How To Prevent A Domain Name Server (DNS) Amplification attack
A domain name server amplification attack is a popular form of DDoS attack that attempts to flood a target system with DNS response traffic
You can prevent a DNS amplification attack by Implementing Source IP Verification on a network device, Disabling Recursion on Authoritative Name Servers, Limiting Recursion to Authorized Clients, and Implementing Response Rate Limiting (RRL) setting on DNS Server.
What Is A DNS Amplification Attack?
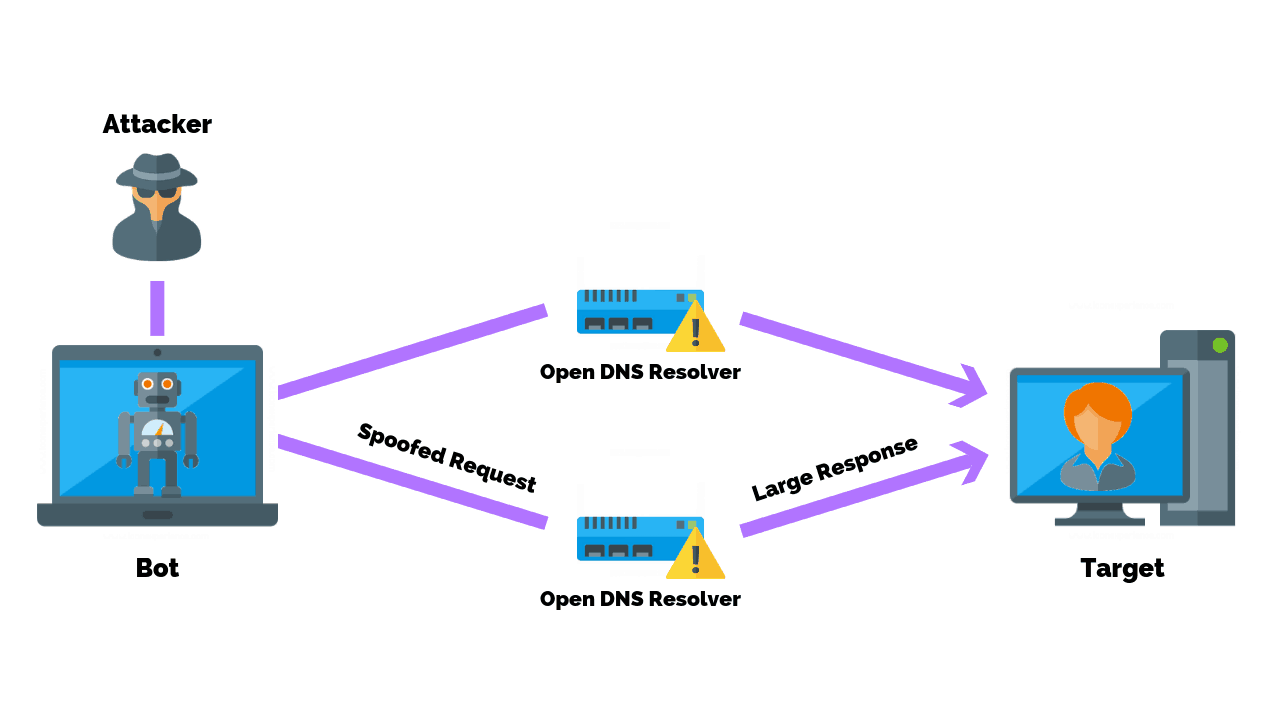
A Domain Name Server (DNS) Amplification attack is a popular form of Distributed Denial of Service (DDoS), in which attackers use publically accessible open DNS servers to flood a target system with DNS response traffic.
The primary technique consists of an attacker sending a DNS name lookup request to an open DNS server with the source address spoofed to be the target’s address.
When the DNS server sends the DNS record response, it is sent instead to the target. Attackers will typically submit a request for as much zone information as possible to maximize the amplification effect.
In most attacks of this type observed by US-CERT, the spoofed queries sent by the attacker are of the type, “ANY,” which returns all known information about a DNS zone in a single request.
Because the size of the response is considerably larger than the request, the attacker is able to increase the amount of traffic directed at the victim.
By leveraging a botnet to produce a large number of spoofed DNS queries, an attacker can create an immense amount of traffic with little effort.
Additionally, because the responses are legitimate data coming from valid servers, it is extremely difficult to prevent these types of attacks.
Read More: 10 Cyber Security Trends You Can’t Ignore In 2021
How Do You Prevent A DNS Amplification Attack?
You can prevent DNS Amplification attacks by:
- Implementing Source IP Verification on a network device.
- Disabling Recursion on Authoritative Name Servers.
- Limiting Recursion to Authorized Clients.
- Implementing Response Rate Limiting (RRL) setting on DNS Server.
Related Articles:


