Previous

Mantis Botnet: The Largest DDoS Attack Ever Mitigated
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Dušan Trojanović / Last Updated: 7/27/2022
Reviewed By: Dalibor Gašić, & Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
Summary Of The Attack
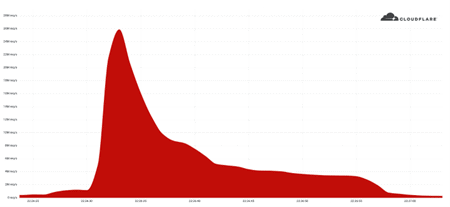
- In June 2022, Cloudflare reported on the largest HTTPS DDoS attack that they have ever mitigated, a 26 million request per second attack which is the largest attack on record.
- Mantis is small, being powered by approximately 5,000 bots, which are compromised of virtual machines and powerful servers giving the botnet much more strength than its size would suggest.
- Mantis is working over HTTPS, which is more expensive in terms of required computational resources because of the higher cost of establishing a secure TLS encrypted connection.
- Cloudflare’s automated DDoS protection system leverages dynamic fingerprinting to detect and mitigate Mantis DDoS attack.
What Happened?
In June 2022, Cloudflare reported on the largest HTTPS DDoS attack that they have ever mitigated, a 26 million request per second attack which is the largest attack on record.
Cloudflare systems automatically detected and mitigated this attack and many more. Since then, Cloudflare has been tracking this botnet, which was called “Mantis”, and the attacks it has launched against almost 1,000 Cloudflare customers.
What Is The Mantis Botnet?
Cloudflare named the botnet that launched the 26M rps (requests per second) DDoS attack “Mantis” as it is also like the Mantis shrimp, small but very powerful.
Mantis is small, being powered by approximately 5,000 bots, but the fact that these are compromised virtual machines and powerful servers gives the botnet much more strength than its size would suggest.
These volumetric attacks aim to generate more traffic than the target can process, causing the victim to exhaust its resources.
While adversaries have traditionally utilized UDP to launch amplification attacks, there has been a shift to newer TCP reflected amplification vectors that make use of middleboxes.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
How Does The Mantis Botnet Work?
The Mantis botnet was able to generate the 26M HTTPS requests per second attack using only 5,000 bots. I’ll repeat that: 26 million HTTPS requests per second using only 5,000 bots.
That’s an average of 5,200 HTTPS rps per bot.
Generating 26M HTTP requests is hard enough to do without the extra overhead of establishing a secure connection, but Mantis did it over HTTPS.
HTTPS DDoS attacks are more expensive in terms of required computational resources because of the higher cost of establishing a secure TLS encrypted connection.
This stands out and highlights the unique strength behind this botnet.
As opposed to “traditional” botnets that are formed of Internet of Things (IoT) devices such as DVRs, CC cameras, or smoke detectors, Mantis uses hijacked virtual machines and powerful servers.
This means that each bot has a lot more computational resources, resulting in this combined thumb-splitting strength.
Mantis is the next evolution of the Meris botnet.
The Meris botnet relied on MikroTik devices, but Mantis has branched out to include a variety of VM platforms and supports running various HTTP proxies to launch attacks.
The name Mantis was chosen to be similar to “Meris” to reflect its origin, and also because this evolution hits hard and fast.
Who Is Impacted By The Mantis Botnet?
Over the past few weeks, Mantis has been especially active in directing its strengths toward almost 1,000 Cloudflare customers.
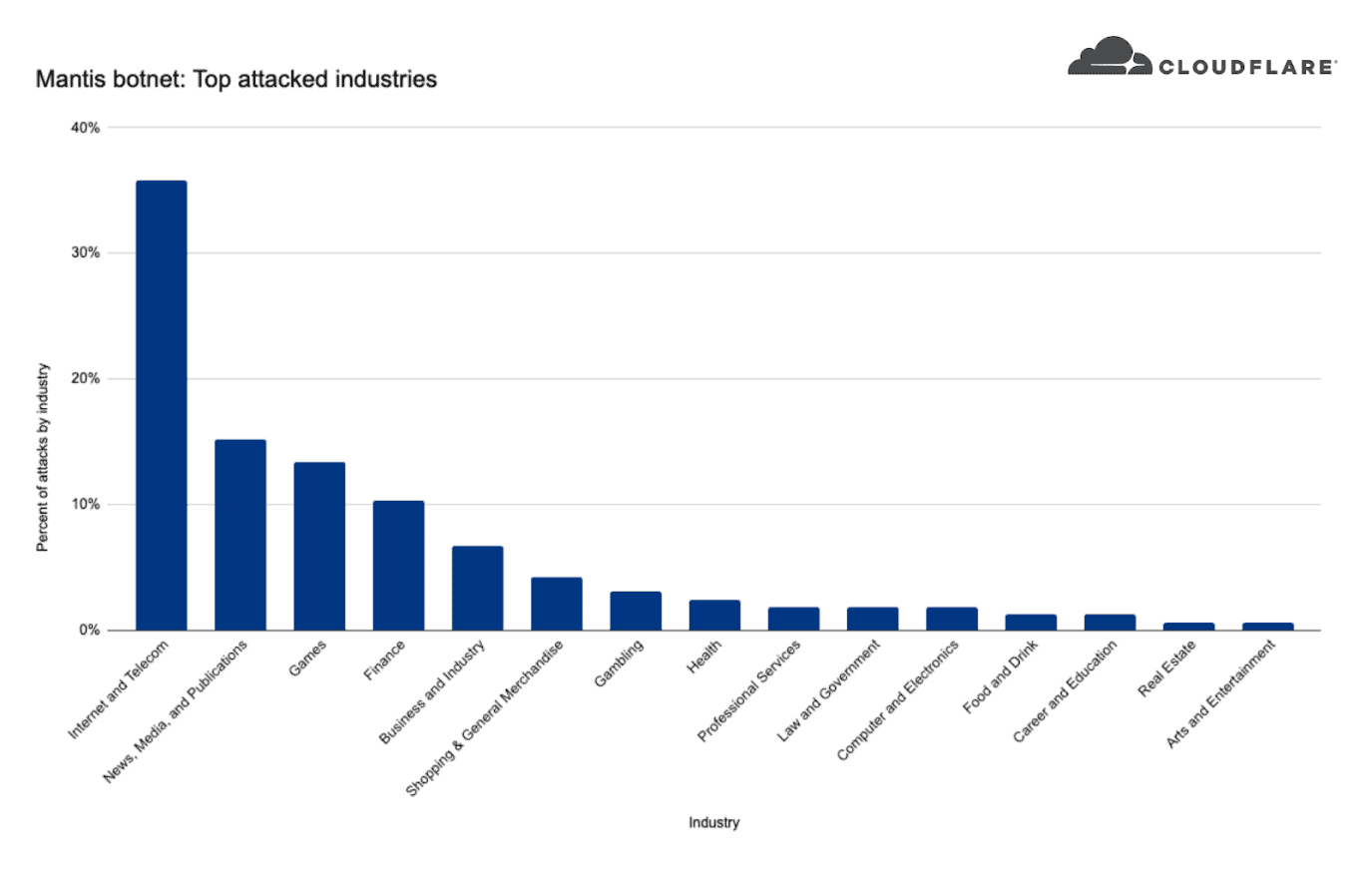
While looking at Mantis’ targets, we can see that the top attacked industry was the Internet & Telecommunications industry with 36% of the attack share.
In second place News, Media & Publishing industry, followed by Gaming and Finance.
When we look at where these companies are located, we can see that over 20% of the DDoS attacks targeted US-based companies, over 15% Russia-based companies, and less than five percent included Turkey, France, Poland, Ukraine, and more.
How To Protect Against Mantis DDoS Attacks
Cloudflare’s automated DDoS protection system leverages dynamic fingerprinting to detect and mitigate DDoS attacks.
The system is exposed to customers as the HTTP DDoS Managed Ruleset.
The ruleset is enabled and applies mitigation actions by default, so if you haven’t made any changes, there is no action for you to take, you are protected.
You can also review Cloudflare guides Best Practices: DoS preventive measures and Responding to DDoS attacks for additional tips and recommendations on how to optimize your Cloudflare configurations.
If you are only using Magic Transit or Spectrum but also operate HTTP applications that are not behind Cloudflare, it is recommended to onboard them to Cloudflare’s WAF/CDN service to benefit from L7 protection.
Related Articles:

Dušan Trojanović
Dušan is a Senior Security Engineer actively working as a penetration tester in DevSecOps projects. He is also an avid security researcher bringing forward analysis on the latest attacks and techniques.
Related Articles
- Top 10 Cyber Attacks In 2022
- Top 10 Vulnerabilities In 2022
- Rackspace Ransomware Attack
- Dropbox Suffers Data Breach
- Iranian APT Uses Log4j
- Google SEO Poisoning Campaign
- Killnet DDoS Target Airports
- Advocate Aurora Health Data Leak
- Microsoft 2.4 TB Data Leak
- Optus Exposes 2.1M Customers
- $570M Binance Coin Hack
- TikTok Denies Cyber Attack
- NATO Data Leak
- Uber’s Systems Compromised
- Cisco Cyber Attack
- Samsung Exposes PII
Popular Articles
Ransomware Attacks
Preventing Attacks



 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO