Previous
The No More Ransomware Project
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Dalibor Gašić / Last Updated: 8/29/2022
Reviewed By: Eva Georgieva & Dušan Trojanović
View Our: Editorial Process
Table Of Contents
Summary Of The Research
- In mid-July 2016, several cybersecurity companies, public and private organizations, pooled their resources and knowledge to launch the “No More Ransom” platform to help people affected by ransomware malware.
- The No More Ransom project includes 188 partners worldwide, including some well-known companies: Amazon Web Services, Barracuda Networks, CheckPoint, Cisco, Emsisoft, Bitdefender, ESET, Interpol, and other law enforcement, public and private entities.
- No More Ransom’s Crypto Sheriff Tool helps you find a free decryption program by uploading two encrypted files and the ransomware note and tries to match them with a list of available tools.
- The best cure against ransomware remains diligent prevention. On our side, we have advice for regular users and mitigation steps for business.
- The general advice is not to pay the ransom. If you send your money to the cyber criminals, you only confirm that the ransomware works, and there is no guarantee that you will receive the needed decryption key in return.
What Is The No More Ransomware Project?
In mid-July 2016, several cybersecurity companies, and public and private organizations, pooled their resources and knowledge to launch the “No More Ransom” platform to help people affected by ransomware malware.
In the beginning, it was a partnership between law enforcement agencies (Europol and the Dutch police) and IT security companies (Kaspersky and McAffee).
At the time, there were only four decryption tools on the platform that could decrypt different types of ransomware, and it was only available in English.
For the part of the audience that doesn’t know what ransomware is, ransomware is still one of the most dangerous malware today, locks files, and cyber criminals demand a certain amount of money to send you the keys.
Today, the No More Ransom project includes 188 partners worldwide, including some well-known companies: Amazon Web Services, Barracuda Networks, CheckPoint, Cisco, Emsisoft, Bitdefender, ESET, Interpol, and other law enforcement, public and private entities, which can be found at the link above: https://www.nomoreransom.org/en/partners.html.
How Does It Work?
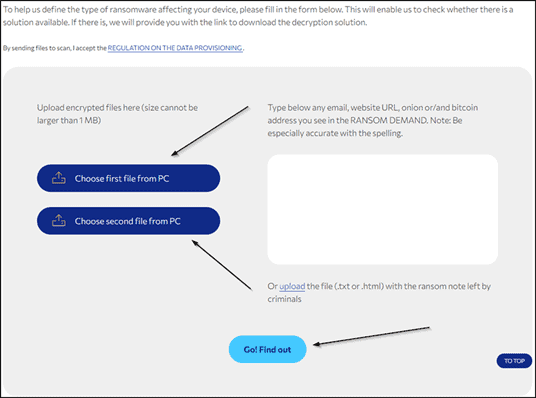
Apart from the fact that on this website we can find all the necessary information about what ransomware is, all the latest types of this malware, we can also find tool Crypto Sheriff.
No More Ransom’s Crypto Sheriff Tool helps you find a free decryption program by uploading two encrypted files and the ransomware note and tries to match them with a list of available tools.
If it finds a match, it will tell you about a suitable ransomware decryption program for your encrypted files, along with detailed instructions on how to unlock them.
If no decryption program is found, you are advised to search for a match again in the future, as new decryption tools are added regularly.
This platform regularly provides new decryption tools for the latest malware strains.
To date, this platform has helped over 1.5 million people successfully decrypt their devices without the criminals having to pay for it.
The portal is available in 37 languages to better help ransomware victims around the world.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
Prevention Is Still The Key
The best cure against ransomware remains diligent prevention. On our side, we have advice for regular users and mitigation steps for business:
- Regularly back up data stored on your computer, so a ransomware infection wouldn’t destroy your personal data forever.
- Avoid sharing personal data.
- Be meticulous with sensitive data.
- Consider using multi-factor authentication on your important online accounts.
- Be wary while browsing the internet and do not click on suspicious links, pop-ups, or dialogue boxes.
- Browse and download only official versions of software and always from trusted websites.
- Use robust security products to protect your system from all threats, including ransomware.
- Never connect unfamiliar USB sticks to your systems.
- Use a Virtual Private Network (VPN) when using public WiFi.
- Ensure that your security software and operating system are up to date.
- Do not use high privilege accounts (accounts with administrator rights) for daily business.
- Enable the ‘Show file extensions’ option in the Windows settings on your computer.
- Turn on local firewall.
- Keep corporate devices’ operating systems and applications updated.
- Apply the latest security patches and ensure critical software is up to date, including on mobile devices.
- Enable the option for automated updates if possible. Having the latest updates will ensure that the devices are not only more secure, but also perform better.
- Assess whether antivirus and anti-malware products are required and keep them up to date.
- Conduct regular vulnerability scans to ensure that your operating systems work efficiently.
- Consider using a centralized patch management system and use a risk-based assessment strategy to determine which systems should be part of the patch management program.
- Regularly back up your systems, online and offline. Up to date backups are the most effective way of recovering from a ransomware attack.
- Ensure that you create offline backups that are kept in a different location (ideally offsite), from your network and systems, and/or in a cloud service designed for this purpose. Keep in mind that ransomware actively targets backups to increase the likelihood of victims paying to retrieve their data.
How We Can All Help
The general advice is not to pay the ransom.
If you send your money to the cyber criminals, you only confirm that the ransomware works, and there is no guarantee that you will receive the needed decryption key in return.
If you are a cyber security company and you are ready to join law enforcement agencies and industry leaders in the fight against ransomware, you are welcome to contact the official website.
Related Articles:

Dalibor Gašić
Dalibor is a Senior Security Engineer with experience in penetration testing having recently served over 8 years in the Ministry of Internal Affairs in the Department of Cyber Security in Serbia.



 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO