How To Prevent Network Attacks
+ (19 Types Of Attacks Explained)
Learn how PurpleSec can help mitigate the latest cyber attacks and improve security ROI.
Authors: Michael Swanagan, CISSP, CISA, CISM / Last updated: 10/17/22
Reviewed By: Rich Selvidge, CISSP, Seth Kimmel, OSCP
View Our: Editorial Process
Network attacks can be prevented by Using an Anti-virus solution, implementing a network monitoring tool, Avoiding trust relationships with unknown entities, Enabling cryptographic network protocols, Blocking directed broadcast traffic coming into the network, Deploying inline or scrubbing DDoS mitigation technology, and more.
Preventing Network Attacks
Network security attacks have become more common in recent years in part because small and mid-sized businesses are not making investments into securing their systems fast enough.
As a result, hackers target businesses because their systems are often easier to compromise. Other reasons include a rise in hacktivism, bring your own device (BYOD) use, and cloud-based applications.
This comprehensive list is by no means exhaustive. It is designed to provide context for the scale of techniques and types of security controls to prevent network attacks.
Common Types Of Network Attacks
A network attack is an attempt to exploit a vulnerability or weakness on a network or its systems including servers, firewalls, computers, routers, switches, printers, and more. The goal of a network attack can be to steal, modify, or remove access to valuable data. Or, it could be to bring down a network.
Common types of network attacks include:
- Denial of Service (DoS)
- Distributed Denial of Service (DDoS)
- Buffer Overflow Attacks
- Ping Attacks
- SYN Flood
- DNS Amplification
- Back Door
- Spoofing
- Smurf Attack
- TCP/IP Hijacking
- Man In The Middle Attacks
- Replay Attacks
- DNS Poisoning
- ARP Poisoning
- Domain Kiting
- Typosquatting
- Client Side Attacks
- Watering Hole Attacks
- Zero Day Attacks
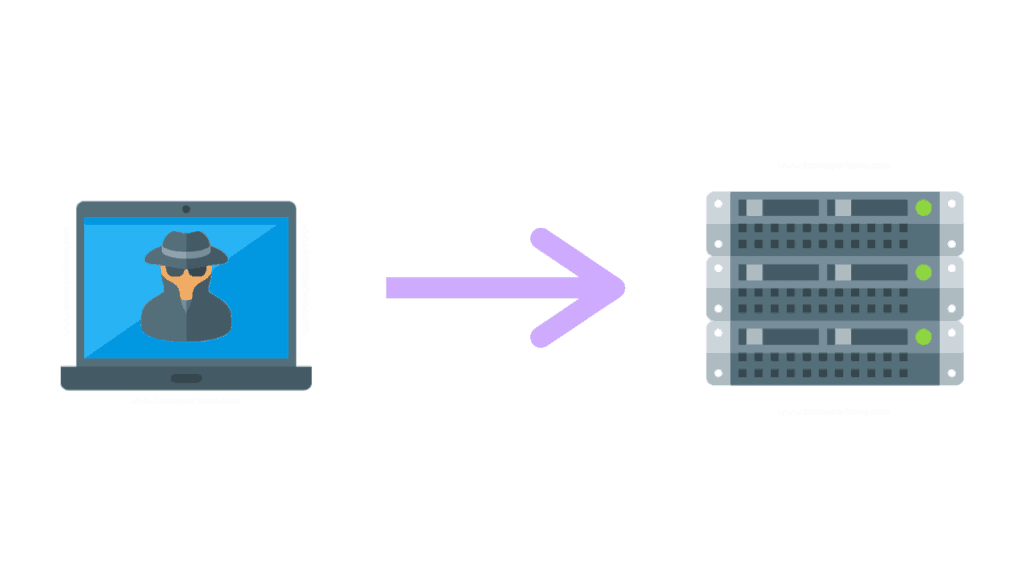
Denial Of Service (DoS)
In a Denial Of Service (DoS) attack a malicious threat actor overloads a server with data preventing valid request coming from real clients on the network.
The server uses resources (CPU/RAM) to process each request, and when overloaded, the performance of the system can be slowed down to a crawl.
A DoS attack can also be performed on entire networks because the attack is targeted at the central router or firewall.
As a result, network bandwidth is compromised, which denies access to all systems on that network, not just the one.
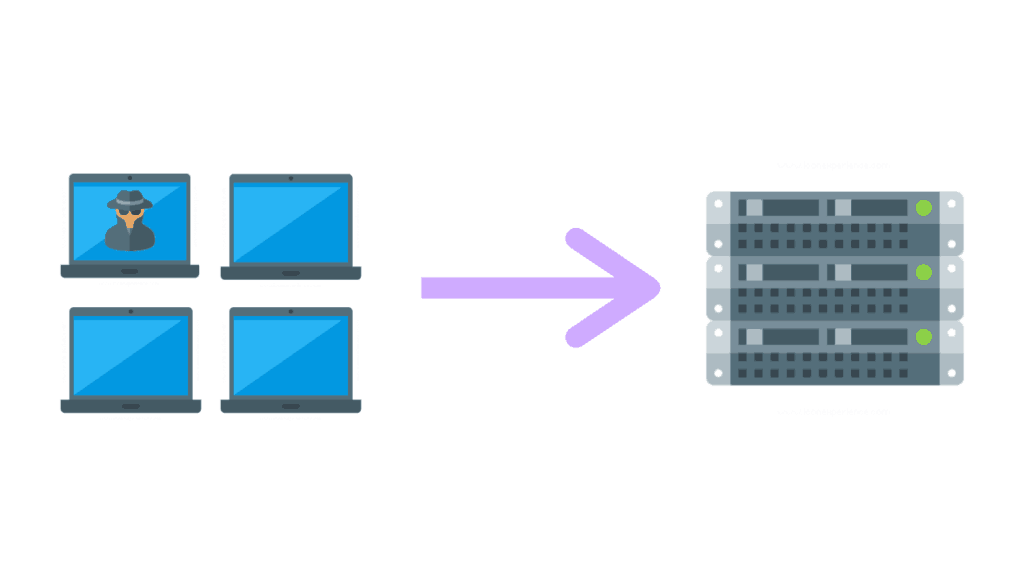
Distributed Denial Of Service (DDoS)
A Distributed Denial Of Service Attack (DDoS) is an attack on a system that is launched from multiple sources and is intended to make a computer’s resources or services unavailable.
DDoS attacks typically include sustained, abnormally high network traffic.
The Mirai Botnet that launched a DDoS attack against the internet service provider Dyn causing outages for popular websites including Airbnb, Amazon, CNN, HBO, and Reddit.
It did this by connecting and controlling thousands of wireless internet connected devices and used their resources to power the attack against their servers.
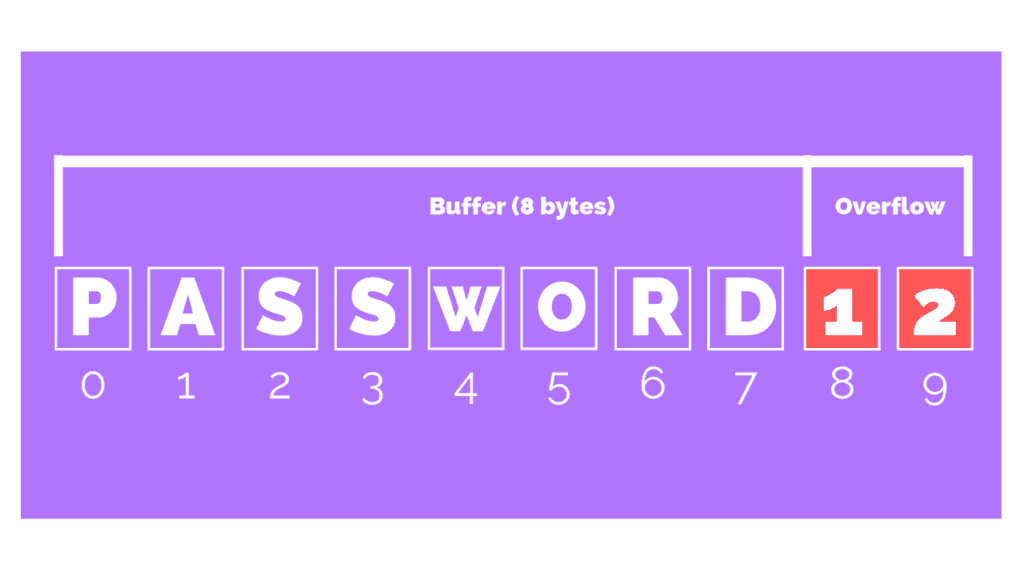
Buffer Overflows
In a buffer overflow attack, an application receives more input than it expects. As a result, the error exposes the system memory to a malicious threat.
While a buffer overflow itself doesn’t cause damage, it does expose a vulnerability.
Threat actors are then able to access memory locations beyond the application’s buffer, which enables them to write malicious code into this area of memory.
When the application is executed the malicious code is launched.
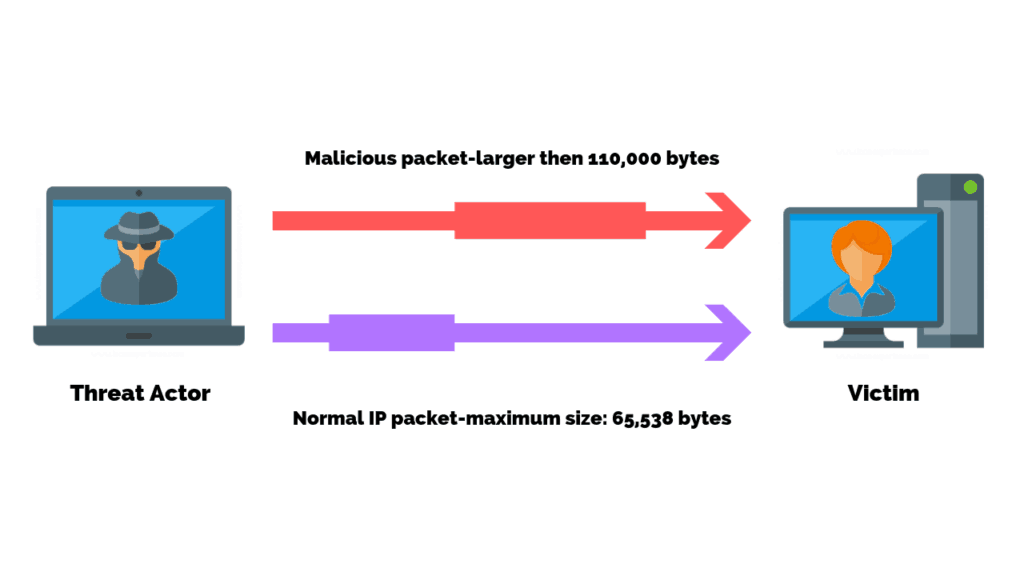
Ping Attacks
A ping attack is an attack designed to overwhelm or flood a targeted device with ICMP (Internet Control Message Protocol) pings.
In normal situations, a ping is used to check connectivity between a source and a destination devices by way of ICMP echo-requests and echo-reply messages.
A Ping Attack on the other hand purposely floods the target device with requests packets.
The destination device is forced to respond with an equal number of reply packets and eventually cannot keep up with the volume of requests.
This causes the target to become inaccessible to normal traffic and unresponsive to normal ping requests.
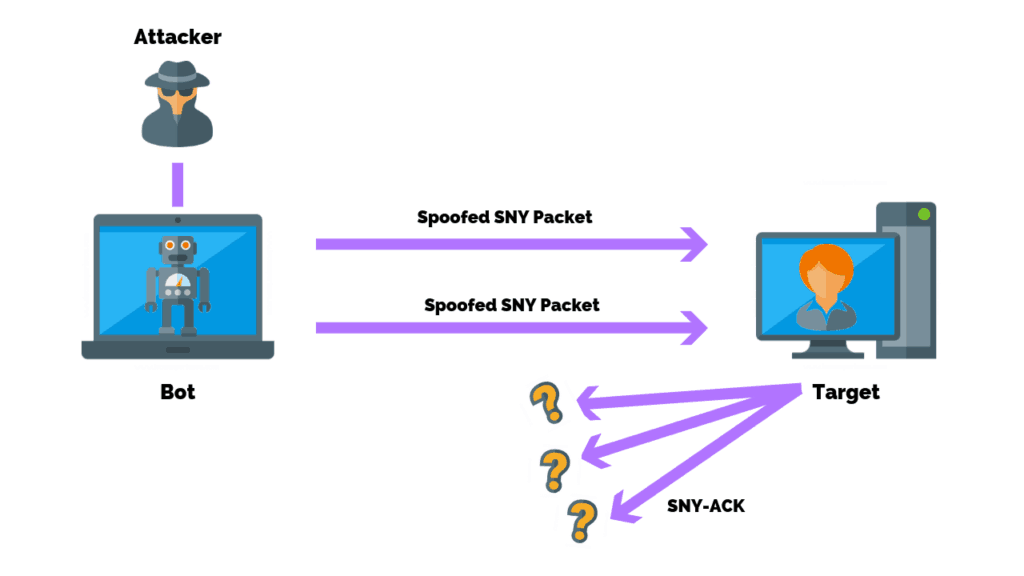
SYN Flood
For every client and server connection using the TCP protocol, a required three-way handshake is established, which is a set of messages exchanged between the client and server.
The handshake process is listed below:
- The three-way handshake is initiated when the client system sends a SYN message to the server.
- The server then receives the message and responds with a SYN-ACK message back to the client.
- Finally, the client confirms the connection with a final ACK message.
A SYN flood manipulates the handshake which allows the attacker to rapidly initiate a connection to a server without finalizing the connection.
The server has to spend resources waiting for half-opened connections, which can consume enough resources to make the system unresponsive to legitimate traffic.
The SYN flood is a form of a denial-of-service attack.
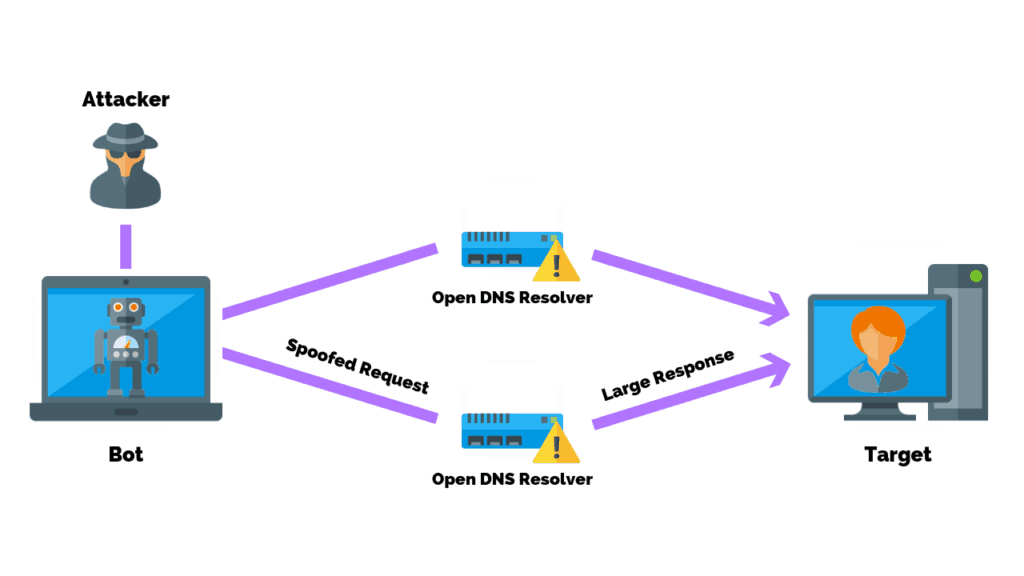
DNS Amplification
A Domain Name Server (DNS) Amplification attack is a popular form of Distributed Denial of Service (DDoS), in which attackers use publically accessible open DNS servers to flood a target system with DNS response traffic.
The primary technique consists of an attacker sending a DNS name lookup request to an open DNS server with the source address spoofed to be the target’s address.
When the DNS server sends the DNS record response, it is sent instead to the target. Attackers will typically submit a request for as much zone information as possible to maximize the amplification effect.
In most attacks of this type observed by US-CERT, the spoofed queries sent by the attacker are of the type, “ANY,” which returns all known information about a DNS zone in a single request.
Because the size of the response is considerably larger than the request, the attacker is able to increase the amount of traffic directed at the victim.
By leveraging a botnet to produce a large number of spoofed DNS queries, an attacker can create an immense amount of traffic with little effort.
Additionally, because the responses are legitimate data coming from valid servers, it is extremely difficult to prevent these types of attacks.
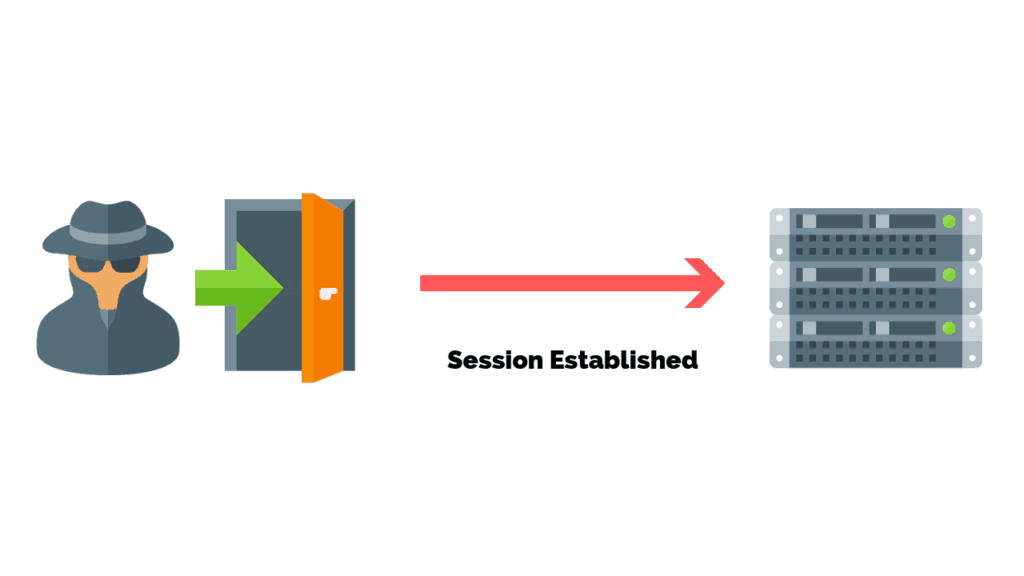
Back Door
A backdoor is a malware type that negates normal authentication procedures to access a system.
As a result, remote access is granted to resources within an application, such as databases and file servers, giving perpetrators the ability to remotely issue system commands and update malware.
Backdoor installation is achieved by taking advantage of vulnerable components in a web application. Once installed, detection is difficult as files tend to be highly obfuscated.
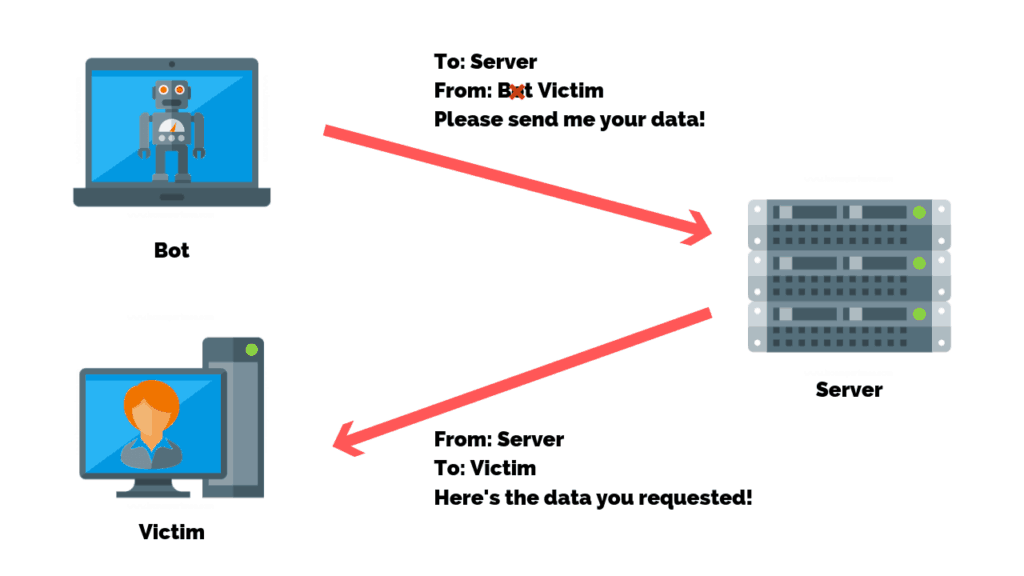
Spoofing Attack
A spoofing attack occurs when a malicious party impersonates another device or user on a network in order to launch attacks against network hosts, steal data, spread malware or bypass access controls.
There are several different types of spoofing attacks that malicious parties can use to accomplish this. Some of the most common methods include IP address spoofing attacks, ARP spoofing attacks and DNS server spoofing attacks.
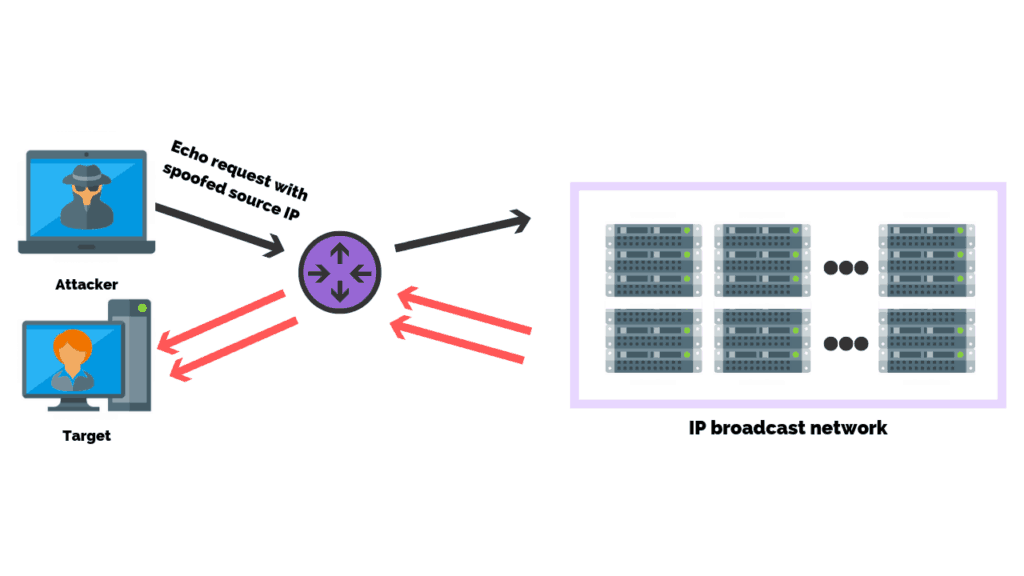
Smurf Attack
A Smurf attack is a form of a DDoS attack that causes packet flood on the victim by exploiting/abusing ICMP protocol. When deployed, large packets are created using a technique called “spoofing”.
The phony source address that is now attached to these packets becomes the victim, as their IP is flooded with traffic. The intended result is to slow down the target’s system to the point that it is inoperable and vulnerable.
The Smurf DDoS Attack took its name from an exploit tool called Smurf widely used back in 1990s. The small ICMP packet generated by the tool causes big trouble for a victim, hence the name Smurf.
Smurf attacks are an old technique but remain relevant due to the popularity of deployment and necessary preemptive prevention tactics.
You can prevent a Smurf Attack by:
• Blocking directed broadcast traffic coming into the network
• Configuring hosts and routers not to respond to ICMP echo requests.
• Deploying inline or scrubbing DDoS mitigation technology
• Ingress filtering can be used to examine all packets that are moving inbound.
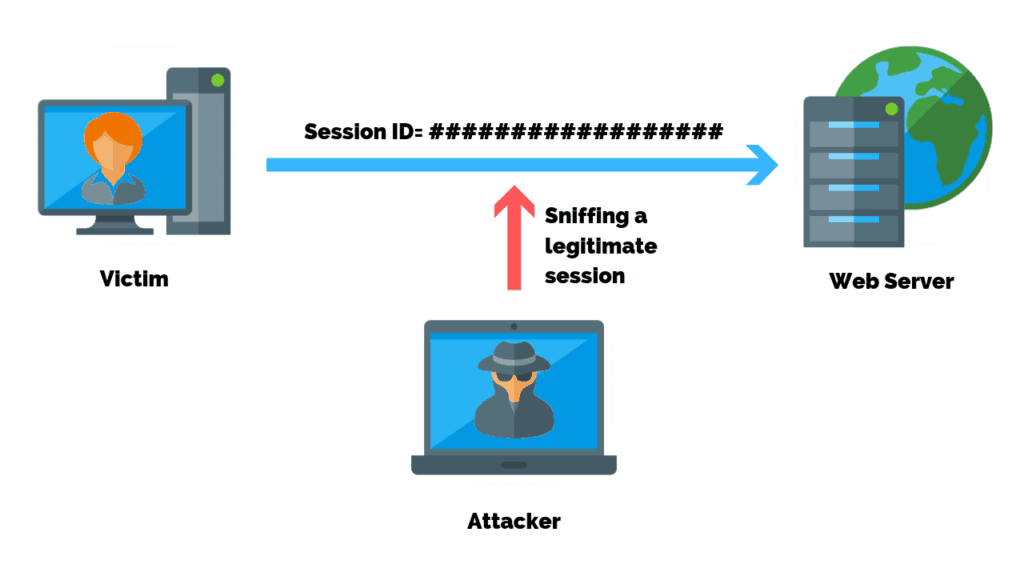
TCP/IP Hijacking
TCP Hijacking is a cyber-attack in which an authorized user gains access to a legitimate connection of another client in the network. Having hijacked the TCP/IP session, the attacker can read and modify transmitted data packets, as well as send their own requests to the addressee.
The intruder can determine the IP addresses of the two-session participants, make one of them inaccessible using a DoS (Denial of Service) attack, and connect to the other by spoofing the network ID of the former.
You can prevent TCP/IP Hijacking by:
- Using SSL when authenticating users or performing sensitive operations.
- Regenerating the session id whenever the security level changes (such as logging in). You can even regenerate the session id every request if you wish.
- Implementing session timeouts.
- Storing authentication details on the server and do not send details such as a username a cookie.
- Locking down access to the sessions on the file system or use custom session handling.
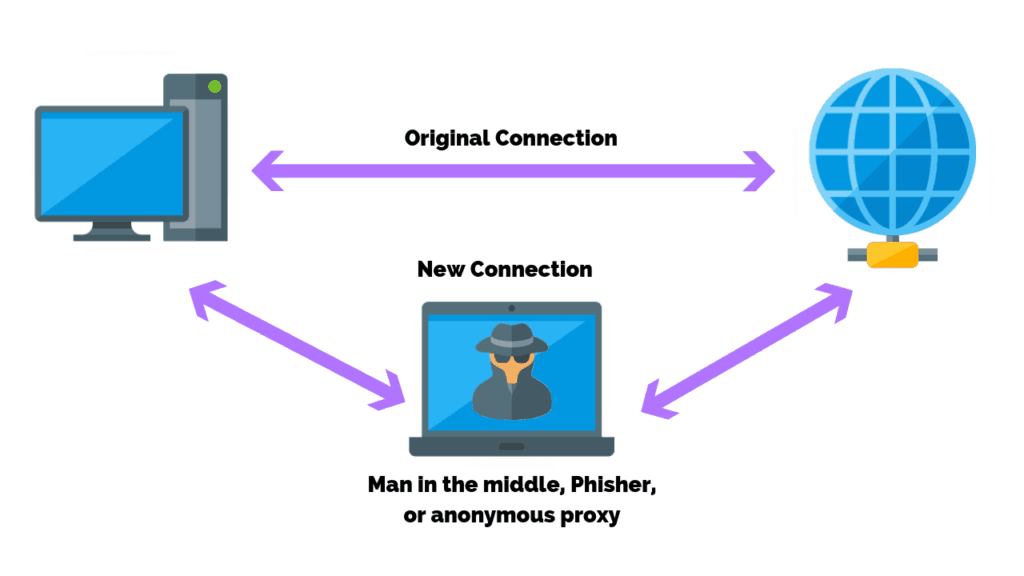
Man In The Middle Attacks
A Man-in-the-Middle (MitM) attack is when an attacker intercepts communications between two parties either to secretly eavesdrop or modify traffic traveling between the two. Attackers might use MitM attacks to steal login credentials or personal information, spy on the victim, or sabotage communications or corrupt data.
MitM attacks consist of sitting between the connection of two parties and either observing or manipulating traffic. This could be through interfering with legitimate networks or creating fake networks that the attacker controls. Compromised traffic is then stripped of any encryption in order to steal, change or reroute that traffic to the attacker’s destination of choice.
You can prevent a MITM Attack by:
- Incorporating the latest version of encryption protocols such as TLS.1.3 on infrastructure assets.
- Training staff not to use open public Wi-Fi or Wi-Fi offerings at public places where possible.
- Training staff to recognize browser warnings from sites or connections that may not be legitimate.
- Implementing VPNs to help ensure secure connections.
- Implementing multi-factor authentication.
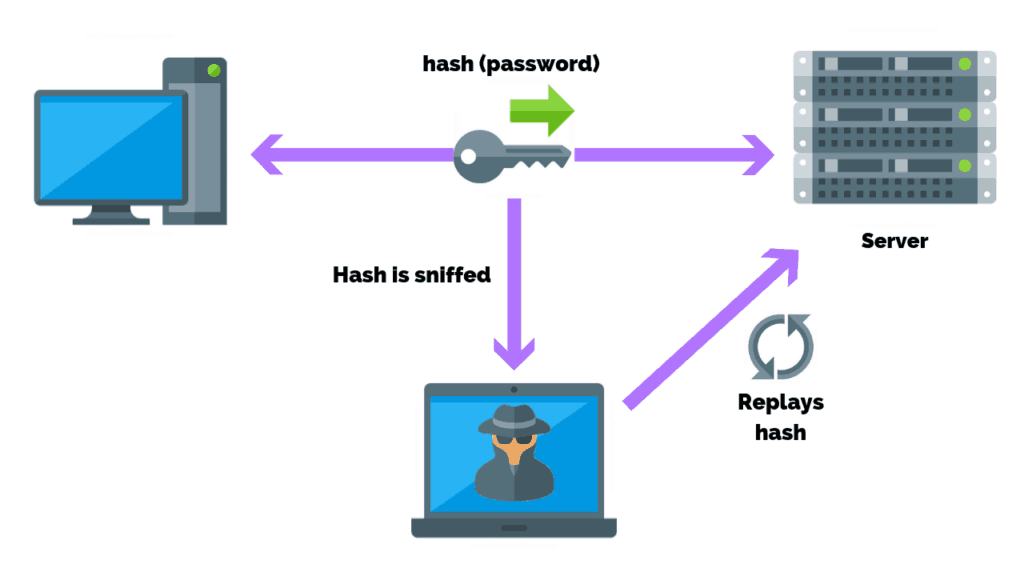
Replay Attacks
A replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants.
The attacker unwittingly deceives the participants into believing they have successfully completed the data transmission. Replay attacks help attackers to gain access to a network, gain information that would not have been easily accessible.
You can prevent a Replay Attack by:
- Creating unique and random session keys between a sender and receiver’s communication.
- Using digital signatures timestamps on all messages.
- Ensuring a password for each transaction that’s only used once and discarded.
- Implementing non-acceptance of duplicated messages.
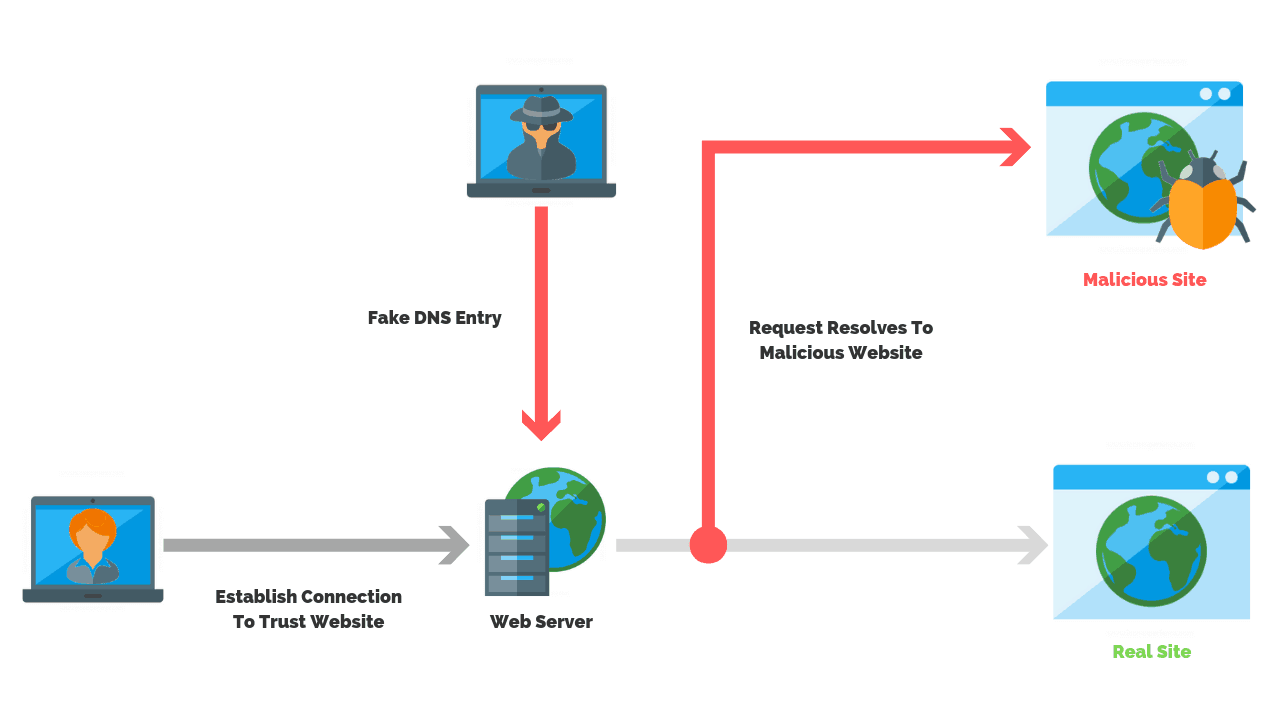
DNS Poisoning
DNS poisoning (also known as DNS cache poisoning or DNS spoofing) is a type of attack which uses security gaps in the Domain Name System (DNS) protocol to redirect internet traffic to malicious websites.
DNS poisoning happens when a malicious actor intervenes in that process and supplies the wrong answer. These types of man in the middle attacks are often called DNS spoofing attacks because the malicious actor is in essence tricking the DNS server into thinking that it has found the authoritative name server, when in fact it hasn’t.
Once it has tricked the browser or application into thinking that it received the right answer to its query, the malicious actor can feed back whatever fake website it wants back to the host device – usually web pages which look like the desired website but actually are there to collect valuable information like passwords, banking information, and the like.
You can prevent DNS Poisoning by:
- Enabling DNSSEC on internal DNS servers.
- Not letting your corporate DNS servers answer Internet DNS queries.
- Paying attention to DNS responses.
- Disabling host file resolution on clients and servers.
- Using DNS forwarders only to verified DNS servers.
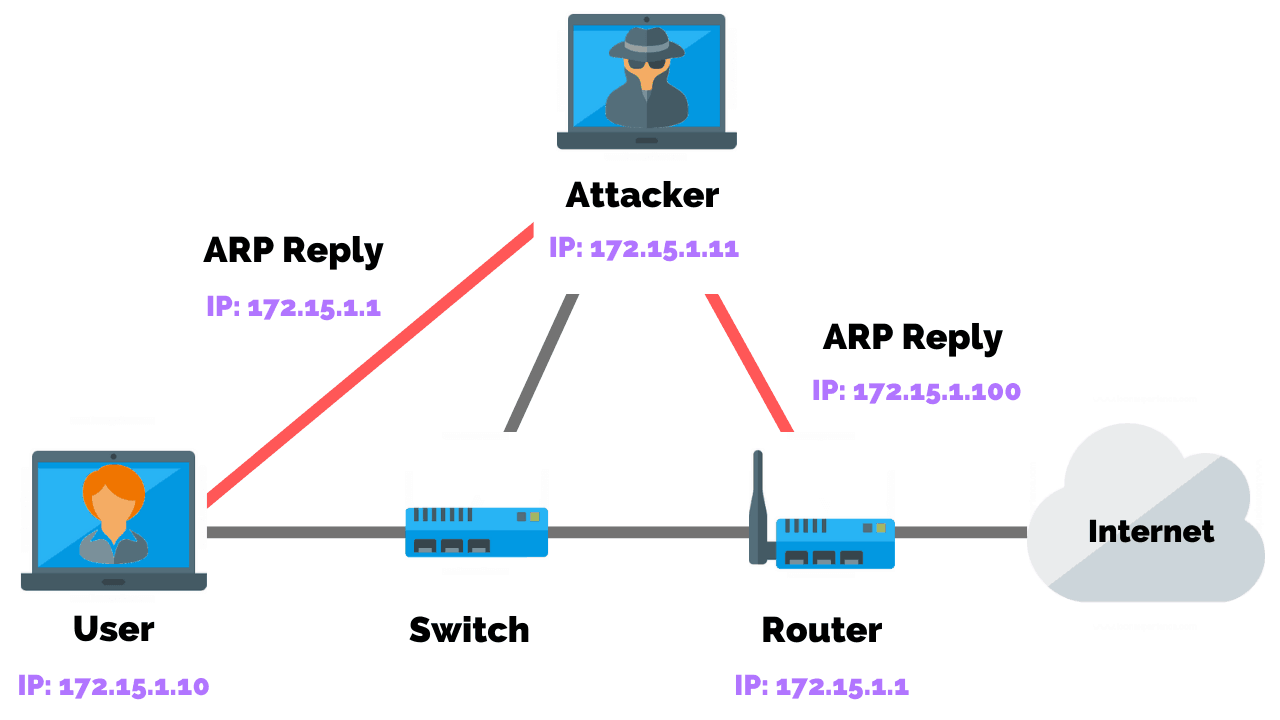
ARP Poisoning
ARP Poisoning (also known as ARP Spoofing) is a type of cyber-attack carried out over a Local Area Network (LAN) that involves sending malicious ARP packets to a default gateway on a LAN in order to change the pairings in its IP to MAC address table. ARP Protocol translates IP addresses into MAC addresses.
The attack consists of an attacker sending a false ARP reply message to the default network gateway, informing it that his or her MAC address should be associated with his or her target’s IP address (and vice-versa, so his or her target’s MAC is now associated with the attacker’s IP address).
Once the default gateway has received this message and broadcasts its changes to all other devices on the network, all of the target’s traffic to any other device on the network travels through the attacker’s computer, allowing the attacker to inspect or modify it before forwarding it to its real destination.
You can prevent ARP Poisoning by:
- Using static ARP entries.
- Implement Encryption on web traffic.
- Implementing VPNs.
- Enabling network firewall to filter out and block malicious packets.
Domain Kiting
Domain kiting is the practice of repeatedly registering and deleting a domain name so that the registrant can, in effect, own the domain name without paying for it.
Domain kiting exploits the five-day add grace period (AGP) in the domain name registration system.
During the first five days after registering, a registrant can delete a given domain name without charge or penalty. ICANN, the organization responsible for the registration system, has proposed abolishment of the grace period as a means of making domain kiting and domain tasting unprofitable for the practitioner.
The main reason for domain kiting is earning extra money from advertisements and marketing methods while not paying any fees for the domain. If the kiting is continuous it is possible that the registration fee for the domain is never paid since the registrar keeps canceling it before the grace period ends; thus, the registrar can earn profit without any costs incurred.
You can prevent Domain Kiting by:
- Staying up to date on ICANN legislation.
- Purchasing domain names only from reputable web hosting vendors.
- Implementing web filtering technology to detect Parked domains.
- Implementing web technology on your browser to detect website reputation.
Typosquatting
Typosquatting, also known as URL hijacking, is a form of cybersquatting (sitting on sites under someone else’s brand or copyright) that targets Internet users who incorrectly type a website address into their web browser (e.g., “Gooogle.com” instead of “Google.com”).
The typo squatted domain owner may redirect traffic to a different URL, show ads, or simply park the domain with the hope that the brand buys the domain from them.
You can Prevent Typosquatting Attacks by:
- Trademarking your domain.
- Purchasing all related URL’s that could be easy misspellings.
- Sending users to third-party from your official website.
- Using an open-source tool like DNS Twist to automatically scan your company’s domain for any typosquatting attacks in progress.
- Checking with your ISP to determine if they offer typosquatting protection as a service offering.
Client-Side Attacks
Client-side attacks require user-interaction usually initiating from a web browser to an internet website. The tactics used to invoke the attack are seamless to the end user, such as, enticing them to click a link, open a document, or somehow download malicious content.
The flow of data is reversed compared to server-side attacks: client-side attacks initiate from the victim who downloads content from the attacker.
You can prevent Client-Side Attacks by:
- Defining permissions for approved third-party vendors you choose to allow to access data – or block from receiving any specific types of data.
- Auditing of new scripts.
- Stopping injection-based attacks like form jacking.
- Enforcing user data sanitization and input validation.
- Comprehensive reporting of site traffic and real-time user activity to identify any suspicious patterns or network requests.
Watering Hole Attacks
A watering hole attack is a targeted attack. It is designed to compromise users within a specific industry or group of users by infecting websites they typically visit and luring them to a malicious site. The end goal is to infect the user’s computer and gain access to their organization’s network.
Watering Hole attacks, also known as strategic website compromise attacks, are limited in scope as they rely on an element of luck. They do however become more effective, when combined with email prompts to lure users to websites.
You can prevent Watering Hole Attacks by:
- Installing web gateways to defend the enterprise against opportunistic drive-by downloads.
- Implementing an email security solution that filters outgoing and inbound email.
- Creating and enforcing a Security Awareness training program.
- Implementing a dynamic malware analysis.
Zero-Day Attacks
If a hacker manages to exploit the vulnerability before software developers can find a fix, that exploit becomes known as a zero-day attack.
Zero-day vulnerabilities can take almost any form because they can manifest as any type of broader software vulnerability. For example, they could take the form of missing data encryption, SQL injection, buffer overflows, missing authorizations, broken algorithms, URL redirects, bugs, or problems with password security.
This makes zero-day vulnerabilities difficult to proactively find—which in some ways is good news because it also means hackers will have a hard time finding them. But it also means it’s difficult to guard against these vulnerabilities effectively.
You can prevent Zero-Day Attacks by:
- Staying informed by joining threat lists from established security organizations.
- Implementing a WAF (Web Application Firewall) to monitor incoming traffic.
- Keeping your systems updated to the latest software and hardware patches.
- Monitoring inbound and outbound traffic for malicious traffic.

Michael Swanagan, CISSP, CISA, CISM
Michael is an IT security expert with 15 years of proven experience. He has experience leading and supporting security projects and initiatives in the healthcare, finance, and advertising industry.
- Explore All Network Attacks
- Denial of Service (DoS)
- Distributed Denial of Service (DDoS)
- Buffer Overflow Attacks
- Ping Attacks
- SYN Flood
- DNS Amplification
- Backdoor
- Spoofing
- Smurf Attack
- TCP/IP Hijacking
- Man In The Middle Attacks
- Replay Attacks
- DNS Poisoning
- ARP Poisoning
- Domain Kiting
- Typosquatting
- Client Side Attacks
- Watering Hole Attacks
- Zero Day Attacks
![]()
Get a fully manged enterprise security solution at an affordable price