Previous
FluBot Android Malware
Spreading Aggressively
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Dalibor Gašić / Last Updated: 6/30/2022
Reviewed By: Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
What Happened?
We were able to encounter this malware for the first time at the end of 2020, while it reached its full potential in the middle of 2021, it went viral all over the world primarily on Android phones.
While most newspapers wrote that this was Android malware, the victims also appeared on iOS.
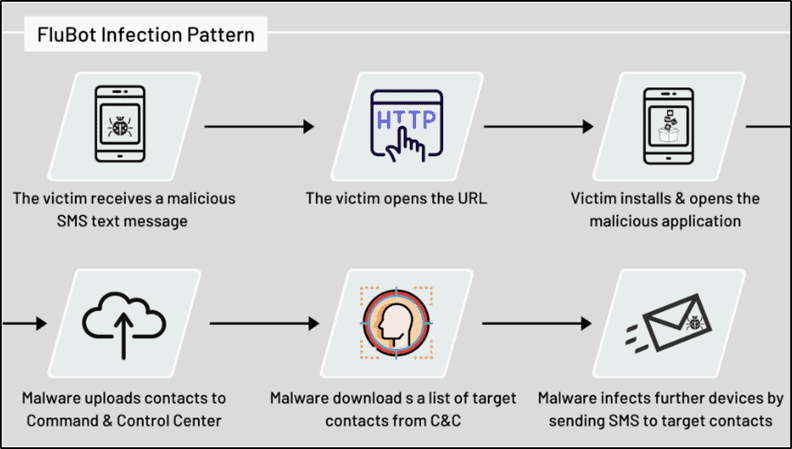
- The victim receives an SMS on her phone with the information that she received the package or listens to a fake voice mail message.
- The malicious message contains a link to a website containing malware, disguised as the delivery company’s application.
- The victim downloads and installs the application.
- Attackers then use this access to steal banking app credentials or cryptocurrency account details and disable built-in security mechanisms.
- In addition to the above, the malware uploads the victim’s contacts to its C&C (Command & Control) server.
- The C&C server sends a list of phone numbers to the victim’s device.
- The victim’s device sends text messages to these numbers, which are other potential victims.
To avoid detection, the victim device sends messages to other numbers but not to those in its phonebook.
International Cooperation Stopping FluBot
In May 2022, this malware was stopped by international cooperation between Europol and law enforcement agencies from:
- Australia: Australian Federal Police
- Belgium: Federal Police (Federale Politie / Police Fédérale)
- Finland: National Bureau of Investigation (Poliisi)
- Hungary : National Bureau of Investigation (Nemzeti Nyomozó Iroda)
- Ireland: An Garda Síochána
- Romania: Romanian Police (Poliția Română)
- Sweden: Swedish Police Authority (Polisen)
- Switzerland: Federal Office of Police (fedpol)
- Spain: National Police (Policia Nacional)
- Netherlands: National Police (Politie)
- United States: United States Secret Service
These few countries were coordinated by Europol’s European Cybercrime Centre (EC3), where since the first appearance of this malware (2020).
Specifically, EC3 teamed with national investigators in affected countries to establish a joint strategy and provided digital forensic support, as well as facilitated the exchange of operational information across various national entities, the agency said.
Who Is Responsible For The FluBot Malware?
Although there have been no official arrests responsible for this malware and attacks around the world, the international law-enforcement team will continue to seek the individuals behind the campaign, who are still at large, according to Europol.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
What Applications Have Been Hit By FluBot?
In the research so far, some of the following applications have been hit:
- Bankinter – com.bankinter.launcher
- BBVA – com.bbva.bbvacontigo
- Cajasur– com.cajasur.android
- Grupo Cooperativo Cajamar – com.grupocajamar.wefferent
- Imagin Bank – com.imaginbank.app
- Kutxabank – com.kutxabank.android
- Ruralvia – com.rsi
- Laboral – com.tecnocom.cajalaboral
- Banco Santander – es.bancosantander.apps
- Bankia – es.cm.android
- Evo Banco – es.evobanco.bancamovil
- IberCaja – es.ibercaja.ibercajaapp
- Liber Bank – es.liberbank.cajasturapp
- Openbank – es.openbank.mobile
- Pibank – es.pibank.customers
- Unicaja Banco – es.univia.unicajamovil
- ING – www.ingdirect.nativeframe
And two related to crypto currency trading platforms:
- Binance – com.binance.dev
- Coinbase – com.coinbase.andriod
How To Prevent The FluBot Malware
- Back up all your data periodically. If you have reason to believe your Android phone is infected, factory-reset your device, but be very careful because this will also erase all your unsaved personal data.
- Restore your device using a backup made before you were infected and change all your passwords.
- Treat all mobile links with extreme caution.
- Watch out for suspicious text messages.
- Fight the urge to click on links you receive via SMS, even if the message seems to come from a reliable source.
- Track your deliveries independently.
- Don’t log in to pages through links you receive in messages.
- Don’t install apps or updates through suspicious links.
- Don’t rush into any action, even if the message seems urgent.
Related Articles:

Dalibor Gašić
Dalibor is a Senior Security Engineer with experience in penetration testing having recently served over 8 years in the Ministry of Internal Affairs in the Department of Cyber Security in Serbia.




 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO