Contents
Summary Of The Research
- Starlink is a satellite Internet company owned and overseen by SpaceX. It currently provides access to 39 countries and plans to cover the entire globe, particularly rural areas, with around 42,000 satellites in a few years.
- The equipment is perfectly made so there are not many parts, but just what you need to take it out of the box, plug it in and get online.
- At this year’s BlackHat USA, held Aug. 6-11 in Las Vegas, a Belgian security researcher stunned the crowd by hacking Starlink Dish with a $25 device, gaining major notoriety worldwide.
- The researcher in question disassembled his terminal, or as SpaceX calls it, “Dishy McFlatface,” and managed to perform a “Voltage Fault Injection Attack,” also known as “glitching,” to load modified firmware, after which he gained full access to the antenna.
- After Lennert W. reported this problem and received money from Starlink for it, Starlink could not fix this problem with a software update but would have had to release new hardware.
Stay Up-To-Date On The Latest Attacks
Be the first to know when our experts release new insights on the top attacks.
You're on the list! Just one more step...
Check your email to confirm your subscription.
What is Starlink?
Starlink is a satellite internet provider owned and overseen by SpaceX.
It currently provides access to 39 countries and plans to cover the entire globe with around 42,000 satellites in a few years.
This amazing project was launched in 2019, with the first satellites launched over the surface of the Earth to cover some of the remote parts of the country where there is little electricity and water, and now they have already started to cover them massively.
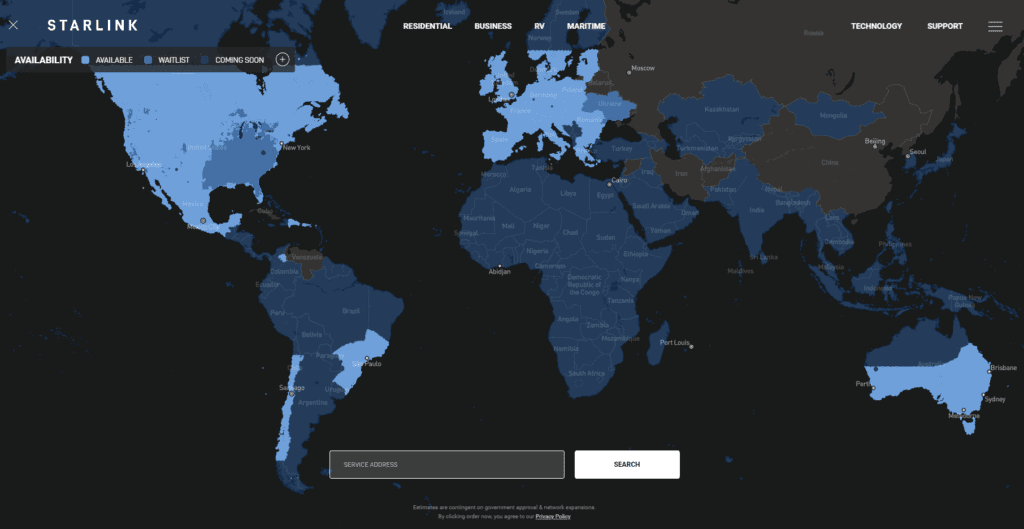
On the map above you can see the current area covered and the one where it is planned, and on the page where you can check if you can order the equipment.
The equipment is pretty much plug and play.
A satellite dish, as well as a pre-configured router from Starlink and a high-quality cable that connects the router and the antenna, is also included.
From there you’ll be able to expand your network, configure the subnet and your devices, as well as set up additional protections, whether you are a business or for your home.
Anatomy Of The Attack
- The attacker sent out a mass phishing email impersonating CircleCI, a major CI/CD software utilized by Dropbox internally.
- The phishing email sent the victim to a bogus CircleCI login page, where they submitted their GitHub credentials. CircleCi enabled users to log in using their GitHub credentials.
- Users were also asked to provide a One-Time Password (OTP) generated by their hardware authentication key,
- The attacker would get access to the victim’s GitHub account using the OTP and credentials given by the user
- The attacker copied 130 internal repositories, which contained both public and confidential code.
- The attacker’s future moves are unclear at this time, however, in prior assaults, the attacker looked for sensitive information such as secrets in order to migrate laterally into more sensitive systems.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Happened?
At this year’s BlackHat Lennert Wouters, a Belgian security researcher stunned the crowd by hacking Starlink Dish with a $25 device, gaining major notoriety worldwide.
With just $25 in off-the-shelf hardware, Lennert was able to gain root access to a Satellite Dish terminal, which allowed him to explore the broader Starlink network – a capability that could enable the exploitation of Starlink satellites themselves.
How The Attack Works
Starlink terminals are very hardened and quite locked, it is very difficult to run any code in the form of plugins or applications on them, this device will only run firmware from Starlink and no one else.
The researcher in question disassembled his terminal, or as SpaceX calls it, “Dishy McFlatface,” and managed to perform a “Voltage Fault Injection Attack,” also known as “glitching,” to load modified firmware, after which he gained full access to the antenna.
“Glitching” works by interrupting power to the antenna’s central processing unit (CPU) for a very short period of time to disrupt certain processor instructions.
The goal of this part of the attack is to bypass the “secure boot” code that confirms that the firmware on SpaceX’s memory chip is signed and has not been tampered with.
The Lennert managed to bypass this mechanism “secure boot” in such a way that he loaded the modified firmware and in that way got full root access to the dish.
He wasn’t satisfied with the hardware he used when he first succeeded in hacking the antenna because it was expensive.
So he took it a step further by ditching the expensive lab equipment and repeating the attack with a Raspberry PI Pico, before going one step further and making a custom circuit board that can be soldered directly to the dish.
This circuit board, commonly called a modchip, contains all the electronics needed for hacking and costs less than $25, plus it’s open source.
Starlink Remediation Solution
Starlink could not fix this problem with a software update but would have had to release new hardware.
However, SpaceX can make it harder to exploit the vulnerability by releasing a firmware update that blows a fuse in the dish and permanently disables the serial output, as Modchip uses this to trigger the hack.
Learn more about Starlink’s Bug Bounty program.
Article by
Share This Article
Our Editorial Process
Our content goes through a rigorous approval process which is reviewed by cybersecurity experts – ensuring the quality and accuracy of information published.
Categories
The Breach Report
Our team of security researchers analyze recent cyber attacks, explain the impact, and provide actionable steps to keep you ahead of the trends.