Awareness of the various types of security controls, their differences, and how they work to protect your business provides a holistic view of cybersecurity.
A Security Information And Event Management (SIEM) solution supports threat detection, compliance and security incident management through the collection and analysis of security events.
An Intrusion Detection System (IDS) is a network security technology built for detecting vulnerability exploits against a targeted application. The main difference between a SIEM and IDS is that SIEM tools allow the user to take preventive action against cyber attacks whereas an IDS only detects and reports events.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is A SIEM?
SIEM technology is a software application that enables IT staff to identify attacks before or as they occur, resulting in faster response times for incident response.
Without a SIEM, IT staff will lack a centralized view of all logs and events.
With limited visibility, IT staff will more than likely miss critical events from their systems, leading to a high number of backlogged events which may contain incidents that require immediate investigation.
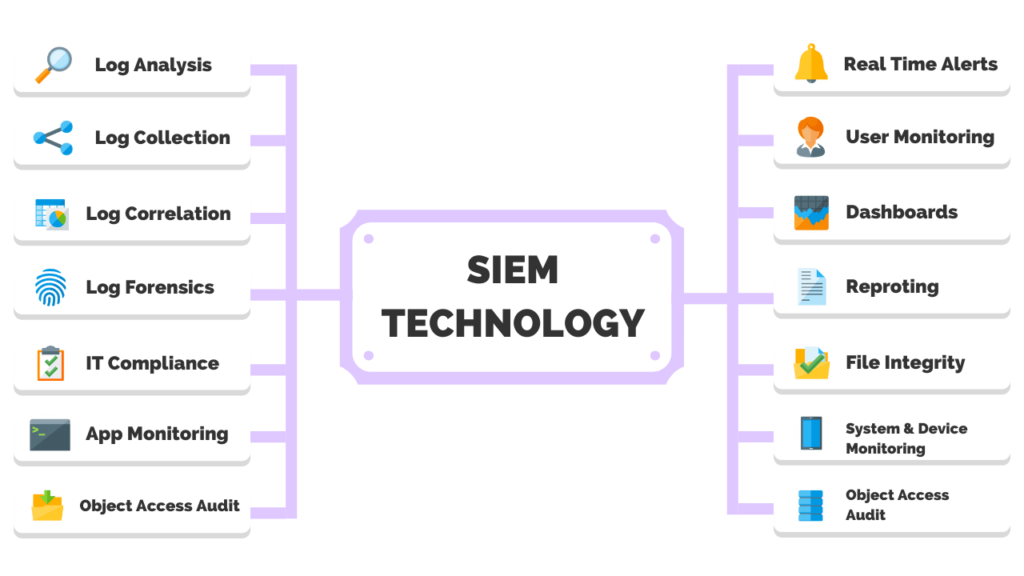
The core capabilities of a SIEM include:
- Log event collection and management including contextual data sources.
- Ability to analyze log events and other data across disparate sources.
- Operational capabilities such as incident management, dashboards, and reporting.
- Support for threat detection.
- Compliance and security incident management.
A SIEM is used to centralize security event log management, alerting, and correlation.
The SIEM allows you to monitor logging from systems, depending on how it’s configured, from one centralized tool. Many solutions also offer correlation, which allows you to review logs from multiple data streams and systems.
The SIEM searches the data for patterns to identify suspicious activity or a network breach.
What Is A IDS?
An IDS is a passive tool that is designed to identify an attack but does not prevent or stop an attack from compromising systems.
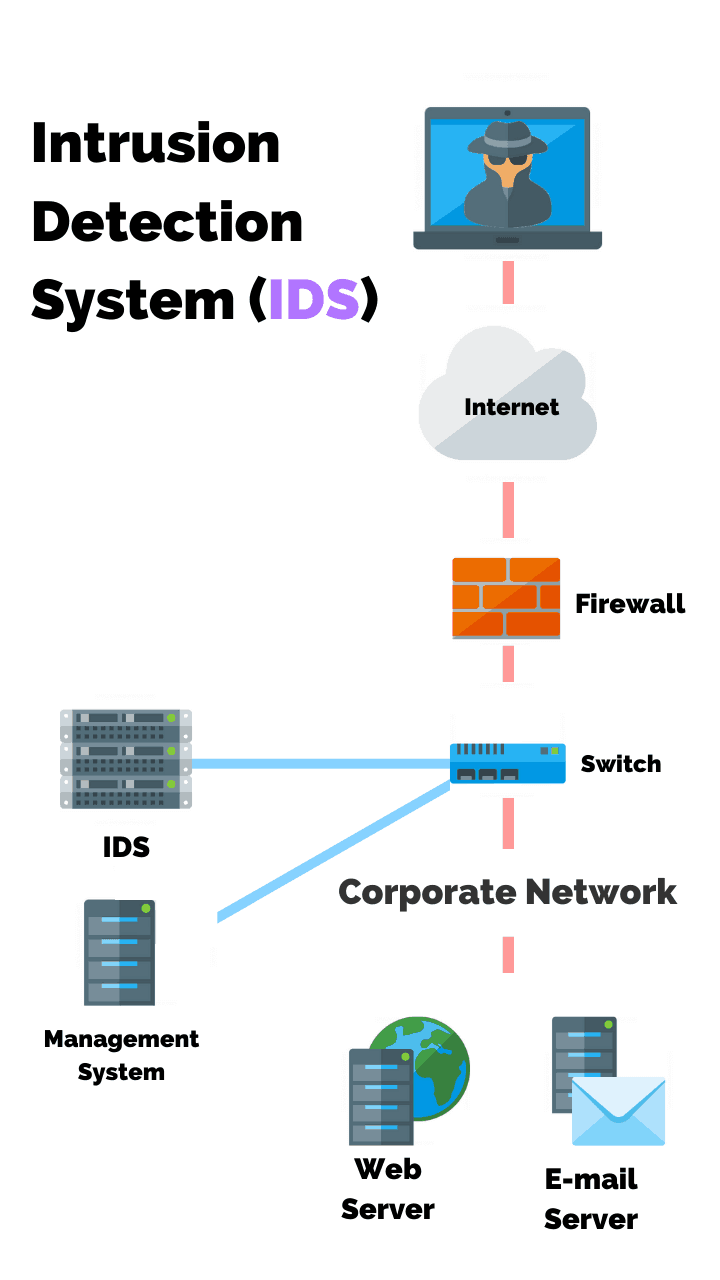
In a traditional IDS, traffic data is brought together and analyzed for suspicious activities in data. This is also referred to as signature-based monitoring, which detects attacks based on known attack signatures and patterns.
Another detection variant used by an IDS is heuristics/behavior more commonly referred to as anomaly-based. This type of monitoring detects attacks by first establishing a baseline of daily network traffic and its use.
The IDS compares day-to-day operations against the baseline. An alert is then sent to a security operations center, or security specialist when irregular or otherwise suspicious activity is detected.
Difference Between SIEM And HIDS
Another type of Intrusion Detection System is a software package that is installed on the endpoint or host device.
This type of system is referred to as a host intrusion detection system (HIDS).
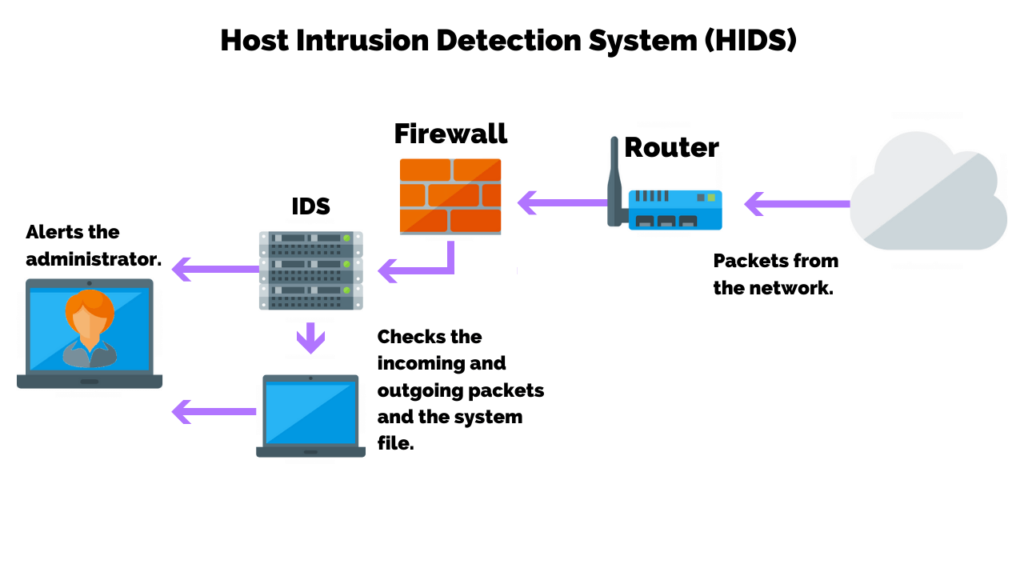
Popular anti-virus vendors include HIDS as part of their endpoint protection suite. Instead of relying on mirrored traffic from a TAP device, HIDS software will examine events on a computer on your network.
This type of intrusion detection system mainly operates by looking at data in system files on the computer that it protects. Those files include log and configuration files.
How A SIEM And IDS Work Together
Both the SIEM and IDS can be used in conjunction across an enterprise network to detect and prevent unauthorized access or control of sensitive equipment and data.
Complex heuristics use algorithms to determine the authenticity of traffic and credentials for each request.
The IDS tool detects suspicious activity or an abnormal security event. The event data is then ingested into the SIEM. From there, information security professionals analyze the data to determine if it is a threat to the network.
Event Log Collection
Similar to a SIEM an IDS can keep event logs, however, it does not have the capabilities of a SIEM to centralize and correlate event data.
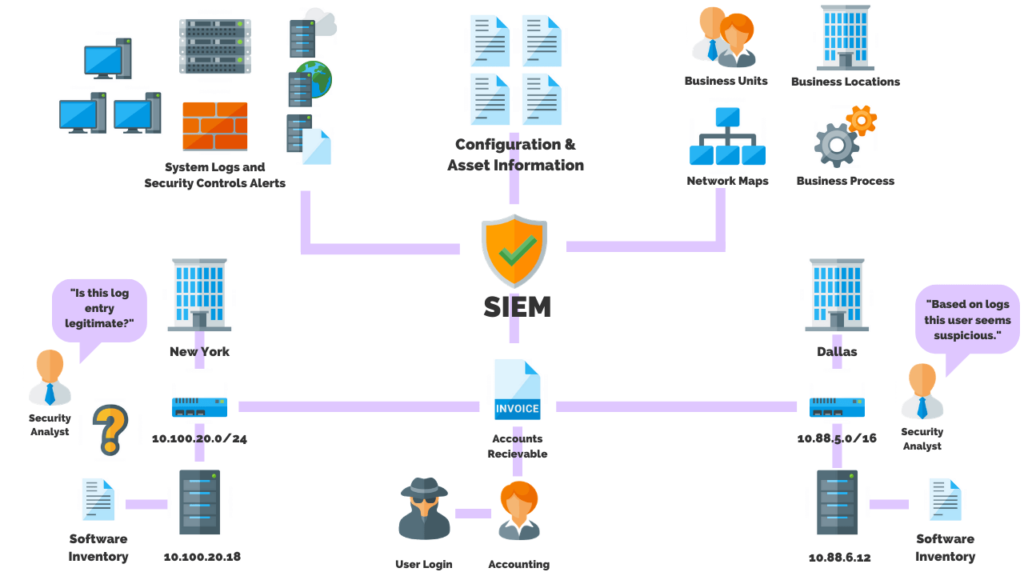
The main benefits of using an SIEM for log collection over an IDS include:
- Your Asset Management system only sees applications, business processes, and administrative contacts.
- Your Network Intrusion Detection System (IDS) only understands Packets, Protocols, and IP Addresses.
- Your Endpoint Security system only sees files, usernames, and hosts.
- Your Service Logs show user sessions, transactions in databases, and configuration changes.
- File Integrity Monitoring (FIM) systems only see changes in files and registry settings.
Article by