Previous
Hertzbleed Attack Impacting
Intel & AMD CPUs
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Dalibor Gašić / Last Updated: 7/31/2022
Reviewed By: Josh Allen, & Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
Summary Of The Attack
- A group of researchers from the University of Texas, the University of Illinois Urbana-Champaign, and the University of Washington, have published an article on their website about a new attack they developed called Hertzbleed.
- Manufacturers Intel and AMD have confirmed that their processors are affected by the Hertzbleed attack.
- This attack is listed in the Common Vulnerabilities and Exposures (CVE) system as CVE 2022-24436 for Intel and 2022-23823 for AMD CPU.
- Neither Intel nor AMD are releasing patches to fix the problem, claim the researchers on their website.
- Neither company responded to questions posed by New Scientist.
What Is The Hertzbleed Attack?
In June 2022, a group of researchers from the University of Texas, the University of Illinois Urbana-Champaign, and the University of Washington, have published an article on their website about a new attack they developed called Hertzbleed.
This attack allows attackers to detect variations in the frequency of CPU using something called Dynamic voltage and frequency scaling or DVFS in short, and steal entire cryptographic keys in that way.
What Is Dynamic Voltage And Frequency Scaling (DVFS)?
DVFS throttles CPUs so they do not go beyond their thermal or performance limits during high workloads. It also reduces power consumption.
As the researchers explain on their website, they prove that attacks can be remotely converted into timing attacks via the power side channel.
This method can be classified as a hardware attack, which is an attack that exploits security holes or other specific vulnerabilities in the hardware.
There are many attacks of this type, but almost all of them require direct access to the target computer – or only to a specific chip. However, Hertzbleed can operate remotely.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
Who Is Impacted By This Attack?
Intel’s security advisory states that all Intel processors are affected. We have experimentally confirmed that several Intel processors are affected, including desktop and laptop models from the 8th to the 11th generation Core microarchitecture.
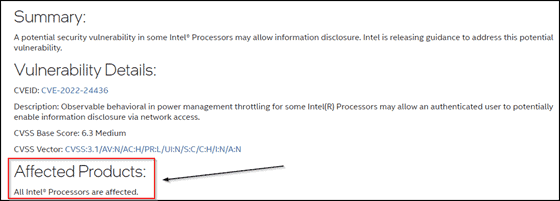
AMD’s security advisory states that several of their desktop, mobile and server processors are affected.
We have experimentally confirmed that AMD Ryzen processors are affected, including desktop and laptop models of the Zen 2 and Zen 3 microarchitectures.

Other processor manufacturers (e.g., ARM) also implement frequency scaling in their products and have been made aware of Hertzbleed.
However, we have not confirmed whether they are affected by Hertzbleed or not.
This attack is listed in the Common Vulnerabilities and Exposures (CVE) system as CVE 2022-24436 for Intel and CVE 2022-23823 for AMD CPUs.
Both Intel and AMD have announced that this vulnerability affects their processors and can be exploited with relatively low privileges.
Both AMD and Intel have stated that they do not intend to release patches as they believe the attacks are not practical outside of a lab environment.
How To Mitigate The Hertzbleed Attack
Both Intel and AMD have provided mitigation assistance by explaining that developers can use masking, hiding, or key rotation to protect against performance analysis-based frequency side-channel attacks.
The researchers also note that you can disable this feature on Intel CPUs with Turbo Boost and AMD CPUs with Turbo Core or Precision Boost, as it is basically DVFS with a user-friendly name.
However, keep in mind that this can affect your PC’s performance, and Intel stated that the attack is still possible even if you disable this feature.
When attacks that watched for changes in a chip’s speed, or frequency, were first discovered in the late 1990s, there was a common fix: write code that only used “time invariant” instructions – that is, instructions that take the same time to carry out regardless of what data is being processed.
This stopped an observer from gaining knowledge that helped them read data. But Hertzbleed can get around this strategy and can be done remotely.
Because this attack relies on the normal operation of a chip feature, not a bug, it could prove tricky to fix.
The researchers say that a solution would be to turn off the CPU throttling feature on all chips, globally, but warn that doing so would “significantly impact performance” and that it may not be possible to fully stop frequency changes on some chips.
Related Articles:

Dalibor Gašić
Dalibor is a Senior Security Engineer with experience in penetration testing having recently served over 8 years in the Ministry of Internal Affairs in the Department of Cyber Security in Serbia.



 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO