Previous
Twitter Zero-Day Exposed Data
Of 5.4 Million Accounts
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Eva Georgieva / Last Updated: 8/19/2022
Reviewed By: Dalibor Gašić, & Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
Summary Of The Attack
- Social media platform Twitter suffered a zero-day vulnerability which allowed the attackers access to personal information of 5.4 million accounts.
- The vulnerability was being exploited in December 2021, but reported to Twitter through HackerOne’s bug bounty platform in January 2022.
- The security researcher was awarded $5,040 for his findings.
- The vulnerability allows any party without any authentication to obtain a twitter ID of any user by submitting a phone number/email even though the user has prohibited this action in the privacy settings.
- The vulnerability is now patched and recommended precautionary measures are enabling 2FA and refraining from linking personal information to your twitter account.
What Happened?
Social media platform Twitter confirmed they suffered a now-patched zero-day vulnerability, used to link email addresses and phone numbers to users’ accounts, which allowed attackers to gain access to the personal information of 5.4 million users.
What Is A Zero-Day?
A zero-day vulnerability is a weakness in software that has been discovered by a threat actor but is still unknown to the developer.
It’s called “zero-day” because once a threat actor detects the vulnerability, the software vendor essentially has “zero time” to patch it before it’s exploited.
Zero-day vulnerabilities can stem from software bugs, weak passwords, or lack of authorization and encryption.
How Does The Twitter Zero-Day Attack Work?
The vulnerability allowed anyone to submit an email address or phone number, verify if it was associated with a Twitter account, and retrieve the associated account ID.
More technically, what the security researcher zhirinovsky reported on HackerOne’s bug bounty platform is that this vulnerability allows any party without any authentication to obtain a twitter ID (which is almost equal to getting the username of an account) of any user by submitting a phone number/email even though the user has prohibited this action in the privacy settings.
As he stated, the bug exists due to the process of authorization used in the Android Client of Twitter, specifically in the process of checking the duplication of a Twitter account.
The security researcher reported the vulnerability in January 2022 and the company awarded a $5,040 bounty for his findings.
Prior to that, the attackers created profiles of 5.4 million Twitter users in December 2021 and scraped public information, such as follower counts, screen name, login name, location, profile picture, URL, and other information.
The data was sold on the market for about $30,000.
From Twitter’s statements, this bug resulted from an update to their code in June 2021. When they learned about this, they immediately investigated and fixed it.
At that time, the company had no evidence to suggest someone had taken advantage of the vulnerability.
Scope Of The Threat
The researcher in its report expressed that this is a very serious threat, as people can not only find users who have restricted the ability to be found by email/phone number, but any attacker with a basic knowledge of scripting/coding can enumerate a big part of the Twitter user base unavailable to enumeration prior.
Such bases can be sold to malicious parties for advertising purposes or malicious activities.
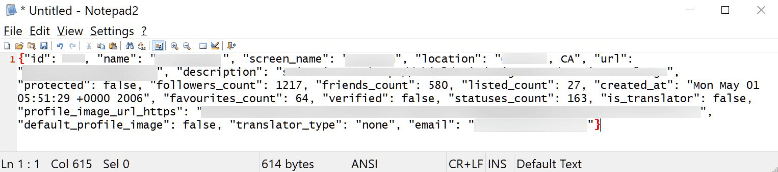
A redacted example of one of the generated Twitter profiles.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
Mitigation Steps Being Taken
In their official statement released on August 5, 2022, the tech giant pointed out that no passwords were exposed, but they encouraged their users to enable two-factor authentication apps or hardware security keys to protect their accounts from unauthorized logins.
And for all the users that operate a pseudonymous Twitter account, they recommended that not adding a publicly known phone number or email address to the Twitter account would be the best point of action in order to keep their identity as veiled as possible.
Lastly, even though most of the data being sold is publicly available, threat actors can use the data exposed in targeted phishing attacks.
Because of that, all Twitter users should be aware when receiving emails from Twitter, especially if the email demands urgency and sensitive information, like asking you to enter login credentials, which users should only be able to do on the official platform.
Related Articles:

Eva Georgieva
Eva is a security engineer, researcher, and penetration tester with experience over 5 years of experience working on both red teams and blue teams.
Related Articles
- Top 10 Cyber Attacks In 2022
- Top 10 Vulnerabilities In 2022
- Rackspace Ransomware Attack
- Dropbox Suffers Data Breach
- Iranian APT Uses Log4j
- Google SEO Poisoning Campaign
- Killnet DDoS Target Airports
- Advocate Aurora Health Data Leak
- Microsoft 2.4 TB Data Leak
- Optus Exposes 2.1M Customers
- $570M Binance Coin Hack
- TikTok Denies Cyber Attack
- NATO Data Leak
- Uber’s Systems Compromised
- Cisco Cyber Attack
- Samsung Exposes PII
Popular Articles
Ransomware Attacks
Prevent Attacks



 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO