Written by:
Jason Fitch, MBA
What Is Cyber Security?
Cyber security is the practice of protecting systems, human resources, and physical assets from attacks. Attacks exploit vulnerabilities or weaknesses. Malicious code is then delivered to access, change, steal, ransom, or destroy sensitive information.
In some cases, the goal of a cyber attack is to disrupt or bring down a network and its business operations.
What Are The Types Of Cyber Security?
There are two types of cyber security:
- Offensive (Red Teaming)
- Defensive (Blue Teaming)
Red Teams are offensive in nature and specialize in attacking systems, networks, human resources, or physical assets with the goal of breaking through security defenses. Blue Teams play defense and maintain the internal network against all cyber attacks and threats.
Somewhere in the middle are Purple teams, which is not a separate team, although it can be. When red teams and blue teams come together to share knowledge from eachother’s discipline they enchance the security capabilities of an organization.
Advanced cyber security programs will perform simulated red team attacks against the blue team’s defenses in order to test the effectiveness of the network’s security.
The purpose of these simulations isn’t for the red team to breakthrough or for the blue team to detect an attack. Instead, the goal is for both teams to share information on how to improve the overall security posture of the organization.
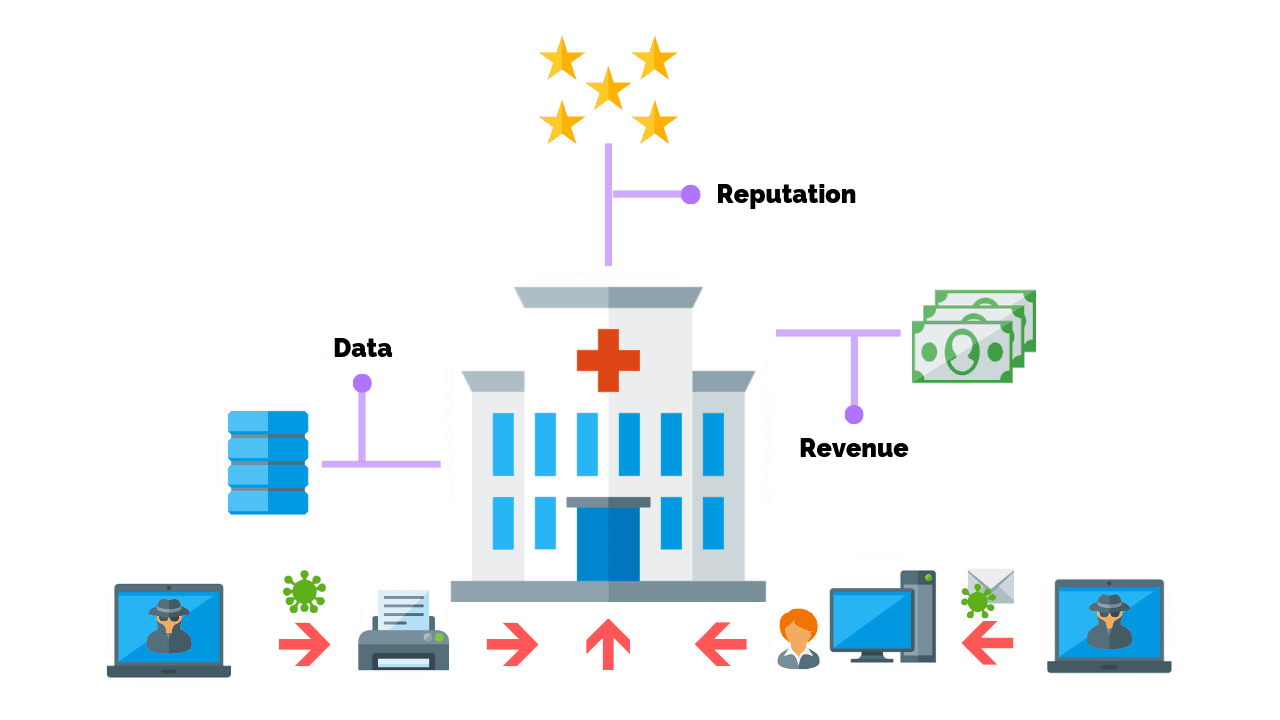
What Does Cyber Security Protect?
Cyber security professionals are responsible for defending against any number of attacks.
For example, there are teams responsible for protecting critical infrastructure like:
- Hospitals
- Traffic lights
- Power grids.
Most businesses are familiar with network security which includes developing password policies, installing anti-virus software on computers and servers, implementing security awareness training, deploying next-generation firewalls, or monitoring internet access.
Other attacks target specific software applications. SQL, a coding language synonymous with databases, could be the target of an SQL injection attack.
Exploiting this vulnerability can result in the bad guys accessing and exfiltrating data from your network.
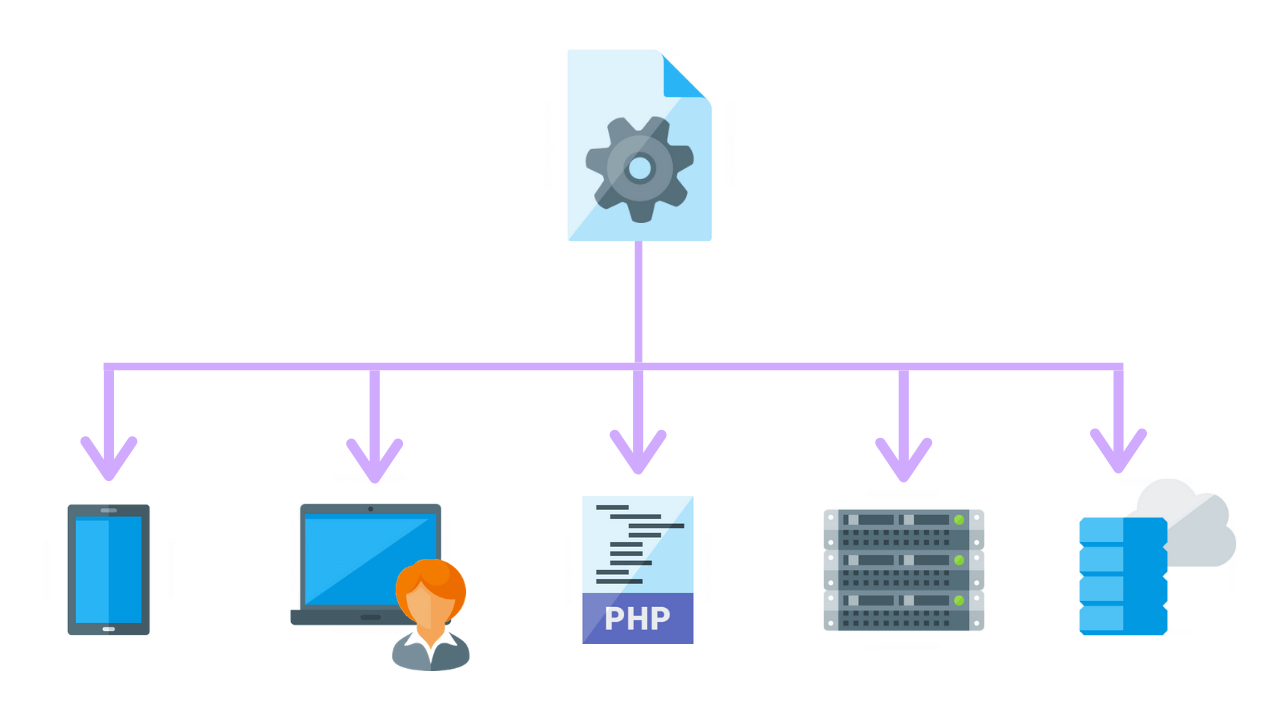
Internet of Things (IoT) devices, or anything that connects wireless to the internet, are also susceptible to a cyber attacks.
This includes appliances, sensors, televisions, wifi routers, and printers.
How Can I Protect Myself From Cyber Attacks?
Cyber attacks are constantly evolving requiring businesses to be proactive in deploying solutions.
To get started, organizations often develop cyber security policies.
Outside of standardizing practices, these policies provide a road map to employees of what to do and when to do it.
Learn More: How To Build A Cyber Security Program
Implementing security awareness training has also risen in popularity, as 98% of cyber attacks rely on social engineering as its entry point into an organization’s network.
The goal of this training is to inform and educate employees on how to identify common attacks used by threat actors.
The wide adoption of these programs owes its success to how effective the training is at mitigating internal risk.
Even with training mistakes still happen. In order to reduce this risk further, businesses often deploy email spam filters and anti-malware filters as the first line of defense against phishing attacks.
The idea is to catch malicious attachments and links to sites containing malicious code before they reach users.
Your systems and devices connected to a network are also at risk if software and patches are not kept up-to-date. Software developers frequently release updates to fix bugs or patch security vulnerabilities.
Vulnerability scans and vulnerability assessments are used to identify weaknesses within your system or network.
Reports are then drafted categorizing the vulnerabilities found along with an action plan for remediating threats.
Continue Reading: How To Prevent Cyber Attacks
Learn How To Secure Your Organization
No matter where your security maturity lies today, this expert written content will help you learn cyber security to build a more secure organization.
These resources are filled with expert interviews, how to guides written by security professionals with real world experience, practical and actionable tips that you can apply today, case studies, and so much more.