Previous
Rackspace Ransomware Attack: What You Need To Know
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Eva Georgieva / Last Updated: 12/13/2022
Reviewed By: Dalibor Gašić, & Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
Summary Of The Attack
- On December 2nd, Rackspace Technology noticed that users were experiencing issues while trying to access their Exchange Environment which turned out to be a ransomware attack.
- There are still no indicators that any user sensitive data were stolen.
- Security researchers state that the ransomware attack was due to an unpatched version in the Exchange cluster which allowed the attackers to exploit the ProxyNotShell vulnerability.
What Happened?
On December 2, Rackspace Technology’s customers started experiencing issues while trying to log in into their Exchange environment.
That for Rackspace was an indicator enough to start investigating and after their initial analysis they confirmed a security incident occurred.
A few days later, Rackspace Technology stated that the issue at hand was actually ransomware, which was the reason for the outage that the users were experiencing.

The Rackspace Ransomware Attack Explained
Ransomware is a certain type of malware attack in which the attacker encrypts:
- The data of the target,
- Any sensitive information,
- Important files.
Systems are locked so the victim now has to make a payment to the attacker in order for the attacker to decrypt their data and make it accessible again.
Usually, this type of cyber attack considers any system, network, software vulnerability or any human error as an entry vector in order to infect the victim’s systems or devices.
These devices can be a computer, printer, POS terminal, smartwatch, smartphone, or any other endpoint.
The way ransomware works is through several phases and usually represents a six-stage attack.
- Infection – An entry vector is found, the ransomware is downloaded and it finds its way to the device or system that represents the target.
- Execution – Here the attacker, through the ransomware, detects locations and maps the infected system. There are also some ransomware types that detect and encrypt the backup files and folders also.
- Encryption – Now all the files detected in the previous stage are encrypted and access to them is locked.
- User Notification – The attacker adds an instruction file for ransom payment called a ransom note.
- Payment – The victim should follow the payment instructions in order to regain access back.
- Decryption – After the payment is made, the decryption key is delivered to the victim, but however that might not always be the case.
The Impact Of This Attack
Per the Rackspace Technology statement, the ransomware was an isolated incident that only impacted and took down their Hosted Exchange implementations, their other services they state were left intact such as their email product line and platform.
Having that information, they still state that they couldn’t say at this level of the investigation if any customer or sensitive data were compromised, so currently there is no signs of data theft, however, that is something yet to be confirmed.
However, due to the nature of the attack, phishing attacks and scammers impersonating the Rackspace Support Team are taking advantage of this situation and targeting Rackspace customers.
Rackspace notified their users to stay vigilant, not to give out personal information on phone calls, and to monitor their banking account statements and credit reports for suspicious activity.
Besides that, Rackspace stated that there will be loss of revenue for them for the Hosted Exchange business, which as estimated, generated around $30 million in annual revenue.
How Did The Ransomware Attack On Rackspace Happen?
Although Rackspace has not issued a statement to confirm the source of the attack, cyber security researchers tend to state that it was due to unpatched software.
Particularly, security researcher Kevin Beaumont, in his Medium blog clearly elaborated that the Rackspace’s Exchange Cluster had an old build version number, specifically a version before a patch for ProxyNotShell vulnerability was released.
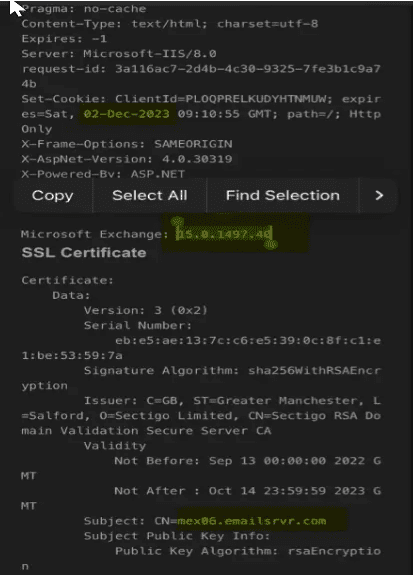
In his research, Mr. Beaumont also stated that if an MSP is running a shared cluster, such as Hosted Exchange, it means that if only one account is compromised for just one customer, it has the potential to compromise the entire hosted cluster.
Although it is not clear that this was the entry vector for the attack, there is still a chance that unpatched software led to Rackspace becoming a victim of ransomware.
How Can This Attack Be Prevented?
Ransomware attack takes several stages and if a good IDS solution is in place, there will be indicators of an attacker moving laterally through the network which would allow the victim, if not previously, to detect the attack while in progress.
Related Article: How To Prevent Ransomware Attacks
Patching the software versions of the different systems is also quite an important aspect and reduces the risk that the attacker will more easily locate an entry vector.
Besides that, network segregation, maintaining backups, and hardening endpoints are just a few of the ways that organizations can prevent falling victim to a ransomware attack.
Related Articles

Eva Georgieva
Eva is a security engineer, researcher, and penetration tester with over 5 years of experience working on both red teams and blue teams.
Recent Attacks
- Top 10 Cyber Attacks In 2022
- Top 10 Vulnerabilities In 2022
- Rackspace Ransomware Attack
- Dropbox Suffers Data Breach
- Iranian APT Uses Log4j
- Google SEO Poisoning Campaign
- Killnet DDoS Target Airports
- Advocate Aurora Health Data Leak
- Microsoft 2.4 TB Data Leak
- Optus Exposes 2.1M Customers
- $570M Binance Coin Hack
- TikTok Denies Cyber Attack
- NATO Data Leak
- Uber’s Systems Compromised
- Cisco Cyber Attack
- Samsung Exposes PII
Popular Articles
Ransomware Attacks
Preventing Attacks






 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO