The main difference between vulnerability assessments and penetration testing is that vulnerability assessments identify potential weaknesses in an organization’s IT infrastructure through high-level security scans.
Penetration testing goes a step further by simulating real-world attacks to test the effectiveness of security measures and provide a more in-depth analysis of the organization’s security posture.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

Unfortunately, many organizations lack the resources to keep pace with growing security concerns.
This can lead to unpatched vulnerabilities that could potentially put your organization at risk for an attack.
A study by IBM showed that the average time to detect a breach is over 200 days, highlighting the need for an effective solution to manage vulnerabilities.
In this article, I will explain the key differences between vulnerability assessments and penetration testing and discuss how they can work together.
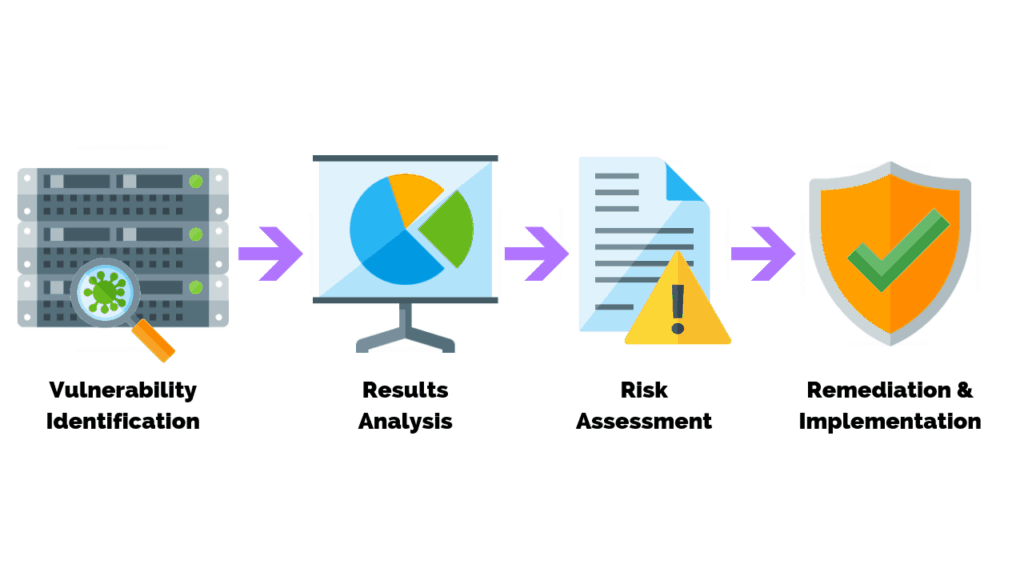
What Is A Vulnerability Assessment?
Vulnerability assessments are security scans that identify potential weaknesses in an organization’s IT infrastructure.
To obtain the most accurate and comprehensive results, credentialed scanning is performed against each host.
The assessment provides a high-level overview of an organization’s security posture and highlights areas that need attention.
Conducting a vulnerability assessment is just part of a vulnerability management program.
A complete vulnerability management program includes:
- Ongoing assessments
- Remediation
- Continuous monitoring
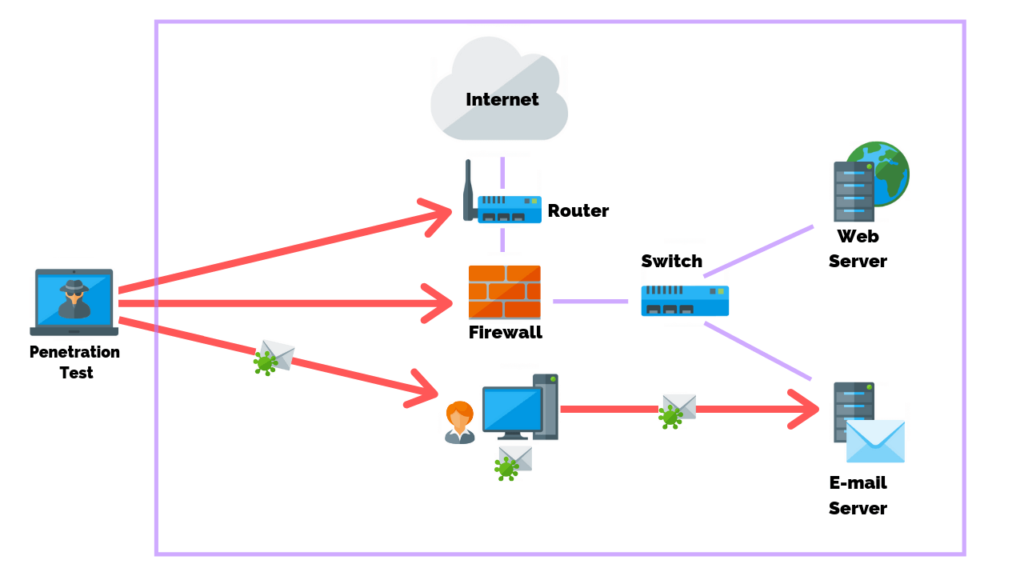
What Is A Penetration Test?
A penetration test is a comprehensive simulation used to test the effectiveness of an organization’s security measures.
It verifies whether or not vulnerabilities can be exploited and provides a more in-depth analysis of the organization’s security posture.
A penetration test should also be approved by management before the commencement of any activity.
Combining Vulnerability Assessments And Penetration Testing
By combining vulnerability assessment and penetration testing you can realize a:
- A comprehensive view of the security posture.
- Faster mean time to remediation.
- Reduced risk across the IT infrastructure.
- Streamlined patch management process.
Unfortunately, quarterly vulnerability assessments and annual penetration tests are no longer sufficient to stay ahead of cyber threats.
Learn More: How To Prevent Cyber Attacks
At PurpleSec, we believe that continuous penetration testing and automating vulnerability management is the key to achieving a truly secure network.
This solution integrates both services, feeding the results from your penetration test directly into your vulnerability management process.
What Security Policies Do I Need?
In order to ensure the effectiveness and success of your security program, it is crucial to have clear documentation for your vulnerability assessment and penetration test processes.
Policies should be written up as part of standard practice with any security program to ensure that all members of your organization are on the same page and understand the expectations and requirements of your security efforts.
Vulnerability Assessment Policy
A vulnerability assessment policy outlines the procedures and guidelines for conducting regular vulnerability scans on your network and assets.
This includes the:
- Scope of the assessment.
- Frequency of assessments.
- Methods for reporting and remediation.
Penetration Testing Policy
A penetration testing policy outlines the procedures and guidelines for conducting regular penetration tests of your network systems and assets.
This includes the:
- Scope of the test
- Testing frequency
- Methods for reporting and remediation.
How Does The Reporting Differ?
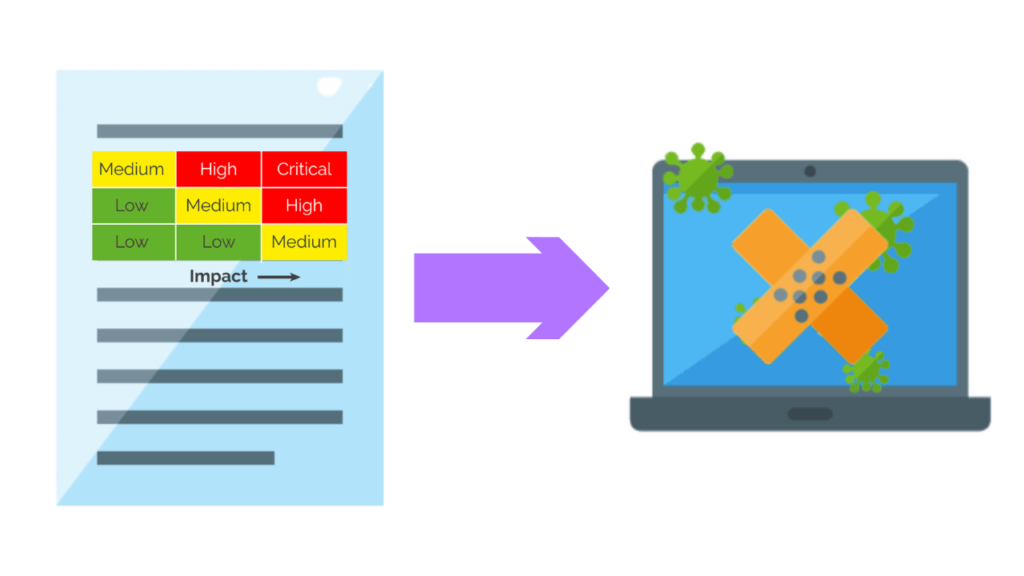
A vulnerability assessment report is the result of a risk-based approach to managing vulnerabilities.
These reports organize scan results and prioritize the vulnerabilities that need to be remediated.
A penetration test report will show a more in-depth analysis from an offensive security professional.
The penetration test report will not only show the vulnerabilities, but it will also demonstrate how an attacker could exploit them.
Vulnerability Assessment Report
A vulnerability assessment report is usually more straightforward, listing all vulnerabilities found during the scan, prioritizing them based on severity, and providing recommendations for remediation,
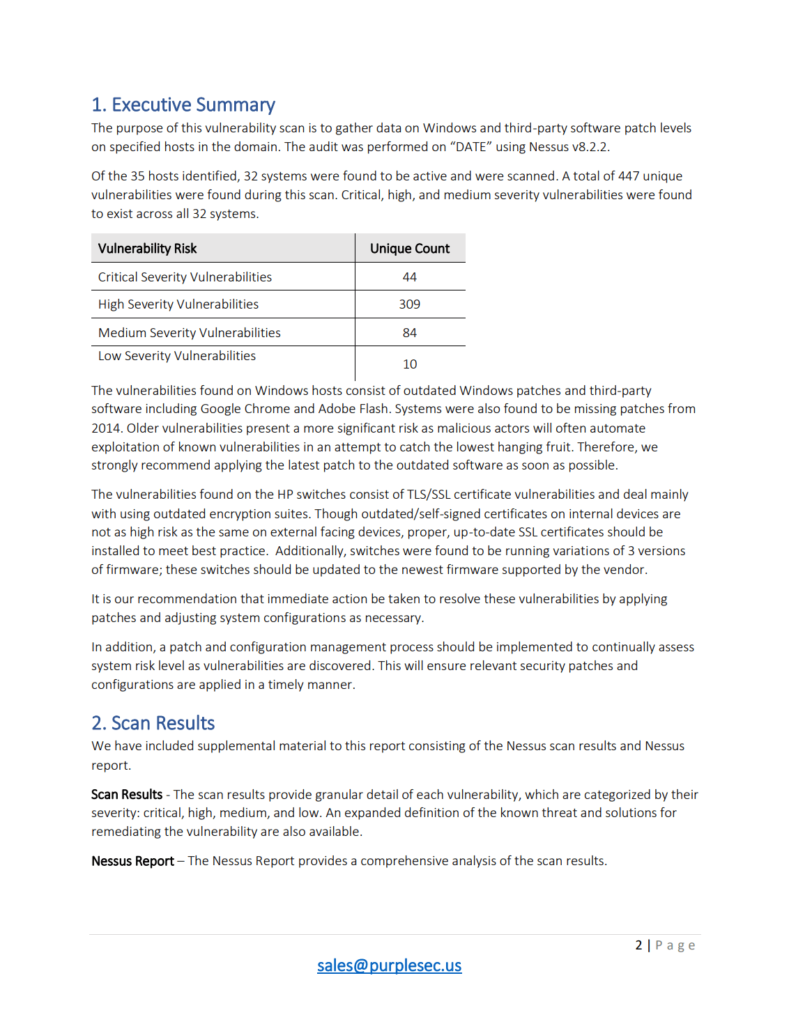
To get the most out of a vulnerability assessment report, look for the following information:
- Comprehensive list of vulnerabilities.
- A clear assessment of the risk associated with each vulnerability.
- Actionable recommendations for remediation.
Learn More: How To Automate The Vulnerability Remediation Process
Penetration Test Report
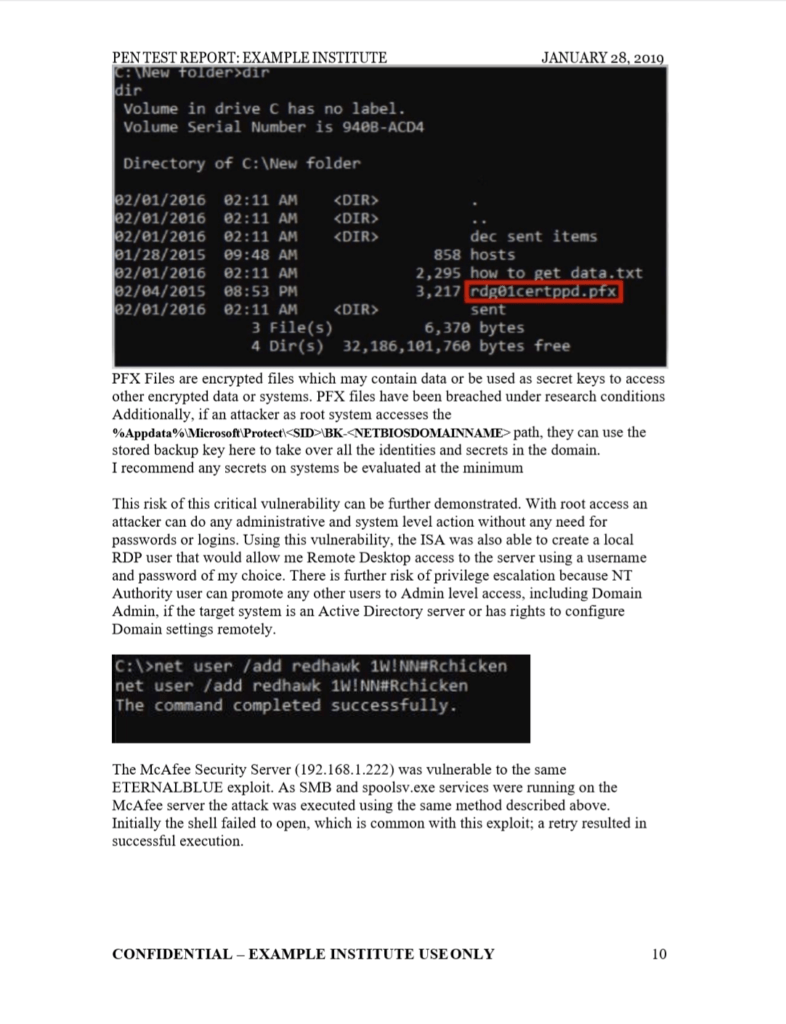
The report should include a:
- Detailed methodology.
- List of vulnerabilities.
- Demonstration of how each vulnerability can be exploited.
In addition, the report should provide recommendations for remediation and prioritize the vulnerabilities based on their severity.
The Value of PurpleSec's Vulnerability Management Services
With PurpleSec’s vulnerability management services, you no longer have to worry about time-consuming and complex vulnerability scans.
- Automation: Reduces human error, providing you with a more efficient and effective solution.
- Technical expertise: By leveraging our skilled team of experts, you will be able to focus on other aspects of your business, without sacrificing your security posture.
- Streamlined process: Our platform provides a single view of your security risk, making it easier for you to understand and manage vulnerabilities.
- Continuous Monitoring: Our experienced team of experts will continuously monitor your systems and provide real-time insights, helping you to quickly identify and remediate potential vulnerabilities.
As a result, your systems are protected and secure, reducing the risk of data breaches or other security incidents.
Wrapping Up
Vulnerability assessments and penetration testing are critical components of any comprehensive security program.
In this article, we have explored the key benefits of combining these two approaches.
With a complete view of the security risk impacting your business systems, you can now take proactive steps to remediate vulnerabilities before they can be exploited by attackers.
Managing a vulnerability management tool to assess your in-house infrastructure can be a time-consuming and complex process, however, it can be accomplished by implementing a platform that is designed for this very purpose.
PurpleSec’s managed vulnerability management platform streamlines the process and improves efficiency.
With real-time insights and recommendations from our experienced team of experts, organizations like yours can stay ahead of evolving cyber threats and free up their internal teams to focus on other critical tasks.
To learn more about how our platform can help your organization, let’s schedule a demo today.
Article by