customer records, which included user information such as:
- Names
- Birthdates
- Home
- Email addresses
- Phone numbers
- Personal identification numbers
14,900 genuine Medicare ID numbers were also compromised as a result of the incident.
How The Attack Happened
The actual data breach appears to have been caused by improperly configured security protections on an API endpoint, but still, there is no proper understanding in Optus of how the incident occurred or how to stop it from happening again.
Optus has hired Deloitte to conduct an independent external review of the company’s security systems and processes.
At least one number from a current, legitimate form of identification, along with personal data, has been compromised for about 1.2 million clients.
These customers have been contacted by Optus, and it has been suggested to take steps to update their identification documents.
Along with personal information, numbers related to expired IDs have been exposed to about 900,000 customers. Optus consults with authorities on what additional actions clients should take.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

The Ransom Demand
The threat actor had first tried to blackmail Optus by demanding a $1 million ransom in exchange for them not disclosing or selling the stolen data.
The hacker posted the personal information of 10,000 clients, including names, addresses, phone numbers, and dates of birth, on a hacking site after not being paid.
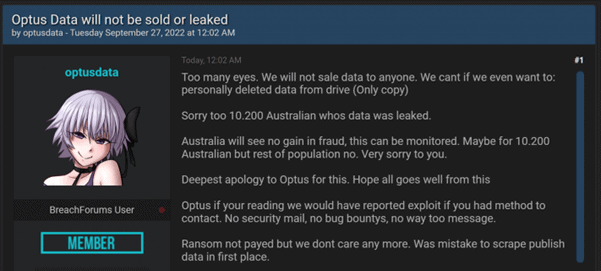
Optus can confirm for the 7.7 million clients for whom the leaked information did not contain valid or current document ID numbers after carefully analyzing the data for the company’s 9.8 million customers with the assistance of government agencies.
Information like email addresses, birth dates, or phone numbers was included in the data. For these clients, it’s critical to use caution.
What Is Optus’s Response?
Customers whose current ID documents were affected by the cyberattack received emails or SMS messages from Optus informing them that their ID document information had been compromised and outlining what they should do.
Additionally, Optus contacted clients whose IDs had expired to inform them that their IDs had been compromised.
Customers who have been informed that both their license number and card identification number have been compromised are urged to update their license number as soon as possible because the danger of identity fraud increases when this information is made public.
Customers are still advised to submit an application for a new license number even if only their license number was compromised.
More than 10,000 clients had their records put online, and the Australian Federal Police is currently conducting two investigations into who obtained and sought to sell the data and protections for those customers.
How Optus Could Have Prevented This Attack
If Optus had proper API monitoring in place, the transfer of sensitive data to the Internet, the lack of authentication, and the exposure of the testing API to public Internet traffic would have all been discovered, notified to, and addressed by Optus much earlier than a post to a data-leak forum.
The effects of the Optus data breach are still being felt, and a class action lawsuit is now a very real possibility.
Protecting a company and its clients from harmful data attacks requires a combination of technologies, training, and building a culture of security awareness.
Article by
Share This Article
Our Editorial Process
Our content goes through a rigorous approval process which is reviewed by cybersecurity experts – ensuring the quality and accuracy of information published.
Categories
The Breach Report
Our team of security researchers analyze recent cyber attacks, explain the impact, and provide actionable steps to keep you ahead of the trends.