Previous
How The Largest European
DDoS Attack Was Blocked
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Dušan Trojanović / Last Updated: 8/24/2022
Reviewed By: Dalibor Gašić, & Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
Summary Of The Attack
- On July 21, 2022, Akamai detected and mitigated the largest DDoS attack up to this point, which has been launched against a publicly unknown Akamai European customer.
- The attack lasted over 14 hours and traffic was peaking at 853.7 Gbps and 659.6 Mpps which was targeting Akamai European customers.
- The most significant DDoS attack type was UDP flood in which a large number of UDP packets are sent to a target with the aim to overwhelm the target device’s ability to process and respond.
- Chose the proper DDoS solution, identify what assets should be protected, identify what business impact, and define the procedure and dedicated team to respond to the attack.
What Happened?
DDoS (Distributed Denial-of-Service) attacks became a real problem, especially for companies, government institutions, and similar organizational types.
As long there is an active internet connection, the threat of DDoS attacks is always present.
After the largest DDoS attack caused by the Mantis botnet attack in June 2022 mitigated by Cloudflare, on July 21, 2022, Akamai detected and mitigated the largest DDoS attack up to this point, which has been launched against a publicly unknown Akamai European customer.
What Was The Impact?
Akamai detected and mitigated attacks on their Prolexic platform which provides protection against the broad range of DDoS attack types, including their 20 anycast global scrubbing centers and more than 10 TBps of dedicated network capacity.
Within each scrubbing center, proactive mitigation controls drop all detected abnormal traffic in short notice and route legit traffic.
How This Attack Happened
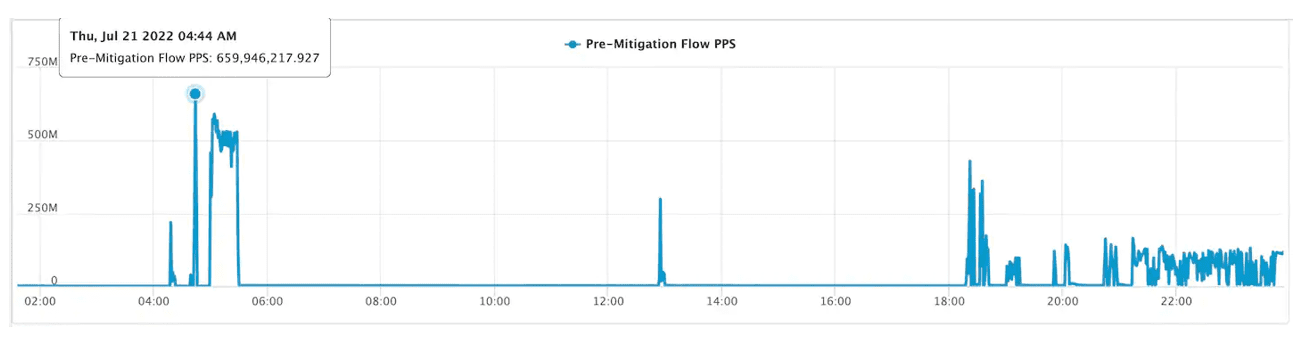
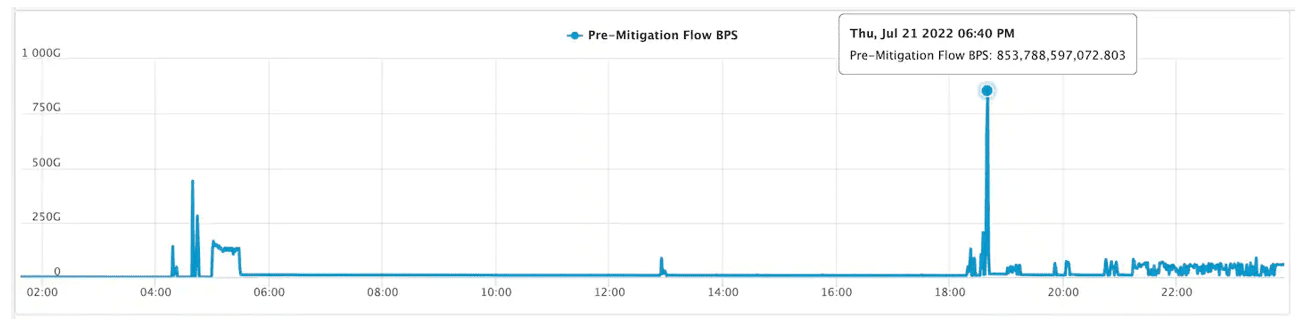
The attack lasted over 14 hours and traffic was peaking at 853.7 Gbps (Gigabit per second) and 659.6 Mpps (Maximum packets per second) which was targeting Akamai European customer large scope of IP addresses which resulted in the largest horizontal attack mitigated on the Prolexic platform.
Akamai revealed that their customer was targeted 75 times in the 30 days time frame including multiple types of attacks.
The most significant DDoS attack type was UDP flood in which a large number of UDP (User Datagram Protocol) packets are sent to a target with the aim to overwhelm the target device’s ability to process and respond. In the following figures, UDP flood was observed in both record spikes.
The first figure represents the maximum number of packets per second was reached 659.6 Mpps during the attack.
The second figure represents the highest attack peak which reached 853.7 Gbps.
Other noticed DDoS attack types were UDP fragmentation, ICMP flood, RESET flood, SYN flood, TCP anomaly, TCP fragment, PSH ACK flood, FIN push flood, and PUSH flood.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
Mitigating DDoS Risk
Today without proper automated DDoS defenses, primarily for critical business operations, it would likely collapse under a similar attack scale, making online business completely inaccessible and causing financial and reputational loss.
Recommendations for mitigating DDoS risk include:
- Chose the proper DDoS solution based on your business scale to keep service up and running.
- Identify what assets should be protected from DDoS attacks, which can include web applications, APIs, DNS servers, origin servers, data centers, and network infrastructure.
- Identify what business impact and operational, financial, regulatory, and reputational costs would incur from loss.
- Design robust architecture by separating data servers on separate networks, and review critical IP subnets to prevent a single point of failure.
- Define procedure and dedicated team to respond to attack on short notice.
- Identify an acceptable time to respond to an attack a do proper mitigation.
- Maintain a DDoS runbook, which allows the organization in case of need to experience a controlled, streamlined response to an attack.
Related Articles:

Dušan Trojanović
Dušan is a Senior Security Engineer actively working as a penetration tester in DevSecOps projects. He is also an avid security researcher bringing forward analysis on the latest attacks and techniques.
Related Articles
- Top 10 Cyber Attacks In 2022
- Top 10 Vulnerabilities In 2022
- Rackspace Ransomware Attack
- Dropbox Suffers Data Breach
- Iranian APT Uses Log4j
- Google SEO Poisoning Campaign
- Killnet DDoS Target Airports
- Advocate Aurora Health Data Leak
- Microsoft 2.4 TB Data Leak
- Optus Exposes 2.1M Customers
- $570M Binance Coin Hack
- TikTok Denies Cyber Attack
- NATO Data Leak
- Uber’s Systems Compromised
- Cisco Cyber Attack
- Samsung Exposes PII
Popular Articles
Ransomware Attacks
Preventing Attacks



 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO