Previous

Cloudflare And Twilio Targets Of
A Sophisticated Smishing Attack
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Eva Georgieva / Last Updated: 8/19/2022
Reviewed By: Dalibor Gašić, & Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
Summary Of The Attack
- Twilio and Cloudflare were targets of a sophisticated smishing attack.
- Both companies’ employees phished and credentials were stolen.
- Twilio’s security team also revoked access to the compromised employee accounts to mitigate the attack.
- Cloudflare’s security systems in place stopped the attack from being successful, credentials weren’t enough to allow access to the company’s systems.
What Happened?
Cloudflare revealed on Tuesday, August 9th that they were also targeted by the threat actors who breached Twilio and gained unauthorized access to some of its systems on August 4th.
The threat actor sent phishing text messages to Twilio employees to trick them into entering their credentials on a malicious website.
How Does The Attack Work?
Twillio became aware of unauthorized access to information related to a limited number of Twilio customer accounts through a sophisticated social engineering attack with a goal to steal employee credentials.
The format of the attacks was that the messages informed the recipients that they had expired passwords, schedule changes, and pointed to domains that included the words ‘Twilio’, ‘Okta’ and ‘SSO’.
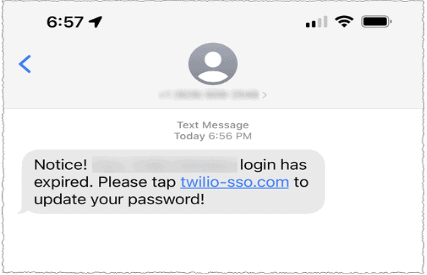
Phishing messages sent to Twilio employees.
The Cloudflare version was that similarly crafted messages were sent to their employees on July 20th.
The company, in their official statement, said that more than 100 SMS messages were sent to its employees and their families.
The messages were pointing to domains that appeared that they belonged to Cloudflare.
Twilio VS Cloudflare Take On The Attack
The threat actors that targeted the companies’ employees managed to fool some employees from both companies into providing their credentials.
Twilio, confirmed that the attackers used the credentials to gain access to some of their internal systems, where they were able to access certain customer data.
From what they stated, they worked with the U.S. carriers to shut down the actos and worked with the hosting providers serving the malicious URLs to shut those accounts down.
Twilio’s security team also revoked access to the compromised employee accounts to mitigate the attack and engaged a leading forensic firm to aid their ongoing investigation.
While Twilio is taking remediation steps, Cloudflare, on the other hand, were able to stop the attack while it was running.
They did state that individual employees did fall for the phishing messages but they were able to thwart the attack through use of their Cloudflare One Products and physical security keys that they issued to every employee that are required to access all of their applications.
Every employee at the company is issued a FIDO2-compliant security key from a vendor like YubiKey.
Since the hard keys are tied to users and implement origin binding, even a sophisticated, real-time phishing operation like this one cannot gather the information necessary to log in to any of the Cloudflare systems.
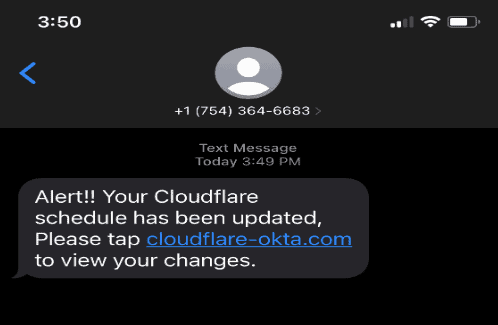
The phishing messages sent to Cloudflare employees.
While the attacker attempted to log in to their systems with the compromised username and password credentials, they could not get past the hard key requirement.
In their official statement, they expressed that no Cloudflare systems were compromised.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
Next Steps
The attacks have not yet been linked to a known threat actor, but Cloudflare has shared some indicators of compromise as well as information on the infrastructure used by the attacker.
Related Articles:

Eva Georgieva
Eva is a security engineer, researcher, and penetration tester with experience over 5 years of experience working on both red teams and blue teams.
Related Articles
- Top 10 Cyber Attacks In 2022
- Top 10 Vulnerabilities In 2022
- Rackspace Ransomware Attack
- Dropbox Suffers Data Breach
- Iranian APT Uses Log4j
- Google SEO Poisoning Campaign
- Killnet DDoS Target Airports
- Advocate Aurora Health Data Leak
- Microsoft 2.4 TB Data Leak
- Optus Exposes 2.1M Customers
- $570M Binance Coin Hack
- TikTok Denies Cyber Attack
- NATO Data Leak
- Uber’s Systems Compromised
- Cisco Cyber Attack
- Samsung Exposes PII
Popular Articles
Ransomware Attacks
Preventing Attacks



 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO